A computer virus is a type of malicious software program designed to disrupt normal operations, steal information, damage files, or even give hackers remote access to your device.
They usually spread through infected files, downloads, email attachments, or hacked websites. Like biological viruses, computer viruses quickly move from one device to another. A virus infection on your device can result in normal annoyances to devastating data loss and financial damage.
Knowing your enemy well is the first step to winning a fight. Computer viruses won’t go away anytime soon, but you can arm yourself with the right knowledge and tools (antivirus and VPN) to stop them before they do any damage to you.
This article explores everything you need to know about computer viruses and how to keep yourself and your devices safe.
What is a computer virus?
It’s a type of malicious program or code that is designed to affect or alter the way a computer works. Think of a computer virus like its biological namesake. A common cold virus, for example, needs a host to live, replicate, and spread around the body and eventually to other people. It’s the same for a computer virus. It cannot operate on its own—just like parasites, but one for the digital world.
To survive and replicate, the computer virus needs to attach itself to a legitimate host program or, in some cases, a document that executes code. For instance, it might latch onto your operating system files or even a harmless-looking spreadsheet.
Once you open the target file or run the program, the virus will spring into action. It may spread throughout your entire system, stealing data, logging keystrokes, damaging your system, sending spam emails, or creating chaos. It’s a serious matter, actually.
How does a computer virus work?
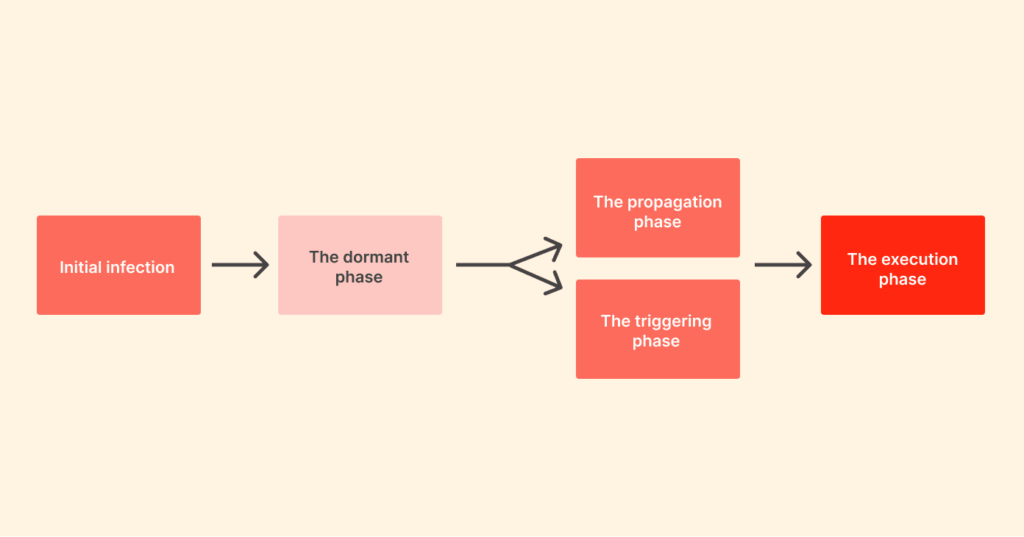
A computer virus works in a peculiar cycle with stages that are predictable. And for you to break the chain and stop the infection dead in its tracks, you need to familiarize yourself with this cycle:
- Initial infection: The virus needs to first get into your device (PC, laptop, etc). This often happens when your device comes in contact with digital content that is already infected. As we have first mentioned, a file download, opening an email attachment that contains a virus, or simply clicking on a malicious link.
- The dormant phase: Just like a typical biological virus, the computer virus has a dormant phase. This is when the virus is lying in wait, attached to the host file. In this case, it is not yet active and cannot cause any damage. It’s just…there. Waiting for a trigger before it strikes.
- The propagation phase: This is when the virus begins to replicate. Immediately you execute the host file, the virus will secretly start to copy itself into other files, programs, or even other system areas. By doing this, the virus is trying to spread as far as it can before you find out. This is why early virus detection is very crucial.
- The triggering phase: Now, all it needs is a specific event—maybe a certain date, user action, or a command from the person who created it—for its payload (the destructive part of the code) to become active.
- The execution phase: This stage is when the payload has been delivered, and then the results start to show. This can be harmless pranks or very serious damage, like stealing your data or corrupting your system.
The information above clears why it’s not good to open files you receive unexpectedly or from unknown sources, right? Without knowing, you might just be triggering the first step of a much bigger problem.
What causes a computer virus?

Hackers design computer viruses mainly to cause damage, gain access to people’s computers, or steal information (without consent). These threat actors write malicious code capable of getting into your computer, altering how it works, and eventually spreading to other devices.
A lot of people invite viruses into their computers without knowing. Some common causes of computer viruses include:
- Opening email attachments from mystery senders you don’t know.
- Downloading software from sketchy websites.
- Clicking on questionable links or pop-ups.
- Using external storage devices or USB disks that are infected.
- Not updating your software or operating systems regularly.
What’s the scariest part? If a virus gets into your system, it can stay hidden for weeks, even months, before showing any symptoms.
How do computer viruses spread?
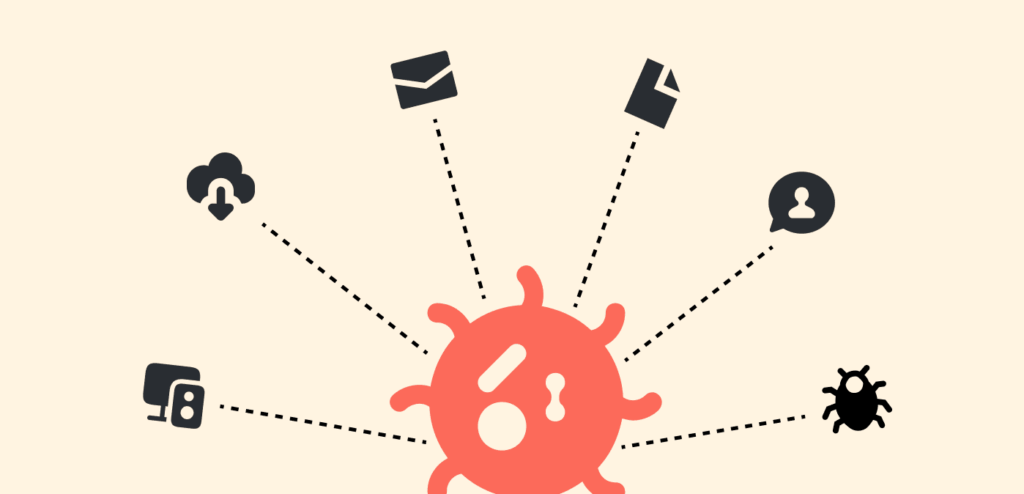
Computer viruses don’t just appear out of thin air or get into your system from nowhere. Instead, people unknowingly help them spread. The way hackers spread viruses keeps getting more complex by the day. In those days, they spread through floppy disks (remember those?). Now things have gotten more serious. Some common means hackers spread viruses include:
- Removable devices: The use of USB sticks, hard drives, and other forms of portable storage allows to transfer of an infected file between computers.
- Unverified downloads: Any free software, media files, or browser extensions downloaded from a suspicious site may contain a virus through the installer.
- Email attachments: Malicious files disguised as invoices, reports, or other common documents will land in your inbox and run harmful code when you open them.
- File-sharing sites: Peer-to-peer sites or torrent sites are full of infected content. That “free” movie or software will cost you more than you bargained for.
- Messaging apps: Viruses are now turning into messages shared through WhatsApp, Facebook Messenger, and other social apps, which also makes mobile devices vulnerable.
- Malicious ads (malvertising): Cybercriminals inject malicious code into ads on unauthorized (hacked or slightly misspelled) sites; one wrong click and you’re infected.
Types of computer viruses
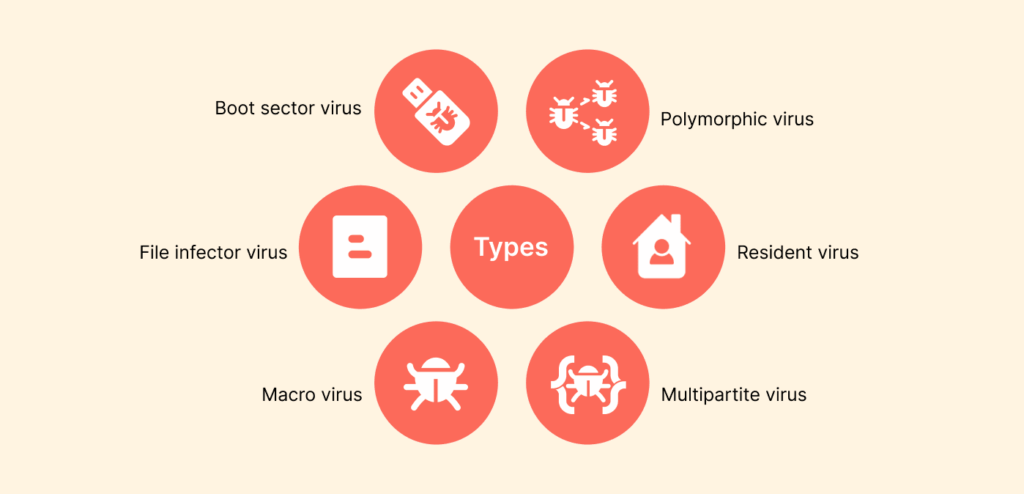
Computer viruses have different types; each of them has its own specialty. Getting familiar with them can go a long way to help you identify the risks on time. Let’s take a look at some of the main (common) types:
1. Boot sector virus
A sneaky type of virus that infects your computer’s master boot record, the first thing that your system reads at startup. It is particularly vicious because it activates once you boot your computer, and it is very hard to remove. It can take control even before your antivirus loads.
- How does it spread: Infected USB drives that you plug into your computer during startup.
- What damage can it do: Completely disable the boot process on your system.
2. File infector virus
Another common virus that attaches itself to executable files (mostly .exe or .com files). Each time you run a compromised program, the virus is triggered, and it could even transfer to other files as well.
- How does it spread: Infected downloads, email attachments, or file transfers.
- What damage can it do: It corrupts critical system files or deletes important files.
3. Macro virus
Created with the same programming language that applications such as Microsoft Word or Excel use, macro viruses hide in document macros and activate once you open the document.
- How does it spread: Email attachments disguised as valid documents.
- What damage can it do: Steals data, corrupts files, or installs other malware.
4. Polymorphic virus
It is also known as the shape-shifting virus. While it is replicating, it changes its code signature, making it very hard for regular antivirus software to detect.
- How does it spread: In many ways, it constantly searches for ways to avoid detection.
- What damage can it do: It can hide for a long period of time, corrupting files without you knowing.
5. Resident virus
It inserts itself into your computer memory and remains active even when you close the original infected program. Resident viruses can infect new files and programs when you use your computer.
- How does it spread: Infected applications and system files.
- What damage can it do: Continuous infection of new files, degrading your system.
6. Multipartite virus
Multipartite viruses employ a combination of two techniques. In the first one, it infects both program files and boot sectors simultaneously. While the second utilizes more than one vector at the same time. This allows them to spread very quickly and is very difficult to eradicate.
- How does it spread: Various modes of infection make them very aggressive.
- What damage can it do: Quite difficult to completely remove.
7. Browser Hijacker
These are technically not viruses, as they cannot replicate. Browser hijackers are entities that can take control of certain browser settings and redirect you to malicious sites.
- How does it spread: Typically bundled with downloaded free software.
- What damage can it do: Invades your privacy and exposes you to further malicious software.
8. Network virus
These viruses can infect every single device on a network and spread quickly through any connections that could occur across the network.
- How does it spread: Taking advantage of network configuration and shared resources.
- What damage can it do: Cripples entire organizational networks.
9. Web scripting virus
A web scripting virus can exploit the code that exists in your web browsers. If your machine visits an infected website, the virus will override the security of your browser, and it can take over your browsing session, steal cookies, or do things while impersonating you.
- How does it spread: Exploiting vulnerabilities in users’ interaction and websites, infecting systems while visiting malicious pages.
- What damage can it do: Redirects to malicious links, steals personal and sensitive information, and exposes you to other dangers.
10. Direct action virus
It is the opposite of a resident virus. It does not hide in memory; instead, this virus resides in a particular file type (such as .exe or .com files). Direct action virus only executes when you run that file. The virus payload is delivered immediately (rather than later from memory), and it is often easier to find and remove.
- How does it spread: It attaches to an executable file (.exe or .com file) and then replicates when that file is run or executed.
- What damage can it do: Corrupts files, loss of access to files, and slows down your systems
Example of threats mistaken for computer viruses
People often refer to all cyber threats as viruses. But the truth is: Every digital threat is technically not a virus, but that doesn’t make them any less dangerous. Knowing the difference will help you to become better at defending yourself against each of them.
Let’s take a look at some common threats that people often mistake for computer viruses:
1. Worms
A worm is more like a virus on steroids. What’s the difference, we hear you ask. A worm does not need a host file, nor does it need human interaction to spread. They are a standalone program that auto-replicates, taking advantage of vulnerabilities in a network to spread from computer to computer.
That’s why worms are very dangerous for creating widespread and rapid damage across the internet.
2. Trojans
Named after the mythological Trojan Horse, Trojans masquerade as legitimate software applications. You’ll believe you are downloading a free game or useful tool, not knowing that what you are doing is inviting a threat into your computer (hides itself behind the legitimate purpose).
Unlike other types of malware, such as viruses or worms, Trojans do not replicate. Their job is to get into your computer without authorization for other forms of malware to use or to directly steal your data.
3. Ransomware
This is a modern and very vicious threat. Ransomware encrypts all files on your computer or network, effectively making them impossible to access. The attackers will then demand payment of ransom (usually in cryptocurrency) to release the decryption key.
Paying is also risky. Even if you agree to pay the ransom, there is no guarantee you will get your files returned, and it only serves to encourage the criminals. (To get a keen knowledge and ransomware stats over the last few years, read our guide here.
4. Spyware
As the name implies, spyware’s job is to spy on you. It hides on your device and collects your data in the background without your knowledge; your keystrokes (passwords, credit card info), browsing habits, messages, etc.
The intent is often to steal your identity or financial information for monetary gain. However, you can use helpful tools (mostly free) to remove spyware from your device and protect yourself from this threat.
5. Adware
Although not necessarily malicious, adware is quite annoying. Its function is to automatically pop up unwanted advertisements on your screen. They make you see endless pop-ups, change your browser homepage, or redirect your search results.
The worst part? Some adware can come bundled with spyware that tracks your activity.
Signs your computer has a virus
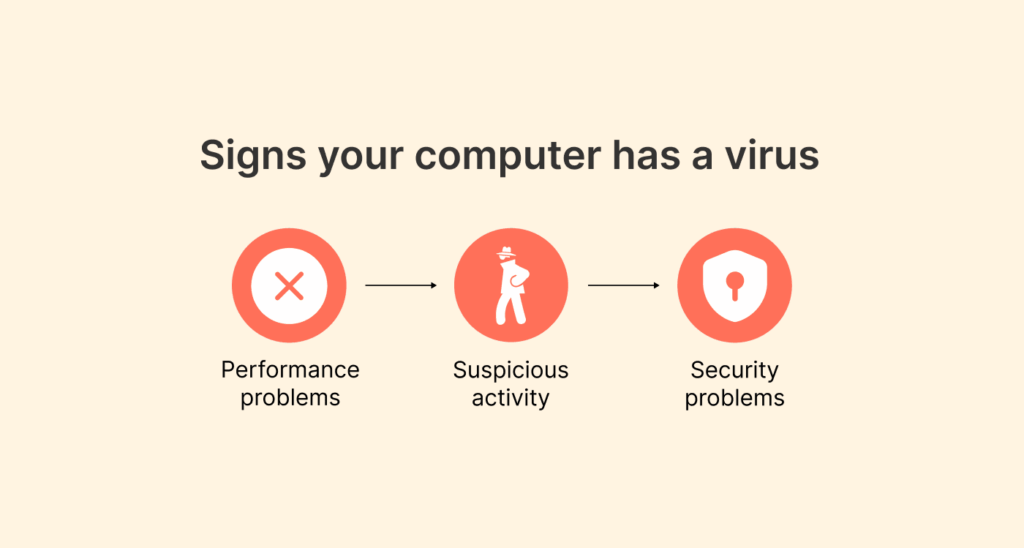
Just like how your body gives you signs and symptoms that you have an infection, your computer usually gives you warning signs when it’s infected as well. Don’t ever try to ignore any of these symptoms:
Performance problems
- Slow operation: Tasks that were fast suddenly feel sluggish and take forever to complete.
- Unexpected crashes: Your computer freezes or automatically restarts.
- Booting is slow: It now takes so long for your system to boot up.
Suspicious activity
- Frequent pop-ups: Annoyingly, unwanted ads (mostly for fake anti-virus software) will be appearing on every website you visit.
- Home page gets hijacked: The default home page of your browser or search engine changes on its own without your permission.
- Mystery programs: Software you didn’t install appears on your desktop or your programs list.
Security problems
- Password issues: Suddenly, you become locked out of accounts that you have used for many years.
- System settings changes: Your system settings change on their own.
- Network nightmare: You start noticing unusual activity on your network, or your internet behaves unusually.
If you notice more than one symptom at the same time, then you’re likely dealing with a viral infection. Do not delay; do something fast!
How to prevent a computer virus

Computer viruses have a history of distraction. Now that we have discussed the problem, it’s time to explore how to eliminate these threats and stay safe. As we know, prevention is better than a cure.
Let’s look at how you can build up your digital immune system and stay virus-free:
1. Use trusted antivirus software
First of all, don’t ever go online without protection. Using a robust antivirus software (like Norton AntiVirus Plus or Bitdefender) is your very first line of defense. It automatically checks for threats and blocks any malicious activity in real time.
Note: You may find free antivirus solutions, but premium antivirus solutions usually provide better protection, update faster, and have additional security features. We curated a list of the best (premium) antivirus in our this article.
2. Enable automatic scanning
Having a reliable antivirus automatically scans email attachments and files before you download. Enabling automatic scanning helps you stop potential threats before they can execute and cause any damage.
Smart tip: You want to schedule your full system scans to occur during non-peak times (overnight, for example) so it can check and catch any threats that may have slipped through.
3. Keep software updated
Infuriating update notifications are usually security patches that close holes hackers like to exploit. Most software has the option to configure automatic updates. Make sure you are using it on your operating system, browsers, and all your other software.
Note: Many of the major virus outbreaks took advantage of vulnerabilities that had already been patched; the victims simply didn’t install the updates.
4. Monitor your email like a hawk
Email attachments are the most common infection vector. Use the following checklist to keep your device safe:
- Never open attachments from unknown senders if you do not know who it’s from; it’s probably not worth risking getting infected.
- Always verify with a known contact to know if the unexpected attachment is from them before opening it.
- Be suspicious of just about anything that has a sense of urgency or threatens you in any way.
- Scan all attachments with your antivirus before opening them.
5. Be careful where you download from
Only download software from the ‘official’ source (from the developer’s website, or a known platform, like Microsoft’s Store, Apple App Store, etc.). Avoid downloading anything from the following sources:
- Any torrent sites/file sharing sites.
- Any “free” version of paid software is just thrown together on some random website.
- If software appears too good to be true, it likely is.
Think about this golden rule: if you wouldn’t buy it from them in person, don’t download their software.
6. Backup your files regularly
And look, even if you do everything right, things can still get bad. That’s why backing up your stuff isn’t just a “maybe.” It’s survival.
The 3-2-1 rule is clutch: three copies, two different types of storage, and one offline or in the cloud.
7. Use secure password practices
Most virus infections lead to compromised accounts. You can avoid this risk by:
- Creating a strong and unique password for each of your accounts.
- Using a password manager to generate strong passwords or store them.
- Enabling two-factor authentication on your important accounts.
8. Be careful with removable media
A USB drive you pick up in the parking lot? Don’t plug it in; scan any external devices always with your antivirus software before you open their content.
9. Keep pop-ups at Bay
Don’t click on pop-ups (especially those that claim your computer is infected or want to give you a “free” scan for security purposes). They are often nothing more than virus delivery methods disguised as helpful warnings.
10. Use a VPN
A VPN is one of the mandatory tools to use to stay away from online threats. Some VPN services come with an adware and malware blocker (for example, NordVPN has Threat Protection, which blocks trackers, ads, and malware), helping you remove viruses and malware, hide your online activities, and keep you and your device protected.
What to do if your computer gets infected

Even with the best precautions, infections can still happen. Here is an emergency response plan for a computer infection. (For mobile devices, our virus removal guide for iPhone and Android covers a similar process.)
1. Do not panic (but act fast)
The quicker you react to a potential infection, the less the damage. So, first things first, disconnect yourself from the internet to stop data from being stolen and stop the virus from spreading to other devices.
2. Run a full system scan
Then, launch your antivirus software and perform a full scan of your system. Several antivirus software programs, like Norton, Kaspersky, and Malwarebytes, have special virus removal tools specifically for dealing with stubborn infections.
3. Boot from external media
If your computer is not starting normally, then boot it from a rescue disk or USB stick that has an antivirus. This way, you can scan your system and your antivirus can do its thing without interfering.
4. Consider professional assistance
If you have a serious infection such as ransomware or financial malware, you should take your computer to a trusted repair service. Some infections will need special techniques for removal.
5. Restore from backup
If something nasty wrecks your system, sometimes you’ve just got to nuke the hard drive and start fresh from a clean backup. Annoying? We know that. But this is exactly why having backups is non-negotiable—nobody wants to lose years of photos or shell out cash to some loser with ransomware.
6. Change your passwords
Once you have succeeded in removing the infection, you should change the passwords to all of your important accounts, particularly banking and email accounts. The virus may have logged your username and password.
FAQs
People keep mixing up ransomware and viruses like they’re the same, but no, they’re not, maybe cousins at best. Ransomware sneaks in, locks up your files with some fancy encryption, and then hits you up for cash if you ever want to see your stuff again. It spreads around like a virus, for sure, but it doesn’t make carbon copies of itself everywhere like a classic virus does.
Trojans are malware simulating real software. Trojans cannot replicate and self-replicate like a virus, although they are definitely quite dangerous; they are not a virus in the precise sense.
Yes, Apple Mac can certainly get viruses and malware, too, contrary to popular belief. While Mac devices get infected with malware and viruses less often than Windows computers, they are still immune to viruses. Also, the number of Mac-specific threats is increasing every year.
You should do quick scans every day and a full system scan every week. To save time and not get infected at the same time, allow your antivirus software to deal with the day-to-day scanning automatically using real-time protection.
Today, there are many antivirus programs that are designed to impact system performance minimally. If an antivirus software is slowing your computer down significantly, you should change to a better quality antivirus program.
Yes, of course. It’s called “drive-by downloading,” and honestly, it’s as shady as it sounds. Sometimes, even just loading the wrong page can start sneaky downloads in the background without you even clicking anything. So keep your browser up to date, and maybe use a script blocker unless you want to roll the dice with your digital life.





