Have you ever heard of a situation where a cyber attacker withholds or threatens to destroy an individual or organization’s critical data unless they pay up? That’s a classic ransomware attack; it’s basically virtual kidnapping. During an attack, your data is ‘kidnapped’ until you pay the ‘kidnapper’ a ‘ransom’ to release it.

Unfortunately, these attacks are widespread and on the rise daily, with more people depending on the Internet for their daily activities. This article will list critical ransomware statistics worldwide.
Quick list of top 10 ransomware statistics
- Ransomware victims paid attackers $449.1 million in the first six months of this year.
- The total cost of ransomware attacks in 2023 could hit $898.6 million.
- Ransomware attackers extorted about $939.9 million from victims in 2021, making it the biggest year for ransomware revenue.
- As of August 2023, over 72 percent of businesses globally were affected by ransomware attacks.
- From 2018-2023, more than half of businesses worldwide suffered ransomware attacks yearly.
- In the first half of 2023, ransomware attacks accounted for almost a quarter of cyberattacks, with 24% amounting to millions.
- In 2023, the average ransomware attack reached $5.13 million, indicating a 13% increase from the 2022 figure.
- On average, it takes about a year to detect and contain a ransomware attack.
- One ransomware group, LockBit, is responsible for almost half (45%) of the total ransomware attacks in the first half of 2023.
- The percentage of ransomware attacks resulting in the victim paying slumped to a record low of 34% in the second quarter of 2023.
Key ransomware attack trends

As the above list shows, the attacks are on the rise, and there is no sign of falling. In 2021, Gartner stated that the top emerging risk facing organizations was the threat of new ransomware models, which has proven true. Amid this rise, these trends can be seen in the attacks.
1. Double extortion is on the rise.
Some years ago, ransomware groups encrypted their victim’s data and sought a ransom in exchange for a decryption key. This action was often carried out by single extortion. However, in recent years, these groups have begun performing double extortion attacks. That is, they store victims’ data in offsite locations before encryption and threaten to leak it if they don’t receive a ransom within a specific period.
That means these groups hold a double threat (data encryption and data leak) over their victim. More attackers are leveraging this method as it’s proven to generate greater profits.
2. Ransom demands are on the rise.
According to IBM, the average ransomware attack in 2023 cost $5.13 million, indicating a 13% jump from 2022’s average cost of $4.54 million. (ResilientX)
The cost has consistently risen yearly, encouraging attackers to execute more ransomware attacks. The rise in cost has led to a rise in ransom demands.
3. Rise in ransomware-as-a-service.
In years past, home Internet users bore the brunt of ransomware attacks. But as the attackers found their craft more lucrative, they’ve shifted their focus to large enterprise networks in recent years. Hence, the evolution of ransomware-as-a-service, also RaaS, has gained traction.
RaaS is a pay-for-use malware that lets cybercriminals purchase ready-made ransomware tools for large-scale attacks. This malware works like an affiliate program; the creators of the ransomware tools get a percentage of every successful ransom payment.
With RaaS, cybercriminals don’t need technical skills to deploy ransomware attacks. This troubling reality has continued to fuel the threat of cyberattacks in 2023.
4. The education sector has become the largest target.
According to various sources, these attacks are deployed across various sectors of society, but the education sector will be the most targeted in 2023. The attacks have affected multiple parts of the education sector, from K-12 schools to tertiary institutions.
According to a global survey of 3,000 IT/cybersecurity leaders conducted by Sophos, a cybersecurity company, between January and March, 80% of school IT professionals said their schools suffered these attacks last year. That’s up from 56 percent recorded in the 2022 survey.
Likewise, 79 percent of IT professionals in higher education institutions reported suffering ransomware attacks in the last year. The Sophos report of 2023 also revealed that school IT professionals were likelier to report the attacks than IT workers from other industries.
Moreover, Blackfog, a data security company, found education to be the most targeted sector for ransomware attacks in most months of 2023. The company found that, of the 33 publicly disclosed ransomware attacks in January 2023, 11 attacks affected the education sector.
The sector remained at the top of the victim list in March, May, June, and August. At the beginning of August 2023, St. Landry Parish Schools in Louisiana, US, announced experiencing a ransomware attack. Medusa, the ransomware group behind the attack, demanded a $1 million ransom to remove the compromised data.
Ransomware statistics by year (2021-2023)
As stated earlier, ransomware attacks are a fast-growing cyber threat, increasing yearly with no apparent end. The rise in attacks is expected to hold in 2023 and beyond. Here are insightful ransomware statistics for 2023 and more.
- Ransomware victims paid attackers $449.1 million in the first six months of this year. For context, the figure victims paid in 2022 was not up to $500 million. (Chainalysis)
- The total cost of ransomware attacks in 2023 could hit $898.6 million if the year’s pace of payments holds. (Chainalysis)
- Ransomware attackers extorted about $939.9 million from victims in 2021, making it the biggest year for ransomware revenue. (Chainalysis)
- As of August 2023, over 72 percent of businesses globally were affected by ransomware attacks. This percentage shows an increase from the prior five years and was the highest figure reported. The ransomware statistics graph below tells the full picture. (Statista)
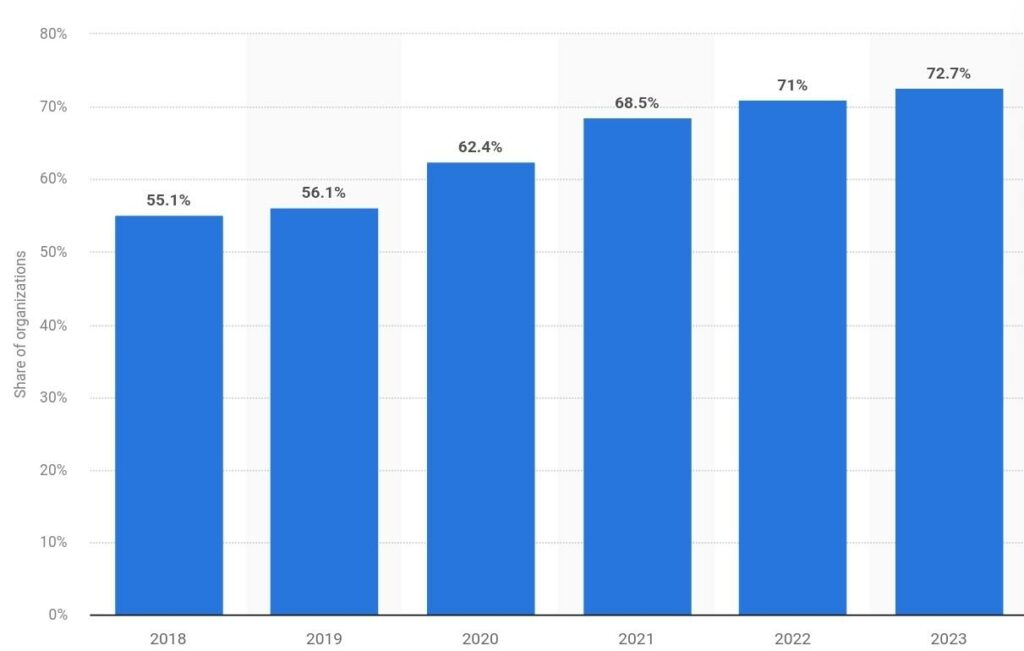
Businesses worldwide affected by ransomware (statistics for 2018-2023)
- From 2018-2023, more than half of businesses worldwide suffered ransomware attacks each year. (Statista)
- Verizon statistics for data breaches in 2022 stated that in the first half of 2023, ransomware attacks accounted for almost a quarter of cyberattacks, with 24% amounting to millions (SC Media).
- In 2023, the average ransomware attack reached $5.13 million, indicating a 13% increase from the 2022 figure. (IBM)
- On average, it takes about a year to detect and contain a ransomware attack. That means ransomware attacks are expensive and time-consuming, resulting in further financial costs. (IBM)
- One ransomware group, LockBit, is responsible for most ransomware attacks in the first half of 2023. This figure indicates that the group has remained the most active ransomware attacker since the second half of 2022. (Trend Micro)
- The percentage of ransomware attacks resulting in the victim paying slumped to a record low of 34% in the second quarter of 2023. (Statista).
- In the first quarter of 2023, 45 percent of ransomware attacks in organizations resulted in a ransom payment worldwide. (Coveware)
- The average ransom payments rose more than twice between the first and second quarters of 2023. Ransom payments went from almost $328,000 in the first quarter of 2023 to over $740,000 in the year’s second quarter. (Statista)
- Working with law enforcement significantly reduces the time to identify a ransomware breach. Specifically, law enforcement involvement could result in identifying an attack 33 days shorter, amounting to 273 days in total, compared to 306 days without help. (Halcyon)
- The mean time to contain a ransomware breach is 63 days, 23.8 percent shorter when law enforcement is enlisted, as opposed to 80 days without their involvement. These numbers indicate that law enforcement collaboration can provide significant cost reduction and duration of a ransomware attack. (IBM)
- About 1 in 3 ransomware attacks begin with email phishing. (Coveware)
- During April 2022 and March 2023, most ransomware attacks targeted the US, an economic giant. The UK is far behind in second place, followed closely by Canada, Germany, and France, respectively. (Malwarebytes)
- In the first half of 2023, there were 1,461 victim announcements, but only 500 database leaks were registered, accounting for around 30%. (SOCRadar)
- Ransomware attacks are expected to occur at a rate of one every two seconds by 2031, with global costs crossing $265 billion. (Cybersecurity Ventures)
- In 2022, about 68 percent of reported cyberattacks worldwide were ransomware. (Statista)
- Almost 155 million ransomware breaches were identified in the fourth quarter of 2022. (Statista)
- As of 2023, Austria and Singapore had the highest share of companies that faced ransomware attacks. (Statista)
- In the second quarter of 2023, Black Basta and BlackCat were the leading ransomware variants, accounting for a market share of 15.5 percent. (Statista)
- Stop/Djvu Trojan was number one on the list of the most commonly encountered ransomware Trojans in 2022, accounting for over 16 percent of encounters. (Statista)
- WannaCry is the second-most used type of ransomware Trojans in 2022 and was encountered by 12 percent of Internet users worldwide. (Statista)
- In 2022, there were 1,829 incidents of ransomware attacks against financial institutions worldwide. There was a sensitive data leak in 477 of them. (Statista)
Ransomware cost and payment statistics
- According to a 2021 IBM Security report, the total cost of a ransomware attack was an average of $4.62 million, excluding the ransom. (CyberArk)
- Education institutions paid $2.73 million to pay ransom and rectify the impacts of ransomware attacks in 2021. This figure was 48% higher than the average for all sectors globally. (Sophos)
- The average ransom payment in the first quarter of 2021 was $220,298, up 43% from the fourth quarter of 2020. (Coveware)
- The average ransom payment in the second quarter of 2021 was $136,576, up 38% from the year’s first quarter. (Coveware)
- The average ransom payment in the third quarter of 2021 was $139,739, up 2.23% from the year’s second quarter. (Coveware)
- In 2021, 32% of ransomware victims paid the ransom, but they ultimately recovered only 65% of their data. (Sophos)
- Approximately 75% of ransomware breaches in the second half of 2021 involved Russia-related ransomware variants. (FinCEN)
- In the first half of 2022, 34% of all cyber insurance claims were ransomware-related. The insurer paid out an average ransom of $255,000 during the same period. (Corvus)
- The average payout by organizations for ransomware attacks increased from $812,380 in 2022 to $1,542,333 in 2023. (Sophos)
- Organizations paying higher ransoms rose since 2022; 40% have reported payments of $1 million or more compared to only 11% in 2022. (Sophos)
- Organizations paying less than $100,000 in ransom slumped to 34% in 2023 compared to 54% in 2022, indicating that the bad guys have become greedier – asking victims to break the bank for ransom payments. (Sophos)
- Companies have spent an average of $1.82 million for recovery from a ransomware attack in 2023. This figure excludes a ransom. (Sophos)
- Organizations with less than $10 million in annual revenue have spent an average of $165,520 to recover from ransomware attacks in 2023. (Sophos)
- Organizations with annual revenue greater than $5 billion have spent an average of $5 million to recover from ransomware breaches in 2023. (Sophos)
- Companies who paid ransom spent about $750,000 in recovery costs, representing twice the amount ($375,000) of what organizations who used backups ultimately paid. (Sophos)
Statistics for attacks by ransomware group
Old and new ransomware groups attack organizations globally every year, including in 2023. However, some groups are more prominent than others.

- LockBit 2.0 perpetrated the highest ransomware attacks in the third quarter of 2021. (Intel 471)
- New ransomware families rose by 26% in 2021, raising 157 families. (Ivanti)
- In 2021, the ransomware group Conti collected the most ransom payments, totaling nearly $13 million. (Atlas VPN)
- The ransomware group REvil/Sodinokibi collected the second most ransom payments in 2021, extorting their victims $12.13 million. (Atlas VPN)
- BlackCat (ALPHV) hit 30 organizations during the third quarter of 2022. (TechRepublic)
- Ransomware attacks from Black Basta affected 50 organizations in the third quarter of 2022. (TechRepublic)
- The number of attacks from ransomware group Hive rose by 188% from February 2022 to March 2022. (TechRepublic)
- LockBit 3.0 was the most prominent ransomware variant of 2022, accounting for 192 attacks in the third quarter of 2022. (TechRepublic)
- LockBit 3.0 impacted 41 countries in 2022, with the US as the top target. (TechRepublic)
- Five groups – LockBit, Royal, Vice Society, BlackCat (ALPHV), and Medusa – have been responsible for the most disruptive ransomware attacks in 2023. (Avertium)
- LockBit was the most prolific RaaS of 2023. (Avertium)
- Vice Society experienced a surge of 267% in their activity in 2023. They’ve primarily targeted victims within the education sector. (Avertium)
- LockBit’s victims are located in 23 countries, representing twice as many countries as any other ransomware group. (Avertium)
- LockBit and Medusa carried out the highest number of attacks in August 2023. (Blackfog)
Ransomware attack statistics by industry

In January 2023, cybersecurity researchers observed 37 industries being targeted for ransomware attacks. However, some industries suffer the attacks more than others.
Education
- In 2021, 88 attacks disrupted operations across over 1,000 schools, universities, and colleges. (Emsisoft)
- Hackers stole sensitive data of employees and students in at least half of the education sector’s ransomware incidents in 2021. (Emisoft)
- The education sector was the second most targeted for ransomware attacks in 2021. (Blackfog)
- Education accounted for 30% of ransomware breaches in 2022, totaling 1,241 data breach incidents (Verizon)
- In 2022, the education sector witnessed 282 confirmed cases of data loss or disclosure. (Verizon)
- Lower education (56%) and higher education (64%) suffered increased ransomware attacks in 2022. (Verizon)
- In 2022, it would cost an average of $1.42 million for higher education to recover from ransomware breaches and $1.58 million for lower education to recover. (Verizon)
- In the first half of 2023, the education sector topped the victim list of ransomware attacks among all industries. (Blackfog)
Health
- In 2021, healthcare experienced the third-highest ransomware attacks by industry. (Blackfog)
- As of 2022, the healthcare sector experienced the greatest average cost of any industry at $10.1 million per ransomware attack for the past dozen years. (IBM)
- In 2022, the healthcare sector suffered more ransomware attacks targeted at personal data than medical data. (Verizon)
- Universal Healthcare Services let go of $67 million in labor expenses, recovery, and lost income due to ransomware attacks (IBM).
- In 2022, 36% of healthcare centers reported a rise in medical complications due to ransomware attacks. (Herjavec)
- Ransomware targeted one in 42 healthcare companies in the third quarter of 2022. (Checkpoint)
Government
- In 2021, government infrastructure suffered ransomware attacks three times the previous year’s figure. (SonicWall)
- There were approximately ten times more ransomware attack attempts than average on government infrastructure in June 2021. (SonicWall)
- Only 38% of local and state government workers have adequate ransomware prevention training. (IBM)
- In 2022, 14 of the 16 US critical infrastructure sectors suffered ransomware attacks, including IT industries, defense, government facilities, emergency services, and food and agriculture. (CISA)
Finance and insurance
- The financial industry spends an average of $5.12 million to tackle data breaches such as ransomware attacks. (IBM)
- Bank of America spends over $1 billion annually fighting ransomware attacks. (CNBC)
- In 2022, victims paid over $602 million in ransom payments using cryptocurrency. (Chainalysis)
- Banks based in the US completed ransomware transactions totaling $1.2 billion in 2022. (CNBC)
- Between 2019 and 2021, 55% of 1,500 insurance claims occurred due to ransomware attacks. (Coalition)
- In 2022, 2,123 insurance claims were due to ransomware attacks. (Coalition)
- In 2022, ransomware breaches accounted for 11% of insurance claims in the Communications and IT sector. (Coalition)
Businesses/Enterprises
- Small businesses suffered 832 incidents of data breaches in 2022. Ransomware accounted for 80% of the breaches, with 130 confirmed cases of data loss. (Verizon)
- Only half of small businesses in the US have a cybersecurity plan, leaving half vulnerable to ransomware attacks. (Provident Bank)
- Almost 40% of businesses had to lay off employees, and another 33% suspended operations temporarily after a ransomware attack in 2022. (Cybereason)
- 80% of businesses suffered another ransomware attack after paying the ransom, while two-thirds (68%) of the companies experienced another attack within a month of paying the ransom. (Cybereason)
Ransomware attack statistics by country
- The US, UK, Germany, Canada, Australia, France, Belgium, Portugal, Italy, and India are the top ten countries affected by ransomware attacks in January 2023. (Avertium)
- The US represents 38.6% of victims targeted by ransomware attacks in 2023. (Avertium)
What is ransomware?
It is software/malware that restricts an organization’s access to its data until there’s a ransom payment. Examples of ransomware include Trojan viruses that extract the content of a folder, save it in a password-protected file, and remove the original data. The victim will only get the password when they have paid the ransom.
Moreover, more sophisticated cybercriminals encrypt an organization’s entire data infrastructure and release the encryption key when the ransom is paid.
How does ransomware work?
It works by restricting an individual or organization from accessing their data. This restriction can happen by moving the data to an unknown location or deploying software that encrypts the data. In either case, the attacker doesn’t lift restrictions until the victim has paid a ransom.
Unfortunately, most organizations are forced to pay due to the fear of further damage from leaking sensitive data such as employee information and intellectual property.
Besides the risk of leaks, some attacks may impede an organization’s ability to function. In this case, organizations have little or no choice but to comply and pay the ransom.
How is ransomware spread?
Ransomware is spread through various means, but the primary method is phishing. Hackers send genuine-looking emails prompting the target to open a link or download a file. If the target opens the link or downloads the file, they will install the ransomware on their device, giving access to the hacker.
Ransomware is also spread through unpatched versions of operating systems.
What is the WannaCry ransomware attack?
The WannaCry ransomware attack was a global attack that rocked the cyber world in 2017. The attack affected over 200,000 computers in more than 150,000 countries. The malicious software, WannaCry, targeted a vulnerability in unpatched versions of the Windows operating system.
The vulnerability was known as ‘EternalBlue’ and allegedly developed by the US National Security Agency (NSA). A hacking group called ‘The Shadow Brokers’ exposed the vulnerability.
Although Microsoft released a new patch that eliminated EternalBlue, many individuals and organizations ignored the patch and were vulnerable to WannaCry, which infected hundreds of thousands of computers globally. The ransomware caused an estimated $4 billion in damages worldwide.
What is DarkSide ransomware?
DarkSide is a hacking group responsible for distributing RaaS. This ransomware emerged in August 2020 and is rented to other hackers (or affiliates) on a subscription basis. The developers collect a percentage of profits gained from deploying the ransomware.
DarkSide has been used for various devastating attacks against organizations in the past three years. On May 7, 2021, the group forced Colonial Pipeline, a major gasoline pipeline across the US East Coast, to halt operations after the ransomware encrypted computer systems.
After the company quickly paid the ransom of 75 bitcoins (approximately $4.4 million), 18 states were put under a state of emergency while they dealt with petrol shortages. Since then, law enforcement agencies have found $2.2 million in Bitcoin linked to cyber criminals using DarkSide ransomware.
How often do ransomware attacks occur?

These attacks occur in quick succession, and they get worse every day. There are 1.7 million incidents every day and 19 attacks every second.
According to Statista, through 2021, there have been 623.3 million ransomware attacks worldwide. In the first half of 2022 alone, there were 236.1 million attacks globally. Although not every attack was successful, the statistics highlight the severity of the ransomware threat.
Even in 2023 alone, these attacks have done some significant damage. For instance, in January 2023, the LockBit ransomware gang linked to Russia attacked Royal Mail and demanded $80 million to decrypt the company’s files.
In February 2023, the oldest federal law enforcement agency in the United States (US), the US Marshals Service, was the victim of a ransomware attack in which hackers stole sensitive data.
The same month, almost 9 million patients were affected by a data breach at the Managed Care of North America (MCNA) Dental, and the attackers demanded a $10 million ransom.
How many people are affected by ransomware?
It’s difficult to ascertain the number of people affected by ransomware, but thousands fall victim to attacks yearly. For example, an estimated 3,700 individuals said they fell victim to successful attacks in 2021.
How many malware attacks were there in 2022?
In the first half of 2022, about 2.8 billion malware attacks happened, including ransomware breaches. By the end of 2022, the number of malware attacks topped 5.5 billion worldwide.
FAQs
Ransomware attacks often happen via phishing. However, there may be other causes, such as weak passwords and poor user practices.
Maintain backups, develop plans and policies to respond to ransomware incidents, connect to only trusted Remote Desktop Protocol (RDP) ports, harden your endpoints, keep systems up-to-date, train the team on security awareness, and implement an Intrusion Detection System (IDS).