One of the World Wide Web’s biggest mysteries is that, despite its unimaginably large size, we walk around with it in our hands. This massive size generally splits into three layers: the surface, deep, and dark web. You only need a search engine such as Google to access the surface, but the situation is very different for the deep web.
Despite the internet’s massive size, only about 10% is the surface web. The remaining 90% of it constitutes the deep web and the dark web.
You might start wondering, “What is the surface web?” “What is the deep web?” and “What is the dark web?” Continue reading below to learn about the deep web and how to access it for free in 2024.
Comparing the Deep Web vs. Dark Web: what are the major differences?
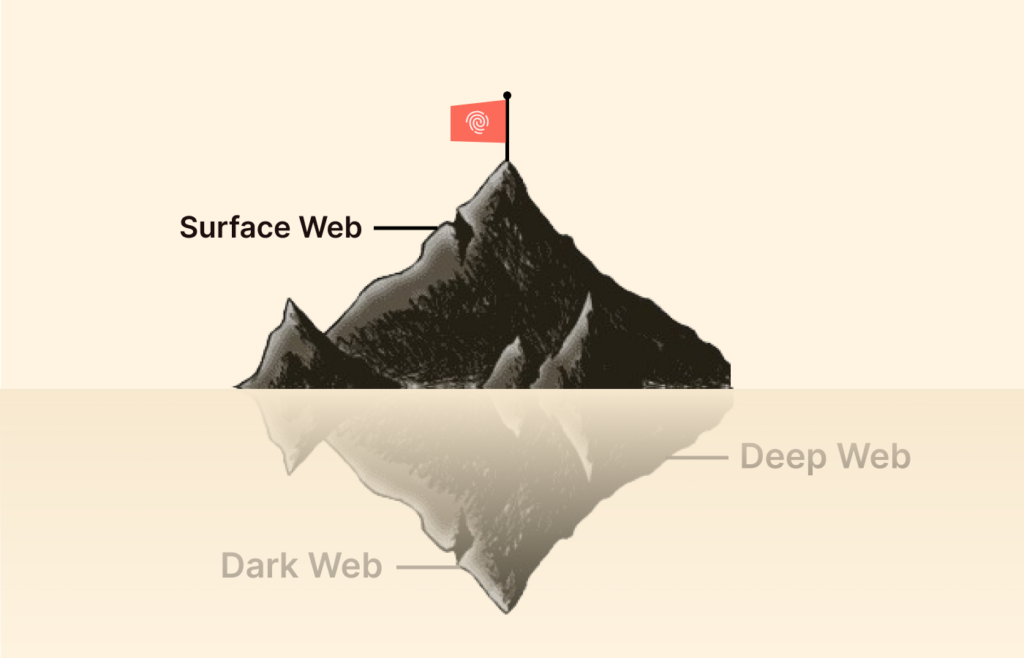
There’s a need to clearly distinguish between the deep and dark web, as most people use them interchangeably.
The deep web means every section of the internet is inaccessible by regular search engines. In contrast, the dark web refers to a part of the internet that runs on overlay networks and requires specific browsers, networks, or authorization. Technically, this means the dark web is under the deep web.
The table below shows the outstanding differences between the deep web and the dark web:
| Feature | The deep web | The dark web |
|---|---|---|
| Definition | Web pages that you can’t find in the indexes of search engines and standard web programs | A subset of the deep web that requires specific browsers, configurations, or authorizations and runs on overlay networks |
| Accessibility | Usually, you can access web pages on the deep web using regular browsers as long as you have the required credentials. | Knowing the URL of the webpage you want to visit is important because you can’t find it using search engines. |
| Search engine discoverability | Web pages on the deep web don’t show up on search engine result pages due to their privacy. | You need specialized dark web browsers like Tor and Freenet to view web pages on the dark web. |
| Examples | Your email messages, Google Drive files, and WhatsApp messages are all examples of the deep web. | Webpages you’ll find on the dark web include black markets, dark web search engines, illegal file-sharing websites, and dark web versions of news websites. |
Is the Silk Road still working?
For the early users of the dark web, the term “Silk Road” should ring a bell, although negative. Silk Road is an online black market and one of the earliest darknet e-commerce sites. Silk Road no longer exists, but even if it did, we’d advise you to steer completely away from it.
While operational, the Silk Road was the hub for various illegal transactions. Since the site ran on Tor, which granted a high level of anonymity, users could trade weapons, hard drugs, and other illegal substances. Payments were primarily in bitcoins, further contributing to the site’s safety and security.
However, no level of anonymity or security is safe when the government is serious about locating you, not even with a VPN. The Silk Road founder was eventually apprehended and put behind bars for life without the possibility of parole. While similar websites like Silk Road have tried to surface, the government’s doubled effort on cracking them down has made that unsuccessful for the most part.
What if I want to access the Deep Web?
Accessing the deep web is quite straightforward, provided you know where you’re going and have the key (your credentials) to gain entry. Most web pages on the deep web are still accessible by regular search engines via browsers like Google Chrome, Microsoft Edge, and Mozilla Firefox.
Take your email, for instance. Open the web browser and type the URL into the search bar. Once the website opens, you’ll see a bar where you can type in your email address and then your password. If you have set up multifactor authentication on your email address, you’ll need to verify from your other device that it is you trying to log in. After that, you can start accessing your private section of the internet.
How big is the Deep Web?
The internet is, without a doubt, one of humanity’s greatest inventions. It’s the ultimate wonder of the vast amount of data that we’ve been able to collect about ourselves, about our world, and about ideas or concepts we’re even yet to explore.
In 2020, the internet’s data hit 64 million zettabytes. A zettabyte is about a billion terabytes. For context, most of today’s advanced computers still come with a storage space of 1 terabyte. That means to fix every piece of information we have on the internet today on computers, you’ll have to stack an endless amount of computers side by side.
Earlier, we explained that the deep web is 400 times bigger than the surface web, but most people may not understand how big that is. The world’s most popular search engine, Google, has over 50 billion web pages in its index. The exact value is unknown, and estimates often suggest a figure of around 100 trillion.
So, how big can the deep web be if it’s 400 times larger than the surface web? We’ll respond with the following statistics:
- Globally, there are over 4.9 billion social media users, representing over 60% of the global population. While some of the activities on these apps are public, most of them, like photo sharing and messaging, are private.
- Email clients like Gmail and Outlook process over 347.3 billion emails daily. Every one of your emails falls under the deep web aspect of the internet.
- Google Drive and Dropbox have more than 2.7 billion users combined, each uploading multiple files of various sizes.
The Deep Web is dangerous: Myth or fact?

For most people, the deep web is the underworld of the internet. Despite the deep web’s bad reputation and terrible PR, it’s not inherently more dangerous than the surface web. Plus, people often confuse the deep web with the dark web, negatively impacting how most perceive it.
There are dangerous websites on the deep web the same way you have best-to-avoid websites on the surface web. Similarly, the deep web also has countless websites that are safe to view.
Most times, when you hear of a terrible incident on the deep web, it’ll most likely relate to hacking or stealing personal information. As these are becoming increasingly more common, here’s a look at recent massive hacks:
- In August 2022, hackers targeted Twitter (now X) via a zero-day vulnerability that allowed attackers to access the personal information of 5.4 million accounts. The hackers offered these accounts for sale for $30,000 and later, in November, made them available for free.
- In September 2022, multibillion-dollar gaming company Rockstar suffered a massive data breach that resulted in the leak of its in-development and widely-anticipated game, GTA 6. Actual footage of the video game later emerged and is similar to what the cybercriminal shared.
- T-Mobile suffered its second data breach of 2023 after a hack revealed the PINs, full names, and phone numbers of over 800 customers. In the first data breach of the year, a malicious actor gained access to their systems last November. He stole personal information – including names, emails, and birthdays – from over 37 million customers.
Exploring how the deep web works

For a web page to be on the surface of the web, such as on Google search engine result pages, a web crawler must first crawl and index it. This process is completely discretionary. That means you decide whether you want any search engine bot to crawl your webpage.
How search engine result pages present the required information
For a better understanding, here’s a detailed analysis of how surface web crawling and search engines work:
- You post content online: Voice, video, or visual content. At this point, you submit a sitemap to tell Google that your website is available for crawling.
- A web crawler analyzes your content: Web crawlers use many names, including spiders, spider bots, or crawlers. They analyze your web page for the main information passed on and do that for numerous other web pages.
- Search engines index the crawler’s findings: Once the crawling process is complete, the search engine adds your webpage to its catalog or index.
- Search engines serve users information they find: Whenever a user searches for information related to what the search engine has indexed, it delivers it.
Why deep web content is hidden
Remember that the crawling process is discretionary. If you own a website and don’t want Google to crawl it, you only have to ensure you do not send a sitemap to Google. This is exactly what operators of web pages on the deep web do: purposely hide their content from search engines and crawlers’ reach.
This is necessary due to the kinds of information that you’ll find on the deep web. You don’t want to wake up one morning to find that the credit card details you stored on a Fintech company’s website are now on the first page of Google. From this, you can deduce that privacy and security are two of the greatest reasons for having content on the deep web rather than on the surface web.
Sometimes, people also hide content from the surface web to protect copyright. For example, the Social Science Research Network has over 1 million academic papers uploaded. However, due to the intellectual nature of the papers, you need to create an account to access them.
How to access the dark web using Tor

Tor is short for “The Onion Router,” and it’s one of the easiest ways to access the dark web. It’s a network of over 7,000 volunteer computers that work together to conceal a user’s activity and make it difficult to determine what they’re doing online. Most dark web pages are onion websites, which are not accessible by all browsers but only to a select few.
Tor browser and Brave can conveniently access the network due to supporting the Tor protocol. You can also use Chrome and Firefox, although you may need to download a separate plugin first. For this guide, we’ll only be focusing on the Tor browser.
Here’s how to start accessing the dark web on your computer:
1. Download the Tor browser for your OS.
Simply visit the Tor project’s network’s website and download the browser’s version for your operating system. Currently, Tor is available on Windows, Mac, Linux, and Android. There’s also an unofficial version for iOS devices, but it has limited functionalities. With the app downloaded, open and install it by clicking on the. EXE file.
2. Connect to the Tor network.
When you open the browser, you can configure it to adjust network settings or connect directly. Like most users, you can skip configurations entirely and just connect directly.
3. Enter the deep web address you want to visit.
Tor’s interface has the design of a traditional browser, making it easy to interact with and understand. While DuckDuckGo has made traditional web searching possible on Tor, its results don’t show dark web pages. To access those, you still need to know the URL of the website and enter it in the address bar of the Tor browser.
How can you stay safe on the Deep Web?

Your safety and privacy should be your topmost priority whenever you visit the deep web. Here are safety steps we recommend following whenever you’re on the deep web:
1. Install premium antivirus software on your phone
When it comes to antiviruses, you have a long list of options from which you can choose. However, before you make a selection, the three main areas to consider are performance or reliability, pricing, and ease of use.
Antivirus software protects you from malware, spyware, and other computer viruses rampant throughout the deep and dark web. When you activate the software, it actively scans any files your device saves from the internet before they get saved onto your phone.
If the antivirus confirms that a file poses any danger to your device, it warns you. High-quality antivirus programs regularly scan your device to ensure malware, spyware, Trojan horses, or other malicious software haven’t compromised it.
2. Use a high-quality VPN service
Next to antivirus software, find and select a quality VPN for surfing the deep web. Virtual Private Networks (VPNs) keep you safe when surfing the internet in various ways. The most obvious way is by hiding your computer’s IP address and assigning you a new one, usually a different region.
VPNs keep you safe in other ways, including preventing IP address leaks and using confirmed no logs that clear your online and browsing data. High-quality VPNs now feature obscure servers for stealth operations and superfast and secure protocols like OpenVPN and WireGuard.
In short, using a VPN makes it difficult for anyone to determine who you are or where you’re browsing from. Below, you’ll find a list of the best VPNs you can trust for your privacy.
1. NordVPN

It is one of the most reliable options for streaming or downloading content. Its ultra-fast and secure servers provide smooth browsing on deep webs.
Pros
- Multiple high-speed servers
- Effective and efficient customer service
- Wide range of global servers
Cons
- Poorly optimized mobile apps
Already a household name in the VPN market, its developers keep upgrading it with new features to keep it ahead of its competitors. One of the most trusted VPNs for the deep web and the dark web security, it effectively blocks malware, ads, web trackers, and other online threats. Conventionally, Nord also doesn’t log your data and uses AES 256 encryption.
NordVPN allows you to create your private encrypted network for safe file sharing and work using its Meshnet feature. It is also one of the few VPNs with a dark web monitor. If your accounts ever get compromised, it will send you alerts. It uses dedicated IP addresses, enabling you to access IP-restricted networks.
If unsatisfied with these features, you have a 30-day money-back guarantee to reclaim the amount paid for the subscription. You can also raise queries and make complaints via its 24/7 customer service.
2. ExpressVPN

An exceptional VPN service with high-speed servers and robust security features. It enables safely accessing any website on the deep web, allowing users to browse their favorite content without restrictions.
Pros
- Excellent security and privacy features
- Simple and user-intuitive interface
- Responsive customer support
Cons
- Expensive subscription fees
By popularity and trustworthiness, only a few VPNs come close to ExpressVPN. Since its launch in 2008, ExpressVPN has helped businesses and individuals stay private and safe online. It works with Tor, Freenet, and Invisible Internet Project (I2P), which form the three major pillars of the dark web.
This VPN has various features that keep you safe on and off the dark web. It uses 256-bit AES encryption for maximum data protection, has a no-logs policy, and protects against IPv6, DNS, and WebRTC leaks. It prevents your IP address from ever falling into the wrong hands in the depths of the internet via “Network Lock,” its kill switch available across all major platforms.
You can have your money back if ExpressVPN fails to impress you, leveraging its 30-day money-back guarantee. While this VPN may look slightly overpriced, considering a monthly fee of $8.32, it offers enough features to justify this rate.
3. ExtremeVPN

An all-in-one VPN provider that ensures maximum security and privacy while browsing the deep web. Its super-fast servers enable smooth browsing.
Pros
- Fast-speed servers with reliable connectivity
- Highly resilient VPN with obfuscated servers
- Numerous features at an affordable fee
Cons
- No dedicated Tor or dark web functionalities
ExtremeVPN is a recently launched VPN with all the functionalities you’ll find in older VPNs and even more. Its server network is widely extensive, and it has state-of-the-art encryption, prevents IPv6 and DNS leaks, and ensures privacy with a no-logs policy.
This VPN also has unique and advanced features, making it a must-have for the deep web. It uses obscure or obfuscated servers to hide VPN usage from ISPs and anti-VPN applications and services. It also has multi-port and domain fronting capabilities, giving you a premium VPN experience.
Despite the wide range of impressive features, you can get this VPN for as low as $3.29/month. Customer support is also swift and prompt and is available via live chat and a dedicated help section on the website to help you as and when required.
3. Protect your accounts with strong passwords
Another step you can take, which you have complete control over, is to improve the strength of the passwords you use to protect your account. A strong password typically contains uppercase and lowercase letters, numbers, and special symbols and lasts longer than 12 characters.
Characters meeting the above requirements are more difficult to brute force, making them safer. If you can’t think of a strong password, consider using a password generator. Google and other companies can also help you generate strong passwords when you sign up on a website and store them in your profile. Anytime you visit that website again and need to log in, Google will pull that password from your list of passwords and auto-insert it.
4. Avoid dropping personal information on the dark web
Whenever you’re on a dark web site, avoid dropping any personal information. Create anonymous profiles for any website you register with on the dark web. Additionally, ensure you do not visit websites or social media that might require you to drop your personal details.
5. Use multi-factor authentication
The increasing occurrence of cyber theft has made multifactor authentication more common. When you set this up, you’ll need to authenticate any login into your accounts on your mobile phone or other means. This helps because even if someone manages to obtain your password and tries to access your profile discreetly, it’s still up to you to authenticate their login.
FAQ
.onion sites are websites on the dark web that use the “.onion” domain rather than the popular “.com,” “.org,” or “.gov.” They’re only available on the Tor network, so you need the Tor browser to access them.
You can use Tor to visit regular websites like Facebook and Twitter, but you can’t visit .onion websites on other browsers besides Tor. The emergence of search engines like DuckDuckGo has also made it possible to search on Tor as you would typically do on Chrome, Edge, and Firefox.
To get on the deep web, you must first create an account with the website you want to visit or have profiles with them via other means. For example, to use a banking app, you must have an account with the bank. The same goes for other websites also in the deep web category.
What we call the dark web is a subset of the deep web. The greatest difference between them is that while you can still access the deep web with regular browsers, web pages on the dark web run on overlay networks. For that reason, they need specialized browsers for access.