The average internet user lacks the expertise to judge correctly how good a VPN is. It’s all about striking a balance. You want your VPN to protect all your internet traffic (including web traffic), so that’s genuinely bulletproof. So, how should a “normal” user choose a VPN?
Perfect Privacy is a Swiss company that puts it out of the international surveillance alliances (out of the reach of the most common spying agencies). It has a strict no-data logging policy, and it splits tunneling through several servers simultaneously.
In this Perfect Privacy VPN review, we will examine each and every security aspects of this service, its speeds, and more, and let you know if the service is suitable for you or not.
Perfect Privacy key features at a glance
| Servers | 55 servers in 23 countries |
| No-logs policy | Yes |
| Torrenting available? | Yes |
| Kill Switch | Yes |
| Split tunneling | Yes |
| Based in country | Switzerland |
| Free version | No |
| Simultaneous devices | Unlimited |
| Money-back guarantee | 7 days |
The pros and cons of Perfect Privacy at a glance
- Based in the safe jurisdiction of Switzerland and follows a strict no-logs policy, meaning that it does not collect or share user data
- Offers additional security features such as tracking blockers, multi-hop, port forwarding, an excellent firewall, and stealth mode
- Provides advanced privacy and security features, including robust AES 256-bit encryption and IP/DNS/WebRTC leak protection
- Supports unlimited simultaneous connections from a single subscription
- Allows torrenting on almost all of its server networks
- Includes an updated Warrant Canary
- Offers HTTP and SOCKS5 proxies
- A bit more pricey than most VPN providers and does not offer adequate value for money
- It has a small VPN server network that offers relatively slow global speeds
- The VPN service has a limited 7-day money-back guarantee
- It does not unblock major streaming platforms like Netflix, Amazon Prime Video, and Hulu
Perfect Privacy servers
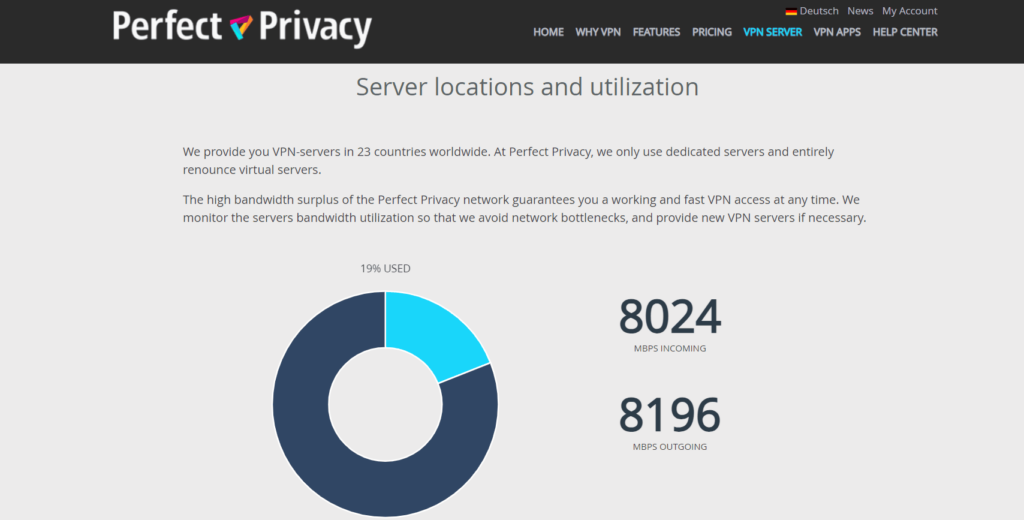
Perfect Privacy owns 55 servers scattered in 23 countries. That is good, but not a lot (other providers have private servers in, say, over 90 countries). That being said, if there is a server in your country that’s good enough for you to be sure you’ll be well taken care of, the company’s lack of international presence needs not to be relevant to your decision.
Just make sure to do your due diligence and find out if there’s a server available near you before spending your money.
Perfect Privacy VPN speed
Here’s where we roll up our cyber sleeves and get our digital hands dirty to test Perfect Privacy’s performance.
Speed test
Perfect Privacy is pretty slow compared to most premium VPN providers. According to our tests, it offers superb local speeds, with only a 12% drop when downloading. However, the international download speed reduction was significant, with our connection rates to Germany reducing by 34%.
We tested the performance of Perfect Privacy by monitoring the connection speeds between our base location and this VPN’s servers worldwide. The table below outlines the results in detail:
| Server location | Download speed (Mbps) | Upload speed (Mbps) | Ping (ms) | Distance (mi) |
|---|---|---|---|---|
| No VPN (UK, London) | 100 Mbps | 100 Mbps | 1 ms | 0 mi |
| UK (London) | 88 Mbps | 87 Mbps | 24 ms | 10 mi |
| UK (Manchester) | 85 Mbps | 89 Mbps | 78 ms | 3,700 mi |
| US (Los Angeles) | 48 Mbps | 88 Mbps | 75 ms | 2,700 mi |
| Canada (Toronto) | 41 Mbps | 85 Mbps | 20 ms | 400 mi |
| Japan (Tokyo) | 38 Mbps | 87 Mbps | 145 ms | 7,000 mi |
| Germany (Berlin) | 74 Mbps | 55 Mbps | 88 ms | 3,800 mi |
| Australia (Sydney) | 26 Mbps | 86 Mbps | 210 ms | 9,500 mi |
The servers near our base location displayed a good performance, with only a 12% drop in download speed. In addition, when connected to a Manchester server, the fastest speeds encountered a 15% drop.
There was a significant drop when we connected to US servers, recording a 52% decrease. This is because our traffic has to travel a long distance. The situation was even worse with faraway servers like Australia and Japan, where we couldn’t stream YouTube videos. High-performance activities like gaming and torrenting require better speeds than this server offers.
Although Perfect Privacy’s speeds are reasonable, other top VPN services, such as ExpressVPN, offer lightning-fast speeds. Therefore, Perfect Privacy should incorporate the WireGuard protocol and expand its server locations to enhance speed.
DNS leak test
DNS means domain name server. You type it in your browser when you want to load a website. It stands for an IP address, which is the object that counts. You want to keep your DNS hidden inside the encrypted tunnel when using a VPN. Perfect Privacy passed the test as it showed no DNS leaks at all.
WebRTC leak test
WebRTC enables users to have a direct information link without any central server. Of course, the direct connection without intermediate nodes makes leaks more likely. Still, it also allows for faster transfer speeds that remove some friction from live streaming, sharing files, doing video chats, etc. To engage in a WebRTC link, both users need to know their private IP addresses. So this is a good test to run in any VPN, and Perfect Privacy passed it, again, with flying colors.
Perfect Privacy VPN Security
All VPN providers should prioritize protecting user data against third-party access. This is accomplished by masking your IP address, avoiding harmful logging policies, and encrypting your web traffic. Perfect Privacy provides robust security features, such as OpenVPN and IKEv2/IPSec protocols, a great firewall, and a no-logs policy, making it an excellent security option.
Kill switch
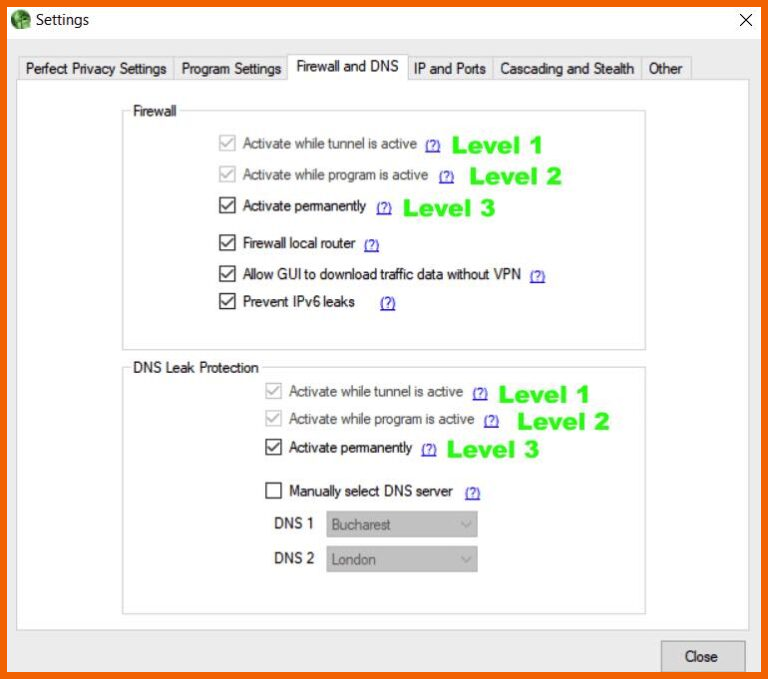
A kill switch lets you immediately disconnect your internet connection if your VPN connection drops, ensuring your safety. Perfect Privacy VPN does not include a kill switch, but it offers an excellent firewall, which is more valuable than a kill switch.
You may choose to activate the firewall when connected to a VPN server. On the other hand, you may use it autonomously from VPN connections or enable it permanently.
However, the permanent firewall option blocks all the web traffic that is not directed via a VPN tunnel. This means you cannot access the internet without using the VPN service. In addition, the setting will remain effective until you disable it.
The VPN’s encryption
Encryption is a funny thing that turns readable information that makes sense into a stream of numbers that looks like noise and is useless to anyone (save for those who can decrypt it). It’s what VPNs do to your data so that unwanted wrongdoers can’t make heads or tails of your online activity.
Perfect Privacy uses AES-256, which is the industry standard for encryption. The AES algorithm has been audited and tested beyond anybody’s endurance, so it’s deemed entirely safe.
Every IP address is anonymous, as all Perfect Privacy members share it. Of course, you could get the same IP address on reconnection occasionally, but that is not a problem because the information remains ciphered. The DNS and domain name servers are anonymous as well.
Encryption is used along with IPSec in one of two modes. Either the data packet’s message with transport mode or encrypting the whole packet within the tunneling mode. Either way, your data is safe.
The protocols supported by Perfect Privacy
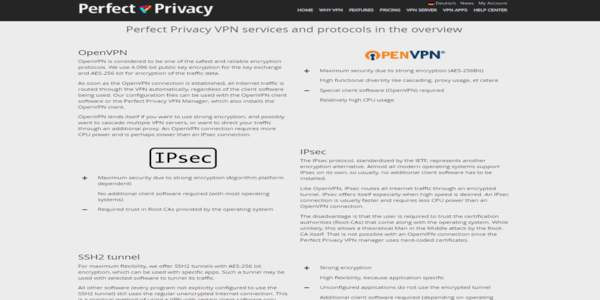
Data can’t just spread around the internet like water. It needs to be sent from one node to another. Internet protocols govern this action. Like in any voyage, a data packet has many options and many possible paths that can take it from A to B. Which way is shorter, safer, and quickest? Perfect Privacy uses several Internet Protocols to make those choices with top security in mind.
- OpenVPN: Knowing that a VPN has OpenVPN working for it under the hood, my peace of mind increases. Why, we hear you ask? OpenVPN’s reputation for security and ability to get around firewalls has no peer in the industry. It’s a crowd-sourced community project that continuously improves and keeps up with the work the surveillance agencies are doing to deal with it. OpenVPN is the way to start if a VPN is built from the basics.
- SSH2 tunnel: Secure shells create a tunnel as well as encryption that allows the information to flow. The SSH doesn’t encrypt the packets itself, but it’s like the pipe that will guide them. SSH2 is a different thing. It’s more secure, and it delivers higher security standards.
- Squid proxies: No, I have no idea why they call them squids. These neat little toys keep a cache or storage of the most repeated requests (web, DNS, network lookups). That speeds things up for users because, if they’re interested in mainly the same things as everybody else, the information is already available without making a computation or a remote query.
- Socket25 proxies: The name means socket version 25. This protocol gives you a new IP address when you join the VPN and takes your data from here to there. It doesn’t encrypt any data; it merely hides your authentic IP address from the servers you are reaching. It’s swift and reliable but not that safe in itself. That is why there are additional encryption layers in the service.
- PPTP: Point-to-point Tunneling Protocol comes up with yet another tunnel. This one encapsulates data packets. Again, it’s just a pipe that is not that secure, but it doesn’t matter, as other layers in the data flow take care of privacy and anonymity.
Perfect Privacy privacy features
Let’s see Perfect Privacy’s features in more depth, one at a time:
TrackStop
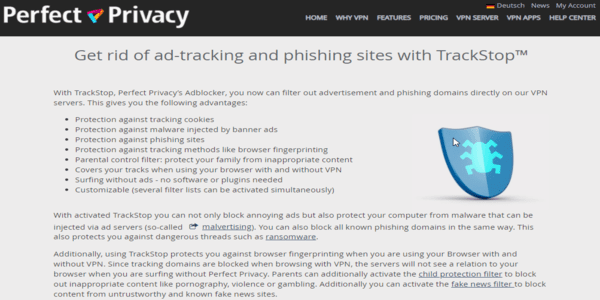
TrackStop is how Perfect Privacy blocks ads. Mind you, avoiding ads is not just a matter of convenience. Malicious ads are the wrongdoers’ preferred option to deliver malware, phishing attacks, and ransomware. That is why ad blocking is, indeed, a legitimate security concern.
But TrackStop’s features don’t end with unwanted or malicious advertising. It will allow you to block specific content that you don’t want. That could include porn, violence, or social media. It even deals with “fake news” from fishy sites.
Last but not least, TrackStop prevents browser fingerprinting. So, what is this fingerprinting thing? Even if you are in incognito mode and using a VPN, you can reveal plenty of information to a website you visit. It will know what browser you are using, your operating system (version included), screen resolution, time zone, language, hardware configuration, and plug-ins to tell you the least technical things involved.
Do you think that’s not such a big deal? In this day and age, a PC is a highly personalized thing. You choose your OS, the programs you install, the browser you use, how you like your resolution to be set, and a hundred other little things. So many different computers in the world may be the same brand and model, with similar hardware.
But the chances are that only you have configured your machine to your liking to the last detail. The possibility is that nobody else in the world matches your browsing profile (fingerprint) in every detail. And that is why it doesn’t take a brilliant hacker to come up with some valuable conclusions from seemingly innocuous information. Well, TrackStop gives you peace of mind in this regard as well. The company has thought of everything indeed, and that is very impressive.
NeuroRouting
NeuroRouting is a Perfect Privacy VPN feature that allows for the dynamic routing of all traffic through multiple server hops. This process takes place on the server side, providing a more efficient way to use the entire VPN server network. NeuroRouting can be broken into the following concepts for easy understanding.
- Dynamic: With NeuroRouting, your internet traffic is routed through multiple “hops” on the VPN server network using TensorFlow machine learning to take the most secure path. TensorFlow continually learns and adapts to find the best route for a given website or server, keeping your data encrypted for as long as possible before it exits onto the regular internet.
- Server-side: NeuroRouting is a server-side feature, which means that it is active and functional every time you connect to the VPN network across all devices. It can be disabled from the member dashboard. It is also compatible with various devices, such as routers, macOS, and Android. In addition, it works with OpenVPN and IPSec/IKEv2 VPN protocols, which are built-in on Mac OS, Windows, and iOS devices.
- Simultaneous: When accessing different websites with NeuroRouting, each website will take a unique path, meaning each access point will have a different multi-hop configuration and IP address. The IP address broadcasted to each website will correspond to the final “hop” in the server chain for that specific website.
Advantages of NeuroRouting
- The use of TensorFlow to find the most secure route for a given website or server allows for more efficient use of the VPN server network, as well as an automatic adaptation to changes on the internet.
- NeuroRouting adds an extra layer of security and privacy by routing internet traffic through multiple server hops.
- With NeuroRouting, each website or server access point will have a unique IP address, making it harder for your internet activity to be tracked.
- The feature can improve the performance of your browsing and streaming activities by dynamically adjusting the routing based on the current network status and usage.
- The feature will mask your identity by providing a different IP address for each website or server access point, increasing the user’s anonymity.
- NeuroRouting lowers the possibility of potential attacks.
Port forwarding
Port forwarding is a networking method that directs incoming traffic to a specific device or service on a private network by forwarding the traffic to a specific port number.
It improves the performance of certain games and file-sharing programs, such as torrent clients, and allows you to access your device remotely. Also, the technique authorizes specific incoming connections to reach a device or service on a private network, bypassing the NAT firewall.
It is important to note that having open ports on your device can make you vulnerable to different types of attacks. Many reputable VPNs, like NordVPN, limit access to only commonly used ports by popular applications. They employ this measure to ensure your online security.
While Port forwarding can be useful, you should use it cautiously because it can increase security risks. It is recommended not to open any ports unless you understand how they work.
Compatibility
This VPN service provides apps for macOS, Android, and Windows. However, it lacks native apps for iOS users.
Apps
Perfect Privacy has custom apps for popular devices like Linux, Android, macOS, and Windows. You can install the iOS app, but it requires manual setup, which is a bit complex. Also, the VPN supports unlimited simultaneous connections from a single account.
Moreover, you can manually configure supported routed models using a detailed guide on Perfect Privacy’s site or purchase a pre-configured router with the VPN program.
The table below shows a summary of how Perfect Privacy’s apps vary in features:
| Device | Protocol | Proxy | Kill switch | Split tunneling | Stealth protocols | Port forwarding |
|---|---|---|---|---|---|---|
| macOS | OpenVPN | Yes | Yes | No | Yes | Yes |
| Windows | OpenVPN, IKEv2 | Yes | Yes | No | Yes | Yes |
| Android | OpenVPN, IKEv2 | Yes | Yes | No | Yes | No |
| iOS | OpenVPN, IKEv2 | Yes | No | No | Yes | No |
Windows
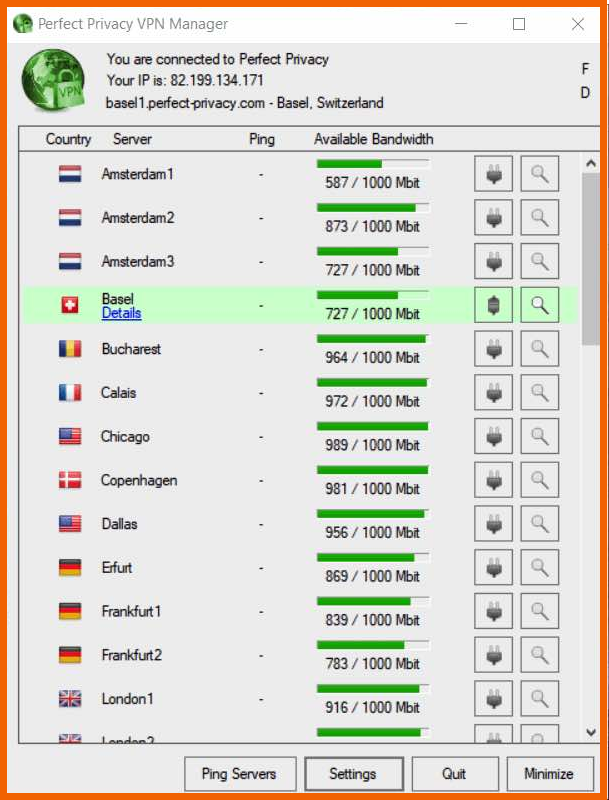
The Windows app appears outdated and is hard to use for beginners. The servers are listed next to their own connect button and available bandwidth, resulting in a highly technical and crowded design.
However, connecting to a new server does not automatically tweak your connections, so you must first disconnect your current server manually. This isn’t very pleasant and is not the situation with most VPN providers.
The ‘Settings’ tab introduces a new window listing all advanced tools. This menu lets you select between OpenVPN or IPsec protocols when you enter your login credentials.
Also, the ‘Program Settings’ tab includes several typical options, like the order in which you want the server list to appear and whether the app should launch when Windows starts up. Also, it supports multiple encryptions, a single server configuration, and a TCP switch.
The ‘Firewall and DNS’ option offers information on every level of the VPN’s DNS leak protection and kill switch. Furthermore, the ‘IP and Ports’ option is not available for beginners, but the VPN inspects every toggle and proposes the best choice for novices.
The ‘Penultimate’ section includes Proxy settings, stealth, and Multi-hop. Also, the multi-hop feature is simple to activate and enables you to manually enter the number of hops you want, which are limited to four. Likewise, the stealth tool is straightforward, allowing you to tunnel your internet traffic via Obfsproxy, Stunnel, or SSH.
Furthermore, the proxy settings are hard to use and require an update as well as contextual information. The app functions in the system tray while minimized, and you cannot adjust this option in settings.
macOS
The Perfect Privacy macOS app varies from the other versions and has a different company logo as well as color style.
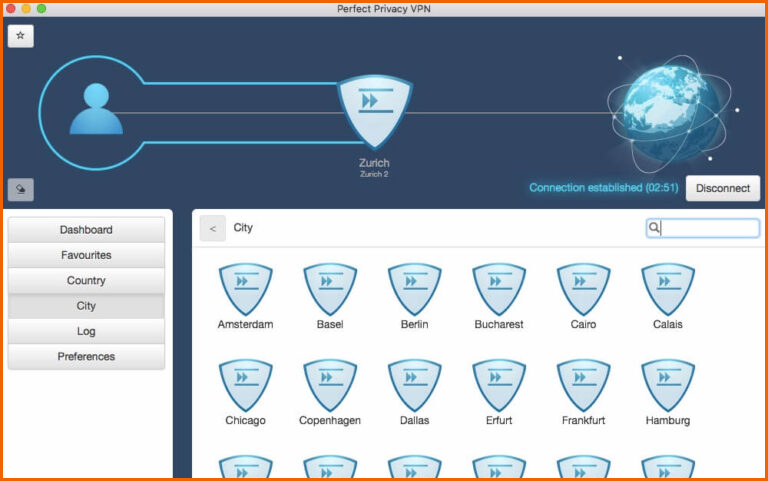
It allows you to connect to a server by choosing your desired location and tapping the ‘connect’ button in the top right corner of the screen. Although this app is outdated, it is straightforward.
Furthermore, the macOS app includes a server location in Egypt that does not display on the other versions. Also, the app’s settings are limited as it allows cascading connections but restricts TrackStop and NeuroRouting.
The app allows you to select between two OpenVPN protocols, UDP and TCP, but lacks the IPsec option. Also, it has a stealth mode, web traffic leak protection, and port forwarding to enhance security.
Moreover, the custom app lacks proxy connections. To configure Tor, SOCKS5, and HTTP proxies, you can install the ‘Secure Pipes’ software from the VPN’s official site. In addition, the official site gives you instructions on how to install the app, but they should add this feature to the native app.
Android
Perfect Privacy’s Android app offers a more appealing design and is simpler to use. Unlike the Windows app, it automatically connects to a new server without requiring you to disable the previous one.
The Android app has a few settings. For example, you can pick a server to act as the ‘Default VPN Profile’ and switch whether the VPN should always be on or not. Also, it includes the option of disabling Android’s optimization notifications. In addition, the ‘Get Support’ tab redirects you to the VPN’s official website.
Moreover, if you wish to employ a kill switch or stealth mode, the VPN will redirect you to OpenVPN’s page and recommend installing its app on your Android device.
iOS
Perfect Privacy VPN lacks a custom app for iOS. On this VPN’s official website, the ‘VPN APPs’ tab contains several tutorials explaining how to install a VPN profile on an iPhone manually. Additionally, it offers information on establishing a proxy connection and using the VPN’s stealth protocol on iOS.
These tutorials may be useful, but they are not alternatives for offering a real native app. Furthermore, when we contacted customer support, they confirmed that iOS does not support the TrackStop features.
Streaming devices & game consoles
Perfect Privacy VPN supports many streaming devices, such as Apple TV, Amazon Fire TV, and Chromecast, and game consoles like Xbox, Roku, PlayStation, and Nintendo.
This VPN service is not an ideal option for streamers and gamers. Despite its efficiency in DNS/IP leak protection and a kill switch, it has a pretty high ping, which is unfavorable for online gaming.
Because gaming consoles such as Nintendo Switch, PS4, AND Xbox fail to support native apps, you will be required to install Perfect Privacy VPN software on your router. Furthermore, several streaming devices, such as Roku and Apple TV, did not work, necessitating a similar workaround.
The VPN supports Tomato, pfSense, dd-wrt, Asus, and OpenWrt routers. Moreover, Perfect Privacy’s website offers detailed installation tutorials for all these gadgets.
Amazon Fire TV
Perfect Privacy’s site claims to offer a native app for Amazon Fire TV, but we could not locate one. Customer support confirmed that they are working to remedy this issue.
Perfect Privacy VPN streaming
Perfect Privacy is not an ideal VPN for streaming. It lacks dedicated servers and has a limited server network, preventing it from unblocking popular streaming platforms like Disney+, Netflix, and BBC iPlayer.
Our streaming test results when using Perfect Privacy are shown in the table below:
| Streaming site | Compatible with Perfect Privacy |
|---|---|
| YouTube | Yes |
| Disney+ | No |
| Netflix US | No |
| Hulu | No |
| ITVX | No |
| Hotstar India | No |
| HBO Max | No |
| Amazon Prime Video | No |
| BBC iPlayer | No |
| All 4 | No |
This VPN service focuses on security and privacy above streaming. The Android app constantly failed to access any streaming site. On the other hand, the Windows version was more unreliable, considering the London servers offered us Turkish and German IP addresses.
Moreover, even after establishing a connection with a London server, the ‘TrackStop’ feature blocked our attempts to access the homepage of BBC iPlayer on a desktop. Nonetheless, we could not access Netflix across all Perfect Privacy versions on all US servers. In addition, access to HBO Max, Disney+, and Amazon Prime Video was impossible. We recommend using a reliable VPN to access major streaming platforms like ExpressVPN.
Perfect Privacy and Netflix
Netflix is the thing for many users these days, so we have to mention it explicitly.
The news is mixed if you’re into Netflix. Perfect Privacy has no restrictions regarding Netflix at all. But Netflix does have a list of banned IP addresses they block. So, there’s a good chance you are out of luck if Netflix is so essential to you. The only way to find out for sure is to try. But even if today it works, it could fail tomorrow as Netflix updates its blacklist.
It wouldn’t get better in the future if you were hoping for something to change. Streaming is not this VPN’s priority at all. Instead, its focus is on privacy. That’s where this service excels, even if streaming your favorite movies suffers. In short, if Netflix is your priority, you should better get one of the VPNs that work for Netflix.
Does Perfect Privacy allow torrenting?
Perfect Privacy allows P2P file-sharing on all of its servers, except for servers in the US and France, due to the strict laws on file-sharing in those countries.
The data centers that host Perfect Privacy’s servers in those regions are under legal pressure to disallow file-sharing. However, P2P is permitted on all other Perfect Privacy servers.
Perfect Privacy also has a port forwarding feature that can improve the torrenting experience. Enabled allows users to seed content to other peers, making it easier and faster for them to download torrents. Additionally, port forwarding can also increase download speeds. Perfect Privacy offers a port forwarding feature for P2P, which includes two options: dynamic and dedicated.
Dynamic port forwarding provides three dynamically allocated ports that change with each connection. Dedicated port forwarding offers five customizable ports that stay active for seven days for extra security, and you can configure the type that best fits your needs.
Can Perfect Privacy work in China?
Perfect Privacy offers several features for users in restrictive nations such as China, Iran, and Turkey.
First, it has StealthVPN, which disguises data packets as regular HTTPS. The details of how this feature works are not disclosed, but it will likely use TCP protocol over port 443.
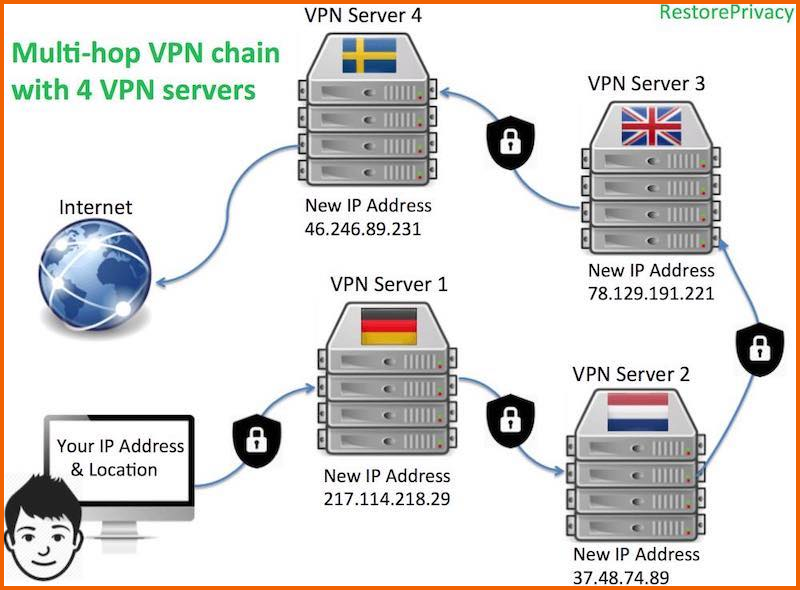
Cascaded VPNs or Multihop is the second feature that allows you to connect to multiple VPN servers in a chain, first connecting to one server, then to a second, third, or fourth server (maximum of four hops). This allows you to have different entry and exit IP addresses, making it more difficult to trace your internet connection.
The third feature is NeuroRouting, which uses an algorithm to determine the safest route for a user’s internet traffic based on their actual location and the traffic’s destination. It routes the traffic through multiple VPN servers depending on the algorithm’s best route calculation.
Customer support
Knowing you can count on the attention of any service provider is always important, even more so when we’re talking technology because not every user is a hacker. Also, a few things in life can cause so much frustration, such as configuring any computer-related item in the “correct” way according to the instructions to see how it keeps not working correctly.
But, at the same time, you still haven’t got a clue about what’s wrong. So, this is also a scenario in which help from your provider can save you a lot of time and stress.
VPNs need users to configure many little things here and there in their operating system or device, which is why good customer support is vital for VPN users. Let’s see how good Perfect Privacy is.
It pains us to say that customer service is not excellent because it lacks two critical features: phone support and live chat support. There is also email support, online contact forms, FAQs, manuals, and a forum.
And how can you compare your experience with those of other users? Well, you can’t. In Switzerland, the customer support culture is not so big a deal yet; there is no Better Business Bureau, and the thing is not on sale on Amazon.
Subscription plans
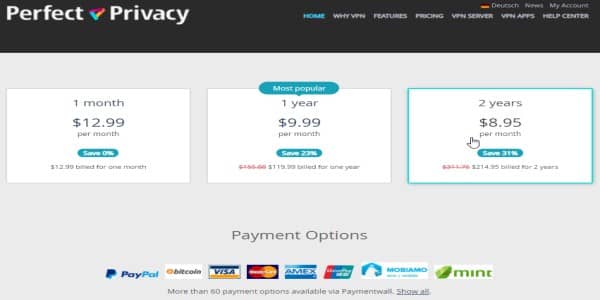
Perfect Privacy is, of course, not a free VPN. There is no good VPN that cares for users’ privacy. So you have to pay a fee, but your subscription enables you to have unlimited server switches, simultaneous connections, and connected devices. It’s a rather good deal as there are no limitations involved.
You can buy a subscription in several plans that last for a month, three, six, twelve, or twenty-four months. Naturally, the more extended plan you buy, the more money you save monthly, and your savings can go from 7% in the three-month program to 31% in the two-year option, relative to the single-month subscription. The highest fee is 12.99 USD monthly, progressively decreasing as the plan’s length increases to 8.95 USD.
The first thing to notice is that Perfect Privacy is a pricy service for the industry’s standards. Plenty of subscription-based VPNs start at about 3 USD monthly, while this Swiss option can be four times more expensive. However, the company is aware of this fact enough to address it directly on its website.
Perfect Privacy explains its higher prices in terms of its superior features, unlimited simultaneous connections, support of many operating systems, unlimited bandwidth usage, and other almost exclusive advantages.
It’s hard to argue against it because Perfect Privacy’s service is absolute in every meaningful way. The cost is justified if privacy in all your devices is your top priority. As stated before, the one disadvantage you could find is if you are used to watching a lot of Netflix content, in which case you’re pretty much out of luck.
Payment methods
Perfect Privacy payment methods include:
- Paypal
- Bitcoin
- Credit cards
- Over 50 payment options via Paymentwall.
One preferred option is purchasing a Bitcoin VPN because of the added anonymity.
Note: Perfect Privacy no longer accepts cash payments.
Usability – Is Perfect Privacy VPN easy to use?
The desktop apps for Perfect Privacy include many customizable options. This makes it an appealing choice for knowledgeable users but complex for beginners.
You can install and setup Perfect Privacy by following the steps below:
- Click the ‘Download’ button to start the installation procedure.
- Accept all of the necessary installation prompts.
- Choose the protocol you wish to connect to and log in using your credentials.
- Select the server location you want to connect to from the list and click the button to the right of the server.
- When a connection is established, the globe in the top left corner turns green, and the app shows your new IP address.
It allows you to select the encryption levels in the settings menu. We highly recommend the robust AES 256-bit encryption. You can also activate the kill switch (firewall) and the leak prevention under the ‘Firewall and DNS’ settings.
Perfect Privacy’s app appears outdated, but they are simple to use when you get used to them. Unlike most VPNs, which feature a single big connect button, every server of this VPN has an independent connect switch. You need to disconnect from one to connect to another manually.
Moreover, the macOS is the only exception with a single connect button, but it appears outdated and needs an upgrade. On the other hand, when the desktop app is minimized, it reverts itself to the system tray, which can be annoying when attempting to navigate the app. The main issue in usability is the lack of a native app for iOS gadgets. We recommend using a top-tier VPN with custom apps for iOS, such as ExpressVPN.
OpenVPN Connect App
You can install This mobile app on Android and iPhone systems.
You can use it to connect to Perfect Privacy on your mobile device. The app is well-rated. It has a 3.9 in the Apple store and 4.3 in Google Play.
Perfect Privacy alternatives
- NordVPN: This VPN offers a wide range of privacy, security, and convenience features. Its security features include DNS leak protection, ad-blocking, a VPN kill switch, and robust encryption. Also, privacy features include anonymous payments, a strict no-logging policy, and a commendable privacy policy. For convenience, NordVPN offers dedicated P2P servers, up to six simultaneous connections, and native apps for all major platforms.
- ExpressVPN: It has a great reputation for excellent security and privacy practices. Their servers use volatile RAM memory to ensure user privacy, ensuring no logs remain on the system hard drives. This VPN is more expensive than most, but it offers excellent speeds and security, as well as the ability to unblock sites even when used in China.
- Private Internet Access (PIA): PIA provides an extensive network and coverage, enabling it to prevent server congestion, slow speeds, and VPN bans. It also offers decent and consistent speeds, making it ideal for streaming, gaming, and torrenting. In addition, the VPN employs robust security and privacy features like encryption levels and protocols that you can simply customize to match your needs.
- Surfshark: Surfshark is a great budget-friendly option when looking for Perfect Privacy options. The VPN subscription is as low as $1.99/month. It works with all major streaming services and supports secure protocols. You can set up unlimited simultaneous connections, and its strict no-logs policy makes it perfect for countries such as China.
Do we recommend Perfect Privacy? Our verdict
Perfect Privacy is an excellent VPN that works well on almost every operating system. It does protect privacy and anonymity successfully without any data leaks, and the company is reliable.
You should choose to subscribe to Perfect Privacy if you like the following things:
- A company based in a country with no retention laws, like Perfect Privacy, is in Switzerland
- No data logging
- Multi-hop data routing
- A kill switch
- High speeds when using Macintosh computers
You should stay away from this VPN provider if:
- High performance in Windows is crucial for you
- You want to stream Netflix and other similar platforms
- You are looking to save money
We hope you will find this article helpful as you try to figure out the best VPN provider for you to get now and in the future. Happy (and safe, anonymous) surfing!
FAQs
No. It only works with HBO Max. Perfect Privacy does not work with major streaming services such as Netflix, BBC iPlayer, Amazon Prime, and Disney+. If you are looking for a perfect Netflix VPN, then your top choice should be ExpressVPN. It supports more than 65 streaming services, including Netflix.
Yes. Perfect Privacy servers support P2P traffic in more than 21 countries, and they work well with major torrenting apps like Vuze and qBittorrent. Its port forwarding feature enables a seamless peer connection for faster download speeds. ExpressVPN is superior to Perfect Privacy due to its more than 3000 servers that support torrenting. It is also faster and easier to use compared to perfect Privacy.
No, a Perfect Privacy iOS app is yet to be introduced. However you can set it up manually, but it could be disappointing and time-consuming. We recommend ExpressVPN for iOS users.
Yes, because it offers robust security features such as a kill switch, bank-grade encryption, and a no-logs policy that Dutch authorities have proved. Other features that make it safe include servers that only utilize RAM, which ensures data is deleted after each server reset, and outstanding forward secrecy, which changes the encryption key for each session to prevent hackers from accessing past or future encryption keys. ExpressVPN is considered a better option than Perfect Privacy because it offers similar security features but provides better value in terms of its ability to work with top streaming sites, faster speeds, and more user-friendly apps.
