
Virtual Private Networks have become a popular security mechanism for many. There’s no doubt that VPNs are efficient protection methods because of two main factors. First, they hide the IP address of the user. Then, in the same way, they funnel the traffic to go through an encrypted tunnel.
But are we 100% confident in VPNs’ safety? Are these tools a hacker-proof method?
In this article, you’ll find answers to these questions and more. Buckle up as we’ll unveil each mechanism that can vulnerate VPNs. Likewise, you’ll see what to do when faced with a VPN hack.
Quick overview of VPN hacking methods

In the next section, we provide a more in-depth review of the methods hackers use to attack VPNs and the reasons why they work. Meanwhile, here’s a short description of the most common VPN hacking techniques.
- VPN Protocol interventions: This technique consists of attacking the security protocol that a VPN uses to shield users’ data. The success of the attack lies in the strength of the protocol. Most updated security protocols, such as OpenVPN, have proven to be hacking-resistant.
- Cryptographic interventions: As it is known, users’ traffic gets invisible when in the presence of a VPN. To do this, VPNs employ different ciphering techniques. Hackers prey upon outdated encryption ciphers to intrude on the VPN connection and obtain sensitive information.
- DNS, IP, or WebRTC attacks: This method doesn’t involve hacking activities in itself. However, hackers manipulate VPN leaks to obtain exploitable information. VPN leaks can occur because of different factors. It could be a problem with the IPv6 encryption, re-routing of the WebRTC, or deficiencies of additional features like Kill Switch or Split Tunneling.
- Attacking the VPN server network: When attacking a connection is not viable for hackers, they tend to go straight to the server network. Although it is not an easy process, hacking a server is possible. Once the attackers vulnerate the server, they can access history activities, users’ identities, and more.
- Pilfering encryption keys: In the encryption process, VPN users’ data is secured with encryption keys. Depending on the Encryption Key Protocol the VPN uses, hackers could seize the keys and access users’ information.
How can hackers compromise the safety of a VPN – Detailed analysis

Responding to the question, “Can someone hack my VPN?” is difficult if one doesn’t know the functioning of a VPN. With this in mind, let’s recap how a VPN operates.
- After getting a VPN subscription, users can download and install the VPN app. Once done, they can connect to a server.
- A few processes take place before the server connection. First, the VPN shields the user’s data by deploying a connection protocol and an encryption cipher.
The connection protocol hides the user’s IP so that it is anonymous. On the other hand, the encryption cipher encrypts the information and protects it against intruders.

- Subsequently, the server provides the user with a new IP address. The website that the user requests to access will receive this proxy IP.
- The user’s device sends the request to a website that receives the information from the server. Then, the website grants permission for the user to access the content without knowing their identity.
- Upon successfully connecting to the desired website, the user manages to surf the web anonymously and securely.
Now that we know how a VPN functions, there’s only one possible conclusion. VPNs are secure methods to shield private data and circumvent website restrictions. In essence, to compromise the security of a VPN, hackers must interfere with all or some of the processes in the VPNs’ operation.
Here’s an in-depth review of each of the attacking mediums.
1. VPN protocol interventions
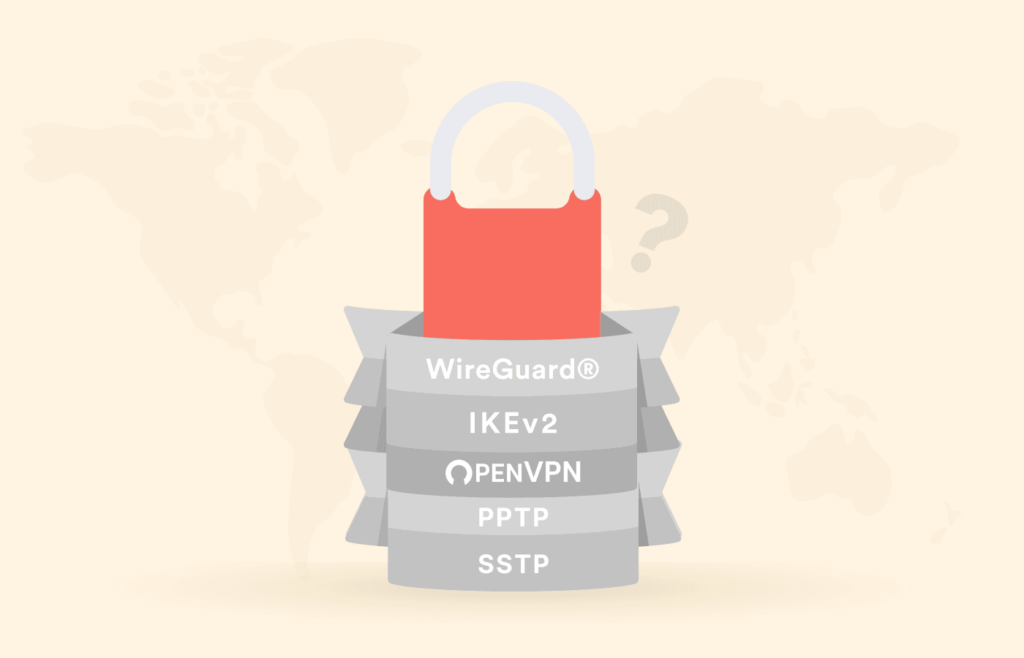
As explained before, VPNs use protocols to function. While some VPN services allow users to choose protocols, most VPNs integrate a default one. It is crucial to understand that protocols evolve rapidly due to the massive adoption of VPNs as a security method. Hence, a VPN protocol can be effortlessly outdated.
Moreover, some protocols are more holistic and less prone to hacker attacks. The following table shows some of the most common VPN protocols and a side-by-side security comparison.
| Outdated/Insecure | Relatively updated/ Secure | Most updated/Secure |
|---|---|---|
| Point-to-Point Protocol (PPTP): Microsoft created this protocol in 1990 for dial-up connections. Due to its antiquity, the PPTP protocol is outmoded. Little to no VPNs use this protocol today as it represents a tremendous hacking risk. | Internet Key Exchange version 2 (IKEv2)/IPSec: This protocol is created by a Cisco/Microsoft collaboration. The system uses the Diffie–Hellman algorithm to exchange keys. IKEv2/IPSec protocol is high-speed, and it works well on a range of devices. Yet, it is close-sourced and vulnerable to MITM attacks when using pre-shared keys. | OpenVPN: Launched in 2000, this one is believed to be the most secure and reliable VPN protocol today. As the name suggests, it’s open source. The protocol is also fast and efficient. Additionally, it uses the Secure Socket Layer protocol. |
| Secure Socket Tunneling Protocol (SSTP): SSTP was introduced by Microsoft in 2000 as a response to the inefficiencies of PPTP. Its key strength is eliminating issues such as blocked access by ISPs or network administrators. Still, the protocol is outdated and susceptible to attacks such as MITM. SSTP is closed-source software. | Wireguard: It is among the fastest open-source protocols because it does not use the “Handshake” for authentication. Wireguard was introduced in 2015, so it’s still relatively new. So far, only a few VPNs have adopted this protocol since it is still relatively new. | |
| Layer 2 Tunneling Protocol (L2TP)/IPSec: The creation of this protocol dates to 2000. It’s a system that combines the best features of PPTP and the Layer 2 Forwarding (L2F) Protocol from Cisco. While more effective than the PPTP or SSTP, L2TP is still vulnerable to MITM attacks. Also, it shares data with the NSA. | SoftEther: Another newborn protocol, SoftEther, was created in 2014. This protocol’s efficiency lies in its being based on the TCP/IP protocol. It’s a fast protocol that facilitates bypassing restrictions. Yet, it requires manual configurations. |
Final verdict: Hackers can exploit the vulnerabilities in the VPN protocols that a VPN service uses to function. Nevertheless, there are secure options such as OpenVPN to avoid this. If you want to be free of VPN protocol interventions, it is best to go for a VPN service that uses OpenVPN.
2. Deploying cryptographic intervention
When you use a VPN, your traffic goes through encryption to make it invisible to ISPs and third parties. In this encryption process, the VPN uses an encryption cipher with a hash authentication to make data “illegible.” In a nutshell, the cipher is just an algorithm that ciphers or deciphers data per request.
At present, two of the most common ciphers are AES and ChaCha20. In the same way, another one is Blowfish, although it’s not that common.
The length of the keys that the encryption cipher creates directly relates to the security it can provide. This is because shorter keys are easier to decrypt by savvy hackers. For instance, AES is one of the safest protocols existing, but AES-256 is safer than the same protocol with 128 bits.
As with most technologies, archaic ciphers and hashes make it easier for hackers to step in. For example, due to vulnerabilities in the Blowfish cipher, the protocol is more susceptible to “birthday attacks.” Similarly, SHA-1 hash cryptography is vulnerable to deciphering techniques.
Final verdict: Deploying cryptography is one of the safest methods to shield data. Yet, there are different techniques hackers can use to decipher the information. Despite not being impossible, it’s quite complicated to decrypt the information of robust systems such as AES-256. Overall going for a 256-bit encryption system, such as AES or ChaCha20, would keep data safe from hackers.
3. DNS, IP, or WebRTC exposures
In some cases, VPNs may leave your data without protection. In the VPN jargon, this is called a VPN leak. Most of the time, this occurs by accident. For example, when a VPN function doesn’t operate the right way.
The IP of a user could be compromised if the IPv6 request is not encrypted or if the WebRTC is not rerouted. Also, the user’s web activity could be visible if the ISP handles DNS requests. And the same applies to Kill Switch errors.
As such, this is not a hacking method since hackers don’t need to intervene in the VPN to get the information. Technically, the only thing they need to do is monitor the VPN activity and be on the look for VPN leaks.
To avoid this, most VPNs today integrate anti-leak protection.
Final verdict: For users experiencing VPN leaks, private data may be in danger. Yet, VPN leaks should be an easy-to-solve problem if a user goes for a VPN service that integrates a default anti-leak function, such as a kill switch.
4. Attacking the VPN server network
Hackers tend to go directly to the VPN server if they can’t breach VPN connections. Sadly, VPN servers might have poor access passwords or be misconfigured, making them an easy target.
Users’ private information, history, and any upcoming behavior when connected to the server might be accessible if an attacker manages to get into the server.
As an illustration, a third-party mistake caused a compromise on one of NordVPN’s servers in 2018. Because of this, hackers could scrutinize which users were logged into the server that had been compromised, as well as the websites they were viewing.
Similarly, SuperVPN, ChatVPN, and GeckoVPN were all compromised in 2021. Hence, nearly 21 million identities, emails, addresses, and payment details were popular domains.
Final verdict: If you select a high-end VPN provider with a track record of independent security audits, the likelihood that your VPN server will be compromised greatly diminishes. Use a VPN with RAM-only servers for even more assurance to stop your data from ever being written to the hard disk.
5. Pilfering encryption keys
Hackers can access your VPN connection and read all incoming and outgoing traffic if they get their hands on the encryption keys used to protect your data.
Thankfully, most top-tier VPNs utilize Perfect Forward Secrecy (PFS) by default, and most VPN software wraps its encryption keys.
PFS is a protocol feature that guarantees the VPN server and the client always utilize distinct symmetric keys. These keys aren’t shared during the connection. Each session generates a new key, rendering the prior one useless.
Final verdict: A single compromised encryption key no longer poses the risk of exposing all of your VPN sessions. The Perfect Forward Secrecy removes this. Thanks to temporary keys, hackers could never reveal more than a particular session.
Big VPN hacking incidents

Most users disregard the potential risks of hacking activities due to unawareness. However, when you think of some of the most significant hacking incidents, it’s easy to realize the magnitude of the problem. The following are three VPN hacking incidents that left their mark on the cybersecurity discussion topic.
1. Pulse Secure VPN hacking
Opening the list is no other than the Pulse Secure VPN hack scandal. In 2021, the cybersecurity firm FireEye discovered a vulnerability in the Pulse Secure VPN.
In their disclosure, the firm stated the vulnerability was “exploited by suspected China-linked Hackers.” The repercussions of the hacking were monumental. Five different US agencies were intruded on with 12 families of malicious software. As a result, the CISA had no other option than to call for a federal agency emergency.
The hacking was attributed to second-rate login processes in the VPN.
2. The hacking of the Android VPNs
Another colossal hacking incident is the one that suffered Android VPNs. Back in early 2021, GeckoVPN, SuperVPN, and ChatVPN were intruded on by hackers who obtained the personal information of nearly 21 million Android users.
It may be intriguing for some people to discover the hack of the info of 21 million users knowing VPNs are so-called safe mechanisms. Yet, it was pretty simple for cyber attackers to snoop in the systems of these VPNs.
Why? Well, all of these previously-mentioned services are for-free Android applications. While free VPNs may enable users to circumvent geo-restrictions, they cannot provide safety.
For example, for-free VPNs do not tunnel traffic. On top of that, they log users’ data and exchange it with third parties. Some of which may be malicious actors.
In this case, hackers could access the data hassle-free since the databases’ credentials were the default ones. As such, after obtaining personal info, like login credentials, country, full name, device, and others. Hackers went to a renowned hacker forum and sold the data to the highest bidder.
3. The hacking of NordVPN
In March 2018, the cybersecurity world was caught off guard (literally) by the NordVPN hack. One can expect a free VPN hack without further surprise, but the hacking of a private VPN like NordVPN was a shocker.
Not only hackers managed to sneak into a NordVPN server, but they went unnoticed for 30+ days. The security breach occurred after an undisclosed far-flung administration system was left unsupervised. As a result, intruders had access to all the traffic on the server for a whole month.
Moreover, they deciphered the information and rerouted the connections while NordVPN’s administrators were oblivious. Although this event shows how hard it is to sustain security at all levels, NordVPN was found negligent by experts.
Overall the three hacks are irrefutable proof that VPN malpractice can have severe consequences. The repercussions are endless, be it frail database shielding, poor authentication systems, or misconfigured servers.
The solution? A rigid VPN service with top-notch security features.
What to expect when faced with a VPN hack?

As seen before, there are several possibilities when faced with a VPN hack. While this will depend on the attacker and the security breach, users can expect the following three actions.
Scrutiny
When experiencing a VPN connection hack, either by breakable encryption ciphers or encryption keys’ hacking, scrutiny is the first thing you would assume. Your data will be at the mercy of third parties like the government, the ISP, or other malicious stakeholders.
Likewise, in the case of server intrusion on a pro-log VPN, the attacker could access the all-time activity on that server.
Data Exposure
In the event of database hacks, all personal information will be visible to hackers. This includes email, passwords, bank account details, IP addresses, and more. Hackers often sell this information to third parties on the dark web or even blackmail the owners in exchange for money.
Additionally, if the attackers manage to intrude on the servers of a pro-log VPN, they can access the browsing history, location, ISP, and more.
Cyberattacks
Hacking does not always involve cyberattacks. Sometimes it only takes hackers to intrude on a connection or a server to obtain valuable information. However, if cyberattackers manage to access a VPN server, they can reroute the traffic to a fake website.
Most of the time, these websites contain fraudulent logins that trick the user into providing sensitive information. In cybersecurity jargon, this is called a Man-In-The-Middle attack (MITM attack).
How to proceed before VPN hacking?

Using a top-notch VPN service poses zero to no cybersecurity risk. Nevertheless, if you have used a for-free VPN or a low-grade private VPN, chances are you can experience a hack.
Even though the best piece of advice is to use a top-of-the-art VPN, these recommendations are helpful.
- Stop using that service as soon as possible.
- Remove the VPN application from all your devices.
- Check your browser, devices, and routers. Then delete the VPN extension and reboot the systems.
- Revise your personal information and modify it conveniently.
What – in reality – is the protection scope of a VPN?

It’s common knowledge how VPNs enhance cybersecurity by protecting users against numerous threats. Yet, sometimes it’s not clear what is, in reality, the protection scope of a VPN.
The following scenarios are examples of when a VPN can protect you.
- When the ISP tries to snoop on your browsing activities: VPNs encrypt your traffic so that it’s invisible to ISPs and other third parties.
- When a hacker wants to deploy a MITM attack: When hackers know your internet activity, they can reroute your traffic to a fake website to collect sensitive information. Since VPNs encrypt traffic, MITM attacks are unlikely because hackers can’t see your browsing history.
- When a third party wants to monitor your network: Because of the encrypted tunnel, it’s impossible for an external to watch your network’s activity when using a VPN.
Disclaimer: Other than the previous protection cases, VPNs are somewhat helpless. For instance, most VPN services can’t provide users with anti-malware/phishing or with protection against local attacks.
Out-of-limit scenarios for VPN protection

Despite having a VPN hacked as a possibility, there are some cases in which a hacker attack isn’t needed for a VPN not to work. Some circumstances simply fall out of the limits of a VPN.
The following are scenarios in which VPNs offer zero to no protection anyhow.
External website breaching
Cyberattackers can hack an external website and access its database. If they happen to hack a website you visit often, your information may be at risk.
While VPNs protect your actual IP address from being revealed, any other critical information shared with that website would be accessible to hackers. Some data at stake include credentials, such as email and password, contact info, and more.
Device infection
The internet is jam-packed with potentially harmful websites and software that contain malware and viruses. Interacting with some of these malicious elements poses a colossal risk of device infection.
In such an event, hackers can intrude on your device and remotely deploy actions, such as recording your screen, using your applications, and more. In this case, VPNs won’t prohibit hackers from manipulating your device.
Malicious Software Installation
Downloading programs from unverified sources can lead to mute virus installation. Likewise, another potential threat lies within some browser extensions that might jeopardize the security of your device.
At last, hardware like flash memory cards, USB, and cables may contain malicious software. VPNs are reasonably helpless in such cases.
Malicious link clicking
A popular scam technique that VPNs can’t protect against has to do with malicious links. Phishing attacks and other social scams are often out of the limits of a VPN service.
Though some VPNs offer antimalware protection, it’s not a typical feature. It’s worth considering this kind of protection against malicious URLs increases the price. Further, it’s not always efficacious.
Network-connected Device Infection
Hackers may also attempt to vulnerate your apparatus when sharing a network connection with an infected device. The most common technique would be an Address Resolution Protocol (ARP) spoofing attack. This hack fools a target device’s user into communicating with the hacker rather than the intended receiver.
Although the VPN protection, in this case, will depend on the configuration of the network, in most cases, VPNs can’t avoid these attacks.
Criteria for choosing the finest anti-hacker VPN service

At this point, it is evident VPNs aren’t 100% hack-free methods. Yet, they can make hacking activities improbable. Depending on the robustness of your VPN service, you will be more or less prone to receive a cyberattack.
Here it’s a list of all the desirable VPN features for anti-hacker protection.
- Internal security inspection
- Bug bounty program
- Tenacious encryption cipher
- Diskless servers
- Kill Switch function
- Anti-leak capabilities
- Strict no-logs policy
- Perfect Forward Secrecy usage
- Durable and secure protocols
Cybersecurity tips for extra protection
Using a VPN furnishes 95+ percent of the security necessary to protect against cyber attackers. Now, what about the remaining 5 percent?

Netizens, most of the time, rely on external tools to protect their privacy and security. Yet, there are a few practices we can carry on as users to trivialize the risks.
Even in the case of a VPN hack, the following self-protection techniques can help you put hackers on a quest.
1. Create robust passwords and use an authenticator app
It’s all about making it hard for hackers to try and decipher our passwords. One of the most common mistakes is that users create weak passwords and use them multiple times. Like this, it only takes for attackers to access one account to have access to all of them.
Using a password manager is one of the safest alternatives today. With this software, you can create strong passwords, stock your credentials, and delete them at your convenience.
On top of this, for further protection, you can use an authenticator app. With a multi-factor authentication system, each login attempt is secure. It doesn’t matter if a hacker manages to decipher your password. Without authentication, it will be useless.
2. Activate your alerts and keep up to date
Users often deactivate email or native notifications associated with login attempts. Yet, this is a powerful mechanism to keep informed of potential hacking activity. Set notifications in any of your devices to remain alert before attacks.
Not only that but keep alert in general.
As technology evolves, cybersecurity best practices arise. Set notifications on your phone or preferred device to receive news alerts. Like this, you will be in the know whenever any of your privacy and security services have an important update.
3. Get antimalware protection
As we know, VPNs’ security falls short faced with malicious software infection. Sometimes, when hackers find it challenging to vulnerate a VPN, they go for more accessible means. In short, social engineering attacks, such as fishing.
Getting antimalware/antivirus software is the safest path for avoiding or attempting to overturn malicious interactions. However, for further protection, ensure downloading content only from trusted sources. Likewise, avoid opening pop-ups or downloading attachments from unknown senders.
4. Rely on the power of encryption
Encryption is a powerful method to encode vital data, such as your online activity or personal information. When passing data through encryption, users reduce the chances of data leaking.
VPNs encrypt online activity in general. Yet, users can take it further. Numerous services encrypt not only your online activities but also your communications.
5. Keep your applications updated
Having an outdated application enhances the possibility of suffering a hack. Software is often on the look for bugs and security errors to fix in newer versions. As a result, if you confirm to have the most recent version of all your apps, your security will be less vulnerable.
Additionally, you can set your device to update your applications automatically.
Top three VPNs in our detailed list
Preventing a VPN hack can be challenging. Not all VPN services offer dependable features that shield your privacy and protect your security at all costs. Considering our criteria for choosing the finest anti-hacker VPN service, here are our top three VPNs.
1. NordVPN
Despite the hacking history of this service, it’s safe to say NordVPN has learned its lesson. It uses OpenVPN and IKEv2/IPsec protocols, two of today’s safest protocols.
Moreover, it uses 256-bit encryption and integrates with antimalware and ad-blocking capabilities.
2. ExpressVPN
This service has trustworthy VPN protocols (such as OpenVPN) and the safest encryption system (AES-256). Additionally, it integrates a Kill-Switch button to offer protection in the event of sudden disconnections and anti-leak capabilities.
3. Private Internet Access (PIA)

This VPN service uses a combination of VPN protocols, such as OpenVPN, L2TP/IPSec, and more. In the same way, it offers encryption ciphers like AES-128 and AES-256. It’s open-source, and it integrates Kill Switch and ad-blocking capabilities.
FAQs
Overall, utilizing financial services while connected to a VPN is safe. However, it will depend – in the end – on the robustness of the VPN itself. Ensure to select a top-notch VPN service like ExpressVPN. This provider offers the best encryption system (AES-256), the most rigid VPN protocol (OpenVPN), and extra capabilities like a kill switch and anti-leak protection.
Absolutely not! The Incognito Mode is an alternate option to visit a website without storing your cookies, browsing history, or the responses to a form. Yet, the information is visible to your ISP or your organization. If something, private browsing avoids being targeted by companies as a result of your search activity. It would be uncomplicated for a tech-savvy person to check your activity if you only use private browsing as a security tool. On the other hand, it would be a piece of cake for hackers.
Of course! Firstly, free VPNs don’t count on rigid VPN protocols, so it’s easy for hackers to get into the servers, obtain the credentials, and more. Second, free VPNs don’t have cutting-edge encryption ciphers, so all your data is at the mercy of intruders. Moreover, free VPNs log your activity and exchange it with third parties. Consequently, your privacy and security are at stake, even if you don’t experience a VPN hack. The list is endless, but using a free VPN is not a favorable decision overall.
Yes! Your traffic goes through an encryption tunnel when using a VPN service. As a result, your data is invisible to the ISP or third parties.
Technically speaking, all types of devices are hackable. Yes, you can experience a VPN hack using your mobile. Yet, the chances decrease enormously if you get the protection of a top-class VPN.



