How we test VPNs before bringing them to you
At PrivacySavvy, we test and review the best VPN services on the market and rank them according to their performance and features, including speed, private browsing and streaming, and more. Here’s how we do it.
With cybersecurity threats increasing day by day, it is more crucial than ever to safeguard yourself online. One wrong step and you can end up facing serious consequences. While several tools promise to provide the best security online, not everyone is what they say.
A Virtual Private Network (VPN) is the first name that comes to mind whenever we think about digital privacy. Why it shouldn’t be—it’s truly a top-class security tool. With this, you can rest assured that you are safe and anonymous online, and no one can trace you back; not even your ISP. Other than providing optimum security, a VPN can help you in many ways, including streaming, torrenting, browsing, and more.
With the growing security needs, the demand for VPNs has increased. As a result, many new VPN services have entered the market. Therefore, it becomes difficult to cut through the noise and choose a good, reputable VPN service suitable for your needs.
This is where PrivacySavvy comes in. Based on rigorous testing and research, our team of experts provides extensive review and first-hand experience of the top VPNs in the market today. We always make sure to try a VPN service ourselves before bringing it to you.
Each of our reviews is written thinking about a specific type of consumer that has the following priorities in mind:
- Expects the best security
- Cares about digital privacy
- Wants fast speeds and reliability
- Want to bypass geo-blocks in several types of platforms
- Is looking for value for money
- Desires excellent customer service
- Wants the ability to bypass censorship
While giving unbiased VPN rankings in a particular article, we evaluate as extensively as above, based on that specific use case. Keep reading as we tell you how our staff considers all those variables.
Our top recommendations
- The Best VPN Services Today
- The Best VPNs for Android
- The Best VPNs for iPhone and iPad
- The Best Mobile VPNs
- The Best VPNs for Business
- The Best VPNs for Travelling
- The Best VPNs for Streaming
- The Best Free VPNs
- The Best Cheap VPNs
- The Best VPNs with free trials
Why you should count on us
Before we start, you may be wondering about our authenticity and thinking why you should prefer PrivacySavvy over other sources. Well, here’s a detailed review of our testing steps and why you can rely on us:
- Dedicated experts. We have an expert team of dedicated and experienced reviewers that focuses on We have a dedicated and experienced team that focuses on executing rigorous research and test and assessing the products we review. They check each VPN on different devices to collect data about the VPN’s effectiveness.
- Unbiased research. We go through different procedures and evaluate tests to check a VPN which we review. Moreover, we consult several reliable and third-party testing labs to cross-check things.
- Original research. We keep evolving and make sure to test the VPNs in new ways to improve our authenticity, reliability, and efficiency.
- Up-to-date information. We keep checking on the VPN services we publish to update the changes made by them, keeping our users up-to-date.
Our VPN testing methodology
Before evaluating the other VPN’s features, we certainly look at:
- What kind of technology it uses (connection protocols)
- The variety of servers it offers (number of server locations, RAM-only, static servers or dedicated servers, physical vs. virtual servers, etc.)
- Additional privacy-enhancing features (multi-hop (doubel VPN) connections and access to Tor)
- Its policy against collecting users’ data.
- Ability to bypass geo-restrictions and access platforms.
Let’s discuss in detail how we conduct tests and check these VPN services.
How secure a VPN should be

VPN security consists of two aspects, namely authentication and encryption. The purpose of the technology every VPN deploys for encryption is to keep all the traffic confidential and unaltered while it travels. Also, it ensures that only two parties on the internet can decipher the traffic’s content.
So we look closely at several security features in VPNs:
- The VPN tunneling protocol. OpenVPN is the industry’s golden standard, but WireGuard adoption is increasing as it maintains high-security levels with better efficiency and speed. Other protocols include IKEv2, SSTP, and L2TP.
- Channel encryption: we expect nothing weaker than AES-128.
- Authentication must be SHA-256, at least.
- Key exchange: we want nothing less than 2.048 bits in RSA and DHS keys.
- Perfect forward secrecy.
- DNS leak security. The vendor’s app must handle leaks correctly.
- WebRTC and IPv6 leaks. These types of leaks must also be avoided in the service.
- Kill switch: When your link to the VPN breaks down, all your traffic must stop. This is mandatory for us, and many providers lack it on mobile apps.
- Private DNS servers: our preferred services will have their own DNS servers in their network. This ensures that DNS requests do not reach Google or other public servers.
- Servers: are they virtual or actual? We prefer physical servers because their legal situation is more precise.
- The whole point of security is, more specifically, to avoid VPN data leaks. A leak is a packet that travels outside the VPN tunnel, thus compromising both security and privacy for the user in question.
VPN can include:
- IP leaks. It happens when your VPN shows your actual IP address to the world.
- DNS leaks: That’s when your DNS traffic reaches your Internet Service Provider instead of a DNS server within a VPN network. The Domain Name System is a digital directory that turns a domain name into an IP address so your computer can find it. If this information leaks, somebody else can see your visited websites.
- IPv6 leaks. The newest IPv6 protocol is still not the general standard for IP addresses. Some VPNs can only deal with IPv4 traffic but can’t handle IPv6 packets correctly, so they leak out of the tunnel –this is more frequent in Windows 10 systems.
- WebRTC. WebRTC came to life so that browsers could support video calls. It connects two browsers directly, so it can evade the VPN tunnel, thus creating a problem.
Browserleaks.com and ipleak.net are helpful sites for us as we check a vendor’s security. We test every time with and without the VPN online to know if the actual IP address is safe behind the VPN’s wall.
Why privacy matters with a VPN
Privacy means that nobody on the internet can identify a unique VPN user or figure out their online activities by monitoring the VPN link. And no, not even your VPN vendor should have this power.
Some of those goals are met through strong security measures (more on that later), but the VPN’s privacy policy is also vital.
We always prefer VPNs with a firm no-logs policy and stick to it. That means we don’t like any provider who keeps track of your browsing history, the apps or services you prefer, search queries, downloads, streams, and purchases. We also don’t want IP address logs (yours or your server’s) or connection timestamps.
Those bits and pieces are meaningful when somebody else tries to put the puzzle together about what you’re doing online.
However, there are some pieces of information that we consider clean. Your dates of connection, the data volume you used, or the countries you used to connect (but not the servers).
VPNs in the market pay lip service to no-logs while still collecting some of the data we mentioned. It usually happens with activity logs but not any additional metadata that could help to identify somebody.
So, some of our research includes reading carefully the log policies of over 150 VPN vendors.
Each VPN is incorporated in a specific country, which also counts. Every country has different legislation on digital issues, including mandatory data retention for service providers. In addition, some governments can force a VPN into installing spying features for the government’s benefit or surrendering user data.
So, we consider that the better options are those in countries that lack any data retention laws and that are outside the influence of the most active surveillance alliances and powers — the US, UK, and China, for instance.
Taking privacy-friendly payment methods such as Bitcoin and other digital assets is a privacy bonus as far as we’re concerned.
How we test the VPN speed
Our VPN speed test results are global averages unless we specify otherwise. We test each VPN several times throughout the day, at least four hours apart, and use three locations, usually one in North America, one in Europe, and one in Asia. Then we compute the average in the report.
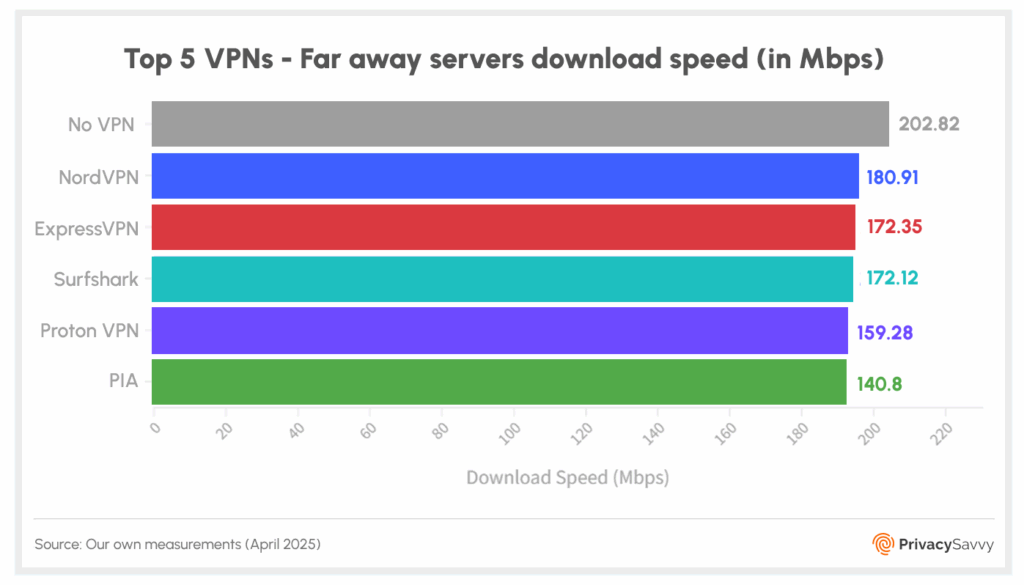
We start with the VPN’s Windows app on a 1Gbps link using the fastest protocol on offer (that’s usually WireGuard, when available, if not, then it’s OpenVPN or IKEv2). Next, Ookla Speedtest is the desktop app that performs our measurements mostly.
If any result is too far away from the mean (by three sigmas or more), we drop it and repeat the test.
We usually report download speeds primarily because that’s what most users want to know. Some of our reviews do include upload speeds, though.
We do not pay much attention to pings (lags or VPN latency). This is because ping time is irrelevant to understanding a server’s performance.
But besides taking measures, we test the servers for functionality by streaming high-resolution videos and playing resource-taxing online games.
Lots of VPNs claim to be the fastest. However, VPN speeds are very tricky to quantify correctly. It’s impossible to test every server several times daily. We keep to the most accurate and empirical data, but the speeds we can get from a VPN depend on our location. Hence, your experience could be very different, depending on where you are.
Also: high video streaming speeds do not guarantee high gaming speeds.
Bypassing region blocks and video streaming platform
Unblocking video streaming services and platforms has become one of the top reasons to use a VPN over the last few years. The best legal streaming services have different content in different countries because of their licensing agreements, so worldwide users get a different deal depending on their location. A good VPN can do away with such restrictions by deceiving a streaming service into thinking you’re in another country.
So we try the following service to see if the VPN will unblock them:
- HBO Max
- Disney+
- Hulu
- Amazon Prime
- BBC iPlayer
- Netflix
That’s the start only because those are the most popular platforms, but we will try more depending on how things develop. We test both the platform’s app, when available, and the website because not every VPN can deal with both. Our Netflix testing is comprehensive, as it’s the most demanded platform.
Censorship
In countries where web censorship is heavy and governmental, many users want a VPN to bypass it. Take China, for instance. Only the best VPNs can bypass the Great Chinese Firewall to access content that is usually unavailable to them because their ISP blocks it because of government orders.
But censorship at a smaller scale happens everywhere. For example, corporations and schools often block many websites in their local networks to prevent distractions.
We test every VPN capability to get around the Great Firewall of China and other official blockages whenever possible. But these situations can change rapidly. So we endeavor to keep our reviews as fresh and current as possible to address these changing realities.
Servers are important
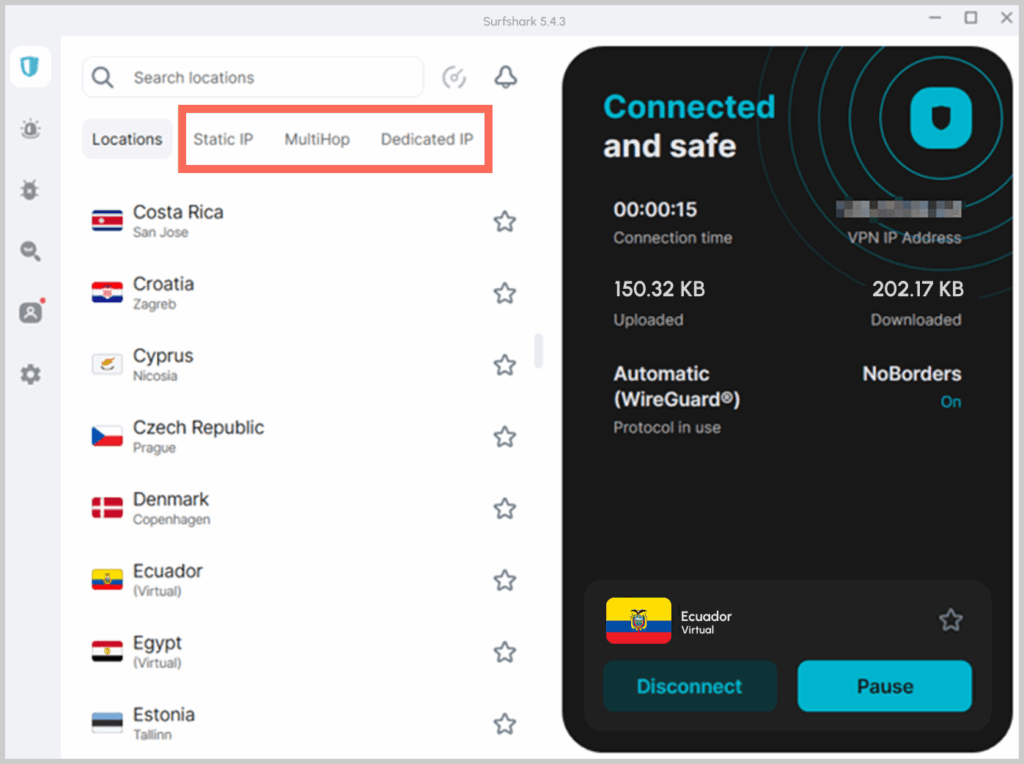
The number of nodes in a VPN network can be impressive overall. But it’s not as important as you could think. The resources and efficiency in every server are more critical. So having 10,000 servers isn’t always better than having 100.
But if you want something in which numbers matter, think of locations on offer. For example, an average VPN offers servers in 35 to 65 countries. So if you know the country you want to connect to, the most important thing is that your VPN has servers there. For example, NordVPN has servers in more than 118 countries, which can be more helpful.
Also, some VPNs have virtual servers. These are computers located in one country but with an IP address from another. So here you have a server that will get you access to a country you want. But it’s located elsewhere, so the local laws are different, which has implications for your privacy. Conversely, VPNs can “have” servers in jurisdictions where they can’t operate, like Iran or China.
Apps
Your VPN must work on every device you use. Most VPNs have apps or clients that work in:
- iOS
- Android
- macOS
- Windows
- Linux
But some VPNs provide software for more exotic devices such as Amazon Fire TV, wifi routers, Android TV, Windows Phone, Blackberry, and Linux devices.
Some VPNs also offer browser extensions for a variety of web browsers. However, beware that those browser extensions will protect your web traffic only, while the rest of your traffic will remain in the open—the exceptions are providers ExpressVPN and NordVPN.
We like apps that include trackers, ad and malware blockers, traffic obfuscation, automatic wifi protection, split tunneling, and a kill switch.
Another feature is the number of concurrent links to the VPN you can have with a single account. Five is the industry’s standard, more or less. But some will give you ten, and a couple of excellent VPNs have unlimited connections.
Reliable customer support
Ideally, you should never need any help with your digital services. Especially with a VPN because it works on such a basic level of your digital experience. However, life is rarely that simple, and the chances are that you could need some help sooner or later. That’s why we also pay attention to a VPN’s customer service.
We keep track of response times, availability, and the knowledge and friendliness of the VPN’s agents.
We prefer VPNs that offer both ticket submission and live chat systems. The second option tends to be faster and more private.
We also have a look at billing practices. For example, is there an auto-renewal thing going on? Is the cancelation process a pain in the behind?
Last but not least, money-back guarantees are a plus.
Pricing and plan
While testing VPN services, we thoroughly analyze each VPN’s pricing and subscription plans to determine value for money. Here’s how we assess pricing and plans:
- We examine different plans of different services (monthly, yearly, and more) and compare each other regarding the features. Some VPNs restrict advanced features like kill switches, dedicated IPs, or multi-hop connections to higher-tier plans, so we always check whether the VPN is value for money or not.
- Long-term plans often offer significant discounts. However, we always verify if the provider has a history of sudden price hikes or hidden charges. We also compare the VPN’s pricing against competitors to gauge market competitiveness.
- A reliable VPN should offer a risk-free trial period (usually 7–30 days). We test refund policies to ensure they are hassle-free and are as advertised.
- We check if the VPN accepts anonymous payment options like cryptocurrency or cash to enhance user privacy. Providers that only accept credit cards may not be ideal for privacy-focused users.
- Some VPNs frequently run promotions, so we assess whether their “discounted” prices are genuine or just marketing tactics.
By scrutinizing these factors, we help users choose a VPN that offers the best balance of affordability, features, and transparency—without compromising on quality.
Why unbiased testing matters
A lot of the content you will find on the VPN subject is not so trustworthy. It’s done through sponsored or free accounts and amounts to little more than a sophisticated form of publicity. We need to find out how things are for an average paying customer so that we can share that experience with you.
That’s why we’ve designed a testing process that aims to eliminate any bias.
First, we actually pay the fee for every account we test and use on several platforms and operating systems. Second, we perform every test ourselves, from speed measurements to geo-unblocking. Third, we look at the company’s jurisdiction and privacy policies. And, in the last step, we write everything down in a review that you can read, understand, but most of all, trust.
Is it legal to use a VPN?
Yes, in most regions, including the United States, the United Kingdom, and most of the European Union. However, in some countries, using a VPN is a severe crime or has limitations.
Currently, countries including Iraq, Belarus, Russia, and have banned using a VPN. As reported in NordVPN’s country guide, countries like China and Egypt restrict and discourage VPN use and put heavy restrictions to eliminate the risks of criminal activities.
You can evade these restrictions, but these workarounds come with a price.