uTorrent is a famous torrent client with more than 150M users worldwide. It earned this reputation because it is fast, reliable, and convenient to use.
Unfortunately, torrenting is one of those tasks online that come with hidden dangers and many users are unaware of them. One wrong step and you can face severe security and legal risks (sketchy download, identity theft, and legal penalties).
There are some workarounds you need to follow to keep yourself secure while torrenting. We suggest using a stealth VPN like NordVPN. In this article, we have also listed other important tips to download torrents from uTorrent safely and anonymously.
How to download torrents with uTorrent anonymously – Quick tips
What is uTorrent?

uTorrent is a software program for downloading torrents. The torrent client relies on the BitTorrent protocol to enhance a hassle-free P2P file-sharing experience. Rainberry Inc., formerly BitTorrent Inc., owns and manages uTorrent, although Ludvig Strigeus, a Swedish programmer, created it in 2005. Ludvig Strigues is a renowned programmer who is acclaimed for developing Spotify.
Reports from TorrentFreak revealed that uTorrent dominated the torrent market in March 2020, with about 68.6%. BitTorrent ranked second with 6.6%.
How does uTorrent work?
You must understand that torrenting is different from regular downloading. With regular downloads, the download server creates a copy of the file and sends it directly to your device. That happens when you download from mobile stores and general content download websites.

In contrast, torrenting operates on a Peer-to-Peer (P2P) platform. So, instead of downloading files from a single server, you get them from other users. You can access the P2P network via torrent clients or downloaders like uTorrent.
Now, how does torrenting work? When you create a torrent, you become the first uploader or seeder. The file becomes available for other users on the P2P network to download. Then, the torrent client begins seeding files immediately after users download them, so their devices become the servers for the files. Each user can now share with a group of other users. When a group of computers shares and downloads the same torrent file, it’s called “the swarm.”
How can you stay safe on uTorrent? Safety tips for risk-free torrenting

Yes, uTorrent can pose harm to your device and data. However, there are ways to bypass the dangers of the torrent platform. All you need to do for a hassle-free torrenting experience is to follow safety precautions.
Here are safety tips to ensure a safe and anonymous download on uTorrent:
1. Use a good virtual private network (VPN)
A VPN is essential for anonymity and privacy while using the internet. It encrypts your internet traffic, hides your IP address, and reroutes it so third parties cannot trace your activities to your location. Hence, Rainberry Inc. cannot trace the data it has logged to you or your device.
A VPN ensures internet freedom, especially if your country has banned torrenting. It helps bypass geographical restrictions and prevents all IP-related attacks and ISP throttling.
You may go through this list of the best VPNs for torrenting on uTorrent to find some reliable and safe VPNs. And if you want a general-purpose VPN for ultimate security, we recommend NordVPN. Below is a detailed overview of why NordVPN is the top VPN for downloading P2P files securely on uTorrent.
NordVPN

Among the most secure and safest VPN services, providing maximum security and anonymity while torrenting on unreliable platforms.
Pros
- Reliable and stable connectivity
- Provides NordLynx protocol for swift and seamless downloading
- Responsive customer support
Cons
- The OpenVPN configuration isn’t easy to navigate
With a brilliant network of over 6,800 servers across over 113 countries, NordVPN ranks number one on our list of the top VPN services. With the advanced IP detection technology it utilizes, VPN has the NordLynx protocol that enhances ultra-fast connection for subscribers.
It offers all you need for online freedom. You can access and download torrent files safely and bypass geo-restrictions without any hassle. It also offers a “Double VPN” for advanced security and protection at no extra cost. Finally, a VPN has a kill switch that shuts down internet activity when the VPN connection stops, so hackers and other third parties cannot access your traffic.
2. Install an antivirus
An antivirus offers real-time protection to prevent malicious files from infiltrating your device. A strong antivirus will flag a potentially harmful torrent file and deal with the threats if you decide to proceed with the download. You can couple your VPN with a strong antivirus program for enhanced security.
Check reviews online and recommendations from reliable sources for top antivirus programs you can try with uTorrent. Some are free, while others require users to pay a subscription fee for premium protection services.
3. Pick torrents carefully
Typically, torrent sites indicate verified and trusted uploaders so you can distinguish them from others. For example, The Pirate Bay distinguishes reliable uploaders with a green skull. You can also check users’ comments and reviews, and the number of seeders before downloading from an uploader.
As quick tips to ensure your online safety when torrenting, with uTorrent or any other client, we suggest avoiding torrents with low seeders and torrents of unreleased TV shows, games, and movies, as they’re suspicious and likely contain malicious files or viruses. We have provided a list of top torrent sites here that you can review and use to torrent your preferred content.
4. Avoid piracy
While internet piracy is a wide concept, we advise sticking to files in the public domain. No matter how enticing it might be to download torrent files of copyrighted content, it’s better to stick with open-source software and independent entertainment content.
This way, you can avoid legal problems relating to privacy. Rather than engaging in illegal torrents, you can try legal platforms like Netflix, Hulu, and Amazon Prime Video or free services like Peacock and BBC iPlayer.
How secure is uTorrent?

You must keep in mind that uTorrent does not guarantee optimum security. Potential threats come in diverse forms and from different sources on the platform. The following are some of the sources that can jeopardize your security:
- Torrent files you download
- Torrent clients
- uTorrent’s parent company (i.e., Rainberry Inc.)
Continue reading to discover the measures uTorrent has put in place to offer users a decent level of safety and explore the extra tips you need for maximum protection.
Does Rainberry Inc. collect your private data?
Although uTorrent is a safe torrent platform, it doesn’t have advanced safety measures in place. Hence, the fact that it might be safer than other platforms doesn’t mean it has a standard privacy policy. Here’s a list of the data that Rainberry Inc., uTorrent’s parent company, logs:
- Location: Your exact physical location
- Account details: Your name, password, email address, mobile number, and display name
- Cookies and web beacons: Data on how you interact with the service.
- Automatic data: Mobile carrier, IP address, device information, port number, cookie identifiers, mobile advertising, user settings, browser information, internet service provider (ISP) details, software information, and other unique identifiers.
While this is a whole lot of data that the company collects from users, we’re more concerned with this section of their privacy policy, which states that:
“We may also automatically collect information regarding your use of our Services, such as pages that you visit before, during, and after using our Services, information about the links you click, the types of content you interact with, the frequency and duration of your activities, and other information about how you use our Services.”
We advise internet users to pay close attention to the software services they interact with, especially because of the prevalence of crimes and criminal activities in the cyber environment. We recommend that readers avoid using software with activity logs.
Rainberry Inc., having access to comprehensive data on users, has to deliver these details to the NSA, 5 Eyes Alliance, and other authorities upon request.
Can uTorrent protect you from bad torrents?
In the world of P2P file sharing, torrents are the most dangerous. Torrenting opens up your device to the thousands of malicious files on the internet, especially if you’re unsuspecting. And uTorrent offers no form of protection against these files, so you must apply the security tips shared in this guide to ensure your digital safety!
We’ve divided the consequences of bad torrents into four categories. They include:
- Malware attacks: Bad torrent files can contain spyware, viruses, ransomware, and other malicious content. Once they infiltrate your device, hackers can access your private information to take over your device, steal from you, or blackmail you.
- Copyright infringements: Some malicious uploaders often upload copyrighted content on the torrent client without labeling it as such. Hence, you can download copyrighted content without knowing it, resulting in fines or severe legal penalties.
- IP theft: Thousands of internet users on your network can see your actual IP address. Hackers can use this to steal identity, attack devices, spy on you, and locate you.
- ISP throttling: Internet service providers can also monitor your activities while torrenting to regulate internet usage. This access helps them restrict your connection speed when you exceed the bandwidth usage (bandwidth throttling).
Advantages of using uTorrent
- Simple user interface: It is user-friendly, so first-timers can navigate the web pages easily.
- Remote control: The software allows users to control their downloads on the go. You can track, initiate, or stop your downloads from your web browser.
- Small size: The app is lightweight and doesn’t affect your CPU or memory. However, the free version contains unnecessary ads and other background runnings.
- Scheduled downloads: You can set when to start and stop your downloads, and uTorrent will execute it automatically.
- Speed limits: It allows users to set upload and download speeds to free up bandwidth.
Disadvantages of using uTorrent
Although uTorrent offers several benefits, especially for accessing blocked content, it also has drawbacks. Here are some of the disadvantages of using uTorrent:
- Seeding is necessary. Users must download files to seed before installing, accessing, or using them. Seeding is usually a prolonged process, especially when downloading multiple files simultaneously.
- Requires a VPN for enhanced privacy. A reliable VPN is essential to attaining optimum protection from internet service providers and other third parties. However, this additional layer of security comes at a cost. With uTorrent, using a VPN is our top recommendation among all the safety tips we ever advise.
- Can cause lags. Like any other BitTorrent client, it can slow down your device. This often occurs when your device consumes huge bandwidth, so opening different tabs and performing other activities online becomes time-consuming.
- Doesn’t allow users to view content before it’s fully downloaded. You must complete downloads to view any content. That means you can only confirm the torrent files’ content and quality once downloaded. So, if you open a movie expecting to play half of it because the remaining part of the torrent has been downloaded, that’s not the case. The movie won’t play.
uTorrent subscriptions and in-app ads
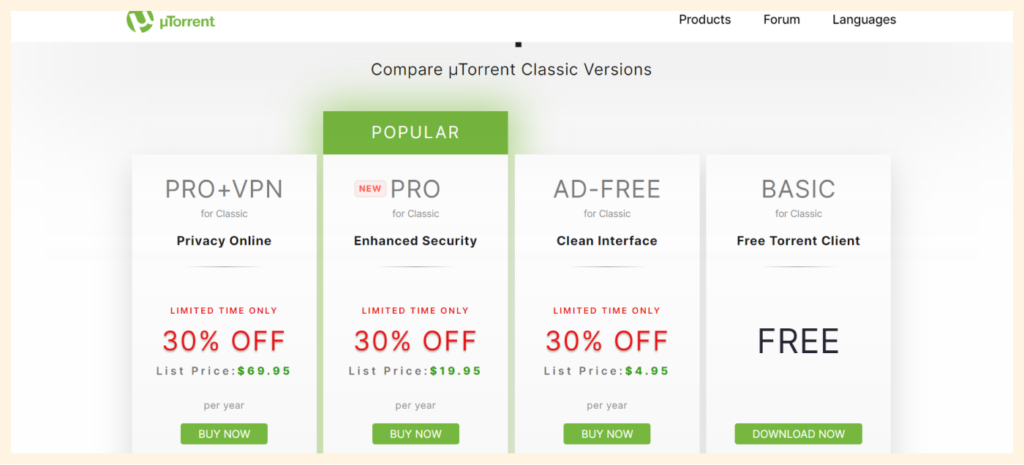
uTorrent uses in-app ads to generate revenue on the free version. However, users can turn off the feature for a hitch-free torrenting experience. The ads can also negatively impact your CPU and memory.
You can access its premium version by paying a subscription fee of $4.95 yearly. The premium version has advanced features such as malware protection and prioritized support. It also blocks every form of ads automatically.
Is the uTorrent app safe to use? (Full tests and results)

Although uTorrent from the official website is generally safe, you can always reduce or avoid the potential safety risks associated with the torrent platform by exercising caution and applying security tips while using it. Torrenting is a highly risky process, so sticking to file-sharing platforms with advanced security and protection features is essential.
Currently, the two uTorrent versions are:
- Utorrent Web: This version allows you to download torrent files and stream them while the download process is still ongoing. The web version also has a safe torrent scanner that helps identify safe torrents while surfing the web. Our tests revealed that it’s compatible with macOS (Catalina 10.5).
- uTorrent Classic: This is the official desktop uTorrent client compatible with Mac, Linux, and Windows. It supports simultaneous downloads and offers advanced features like a scheduler and automatic shutdown.
After a couple of extensive tests on these uTorrent versions, we can assure you they are safe for torrenting. However, uTorrent has a higher risk of security and privacy breaches than qBittorrent. uTorrent also is not an open-source client.
FAQs
While it’s not illegal to use this and other BitTorrent clients, some countries have laws prohibiting them in their territories. Also, if you download copyrighted content from uTorrent, you could face legal punishments.
The app from the official website is safe and secure. However, if you download from an unreliable source, you may download a malware-infested software program. Torrent files may also contain malware. That’s why you must use a reliable VPN and antivirus program to alert you promptly.
Yes, it does. It involves a peer-to-peer connection where other users download torrent files from your device. The process consumes data and can trigger bandwidth throttling.
Here are some effective tips to increase the download speed without compromising uTorrent safety:
1. Make sure you have a good internet connection.
2. Do not download files that have many leechers.
3. Make uTorrent priority a high priority.
4. Increase the download rate.