Internet usage has increased significantly in the last decade, exposing users to various malicious applications ready to invade user’s privacy. Consequently, personal data leaks (such as photos) and other hacking attacks have increased. An effective way for hackers to access users’ devices and infiltrate them is through a keylogger virus.

They are lightweight, difficult-to-detect spyware applications that record every key you type on your PC or mobile device. These tools relay the logged data to the hacker’s server.
This article will explain what a keylogger is, how it works, and how to stay away from it.
What is a keylogger?
It comes from the family of the Trojan virus. A Trojan would typically mask itself as a helpful application to conduct malicious activities after downloading it sneakily.
The term ‘keylogger’ describes any program that records the keystrokes of a device. It operates secretly by monitoring and storing a user’s keystrokes.
However, there are also keylogging devices that are different from keylogging software. So that brings us to the question of what is a keylogger virus.
Not every keylogger is malicious or a virus. In some cases, legitimate programs also carry out keylogging functions. For example, applications that use “Hotkeys” or help users toggle between different keyboard layouts may not be malicious.
Some organizations also install keylogging software on employee systems to track their activities during working hours. If this is an organization’s general policy, then it is justified and legitimate. Besides, parental control apps may also keylog the devices of the wards.
However, many malicious keylogging applications, such as viruses, also exist and help cyber criminals in espionage and unjustified monitoring.
Thus, no matter the reason for deploying, you should know that such tools can facilitate malicious and criminal intent.
Hardware keylogger
Some keyloggers are embedded in hardware, and you may never suspect them. For example, a mobile manufacturing firm can spy on your cellphone by embedding a keylogger in jacks. The same applies to computers and laptops.
Hardware keyloggers can be embedded in a mouse or joystick and serve as a keyboard overlay.
Did you know that each key’s sound can help hackers determine the keys a user types through an acoustic keylogger? The keyboard overlay records every sound of your keystrokes and associates it with specific keys.
But most cybercriminals and international spying bodies use software keyloggers instead of hardware or acoustic ones, as they are easy to deploy.
How a keylogger works
Once installed on a device, keylogging tools execute immediately after the target user boots the system and runs until shutdown.
Some keyloggers target your activities on specific applications/websites, while others target every keystroke you make, irrespective of what you do.
Most modern keyloggers are lightweight. Hence, they don’t affect the target device’s performance, becoming hard for users to suspect anything wrong and take action. Also, these tools remain hidden in your device operating system, so you cannot usually find them in your list of installed programs.
Sometimes they can embed themselves in hidden browser extensions. Some criminals would poison their websites and infect any device that visits the sites. They help malicious actors steal your personal details and credit card information alongside other secret data.
Keylogging software usually stores your keystrokes on a cloud server or in a small file, which then either gets emailed to the person monitoring your moves automatically or accessed by him via an online dashboard.
Today, not only do software-based keyloggers exist, but many hardware keylogging devices are also available in the market.
How to detect and remove a keylogger

Detecting a keylogger is the first step to ensuring your security. The most effective and easiest way is to scan through the running processes of your system’s task manager.
However, it usually names its process to an unrelated name, making it difficult to identify. Therefore, you should search the names of any new or strangely-named processes running on your system on the internet to spot any malicious processes.
If you find any keylogging or tracking process, disable or stop it from running on your device. Here you go with detailed steps to do so.
- Access your Windows Task Manager. (You can do that either by simultaneously pressing the “Ctrl,” “Alt,” and “Delete” keys and then clicking on “Task Manager” or right-click on your taskbar and click on “Task Manager” from the menu to see.
- Once opened, click the “Processes” tab to view all running processes on your PC.
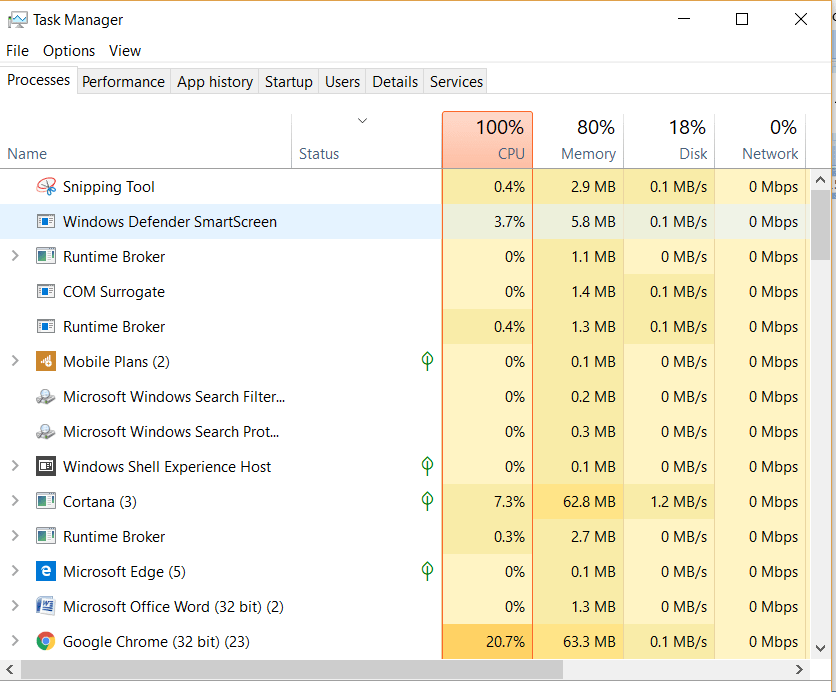
- Check for the names of unusual processes and stop any related to a key logger.
You should also click on the “Startup‘ tab to know the applications and processes that launch automatically when your system starts. This will enable you to determine whether a keylogger is running on your system since it is usually programmed to run immediately after the design starts.
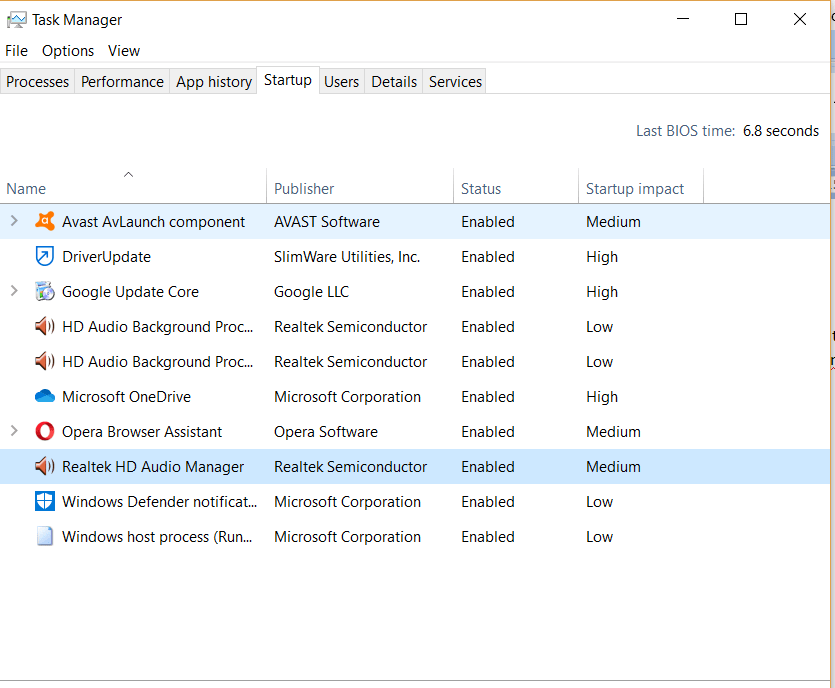
- Right-click on the name of any program you suspect is a keylogger and disable it.
Checking for keylogger through internet usage
Checking your internet usage report also effectively confirms a keylogger’s presence on your system. Follow the steps below.
- Go to the “Settings” menu (press the “Windows” and “I” keys simultaneously to directly open the Settings window, or scroll through the Startup menu to find “Settings“).
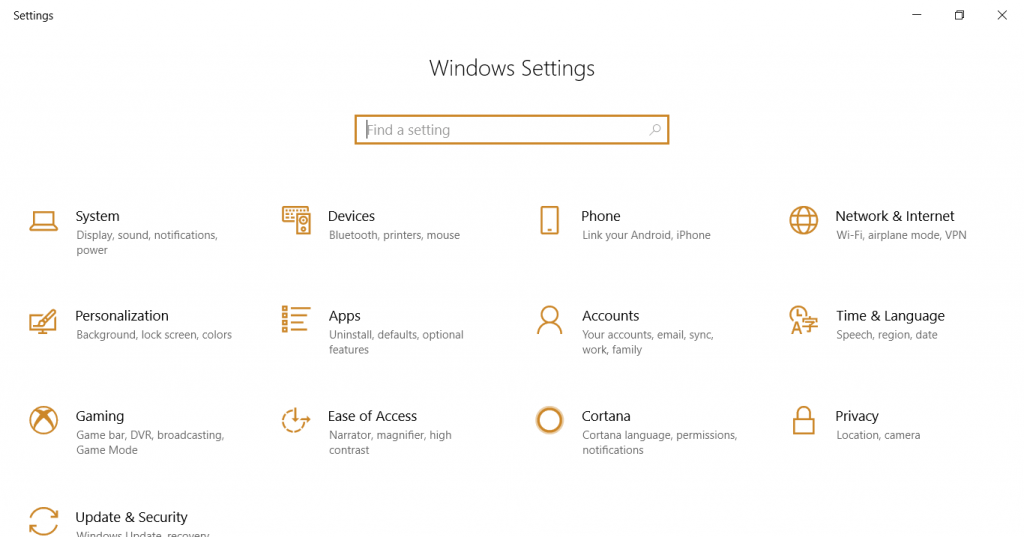
- Click on the “Network & Internet” option.
- Now select the “Data usage” tab.
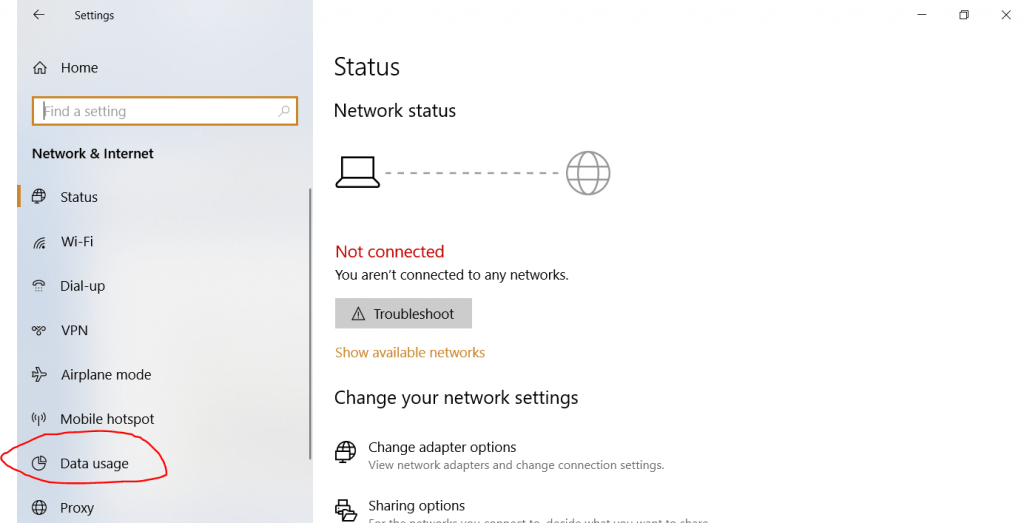
- Click on the “View usage details” option.
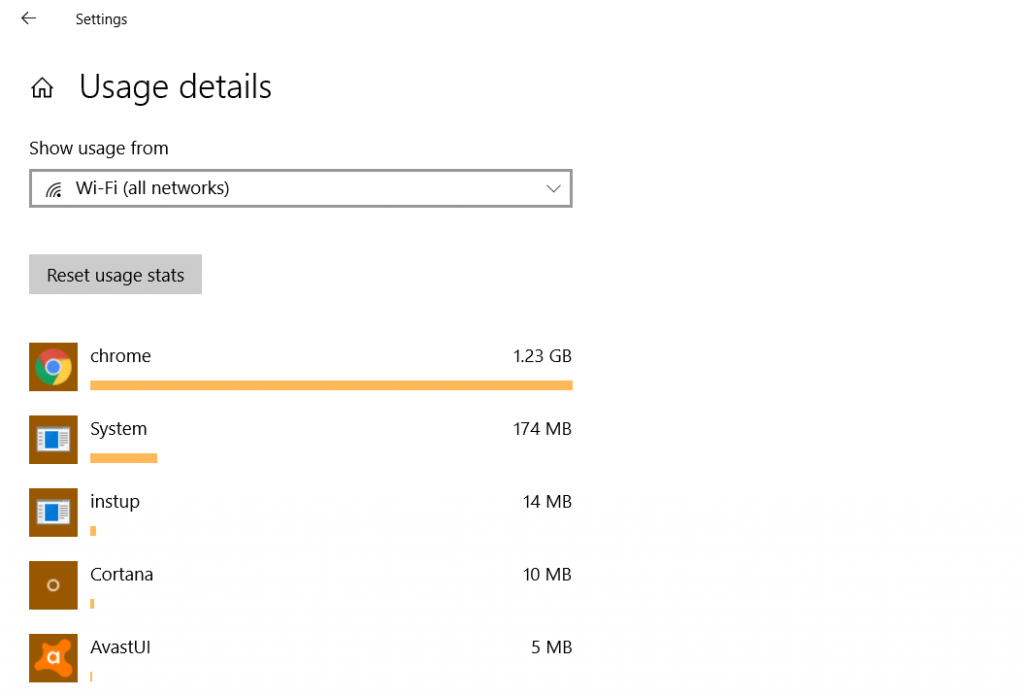
You can now see a list of all applications using your internet resources. Next, search for any unknown program on the internet to determine if it is associated with a trojan.
Looking out for keyloggers in browser extensions
You should also search your browser plug-ins and extensions to determine if they relate to a keylogging tool. You need to get to your browser’s extension list to do that.
Here is how to find the extensions running on major browsers:
- Firefox: Open your web browser and type About: add-ons in the address bar.
- Google Chrome: Open your Chrome and type chrome://extensions into the address bar.
- Safari: Go to the Safari menu option and select “Preferences,” then select the “Manage extensions” option.
- Opera: Locate the menu tab and select “Extensions.” Then click on the “Manage extensions” option there.
- Microsoft Edge: Go to the browser menu and click “Extensions” to find all add-ons.
- Internet Explorer: Go to the “Tools” menu and click on the “Manage add-ons” setting.
Now scan through the list of all extensions and search the internet for extensions with unusual names. If you find any malicious add-on, disable or remove it immediately.
Detecting and removing keyloggers through full system malware scan
System-wide malware scans help you detect the presence of a keylogger on your system and remove it. You should carry out a full malware scan or schedule automatic scans to remain safe from malicious or intrusive applications.
But make sure you use top-notch anti-malware software to sniff out any keylogger.
A reputable anti-malware uses signature recognition and heuristics to recognize malware. It can also detect typical tracking activities, such as capturing screenshots and recording keystrokes to spot any spyware tools and remove them.
Fortunately, you do not need to spend a fortune to get your hands on such programs. Many free malware and spyware removal tools are available to do the job.
20 ways to keep yourself protected from keyloggers
A keylogger is a significant threat to your personal information, such as your emails, passwords, user names, bank card information, and other sensitive details. Losing this data to adversaries can lead to identity theft, unauthorized transactions, and more.
Therefore, make it a priority to keep your devices safe from such data stealers. Use the following methods to prevent keylogging on your PC.
1. Use 2-step verification
Generally, hackers use your username and password stolen through keylogging to log into your accounts and carry out malicious activities.
Therefore, you should secure your online accounts with two-step security verification, known as “multi-factor authentification.”
With two-factor authentication, you receive a PIN on your mobile device for authentication before you can access the account.
This additional verification step prevents hackers from gaining access to your accounts even if they succeed in stealing your login details. The process also notifies you if someone tries to access your account.
We recommend you set up two-step verification for your email, bank log-in, social media accounts, and almost every account you deem important online.
2. System and application updates
System updates are necessary because they automatically eliminate all malicious third-party applications from the operating system, including keyloggers.
Furthermore, a software update also automatically fixes all the existing issues on your device, including security vulnerabilities that may allow hackers to gain access.
Please note that some system updates do not update your web browser. Therefore, you should constantly update your browsers because, like OS, outdated browser add-ons can also lead to hacking and malware attacks.
3. Use encryption software
An encryption application masks your keystrokes, sending the wrong key logs to the hacker. Since encryption scrambles your input, the keylogger won’t track the same keys you typed. This is an added security layer you can apply on your PC for enhanced security.
Axcrypt.net is one encryption software you can use for free on your Mac and PC.
4. Avoid downloading cracked programs
People often look for cheap software alternatives on the internet. However, these apparently free apps can cost your security because hackers often exploit your interest by inserting malicious codes within cracked software to infect your system.
Hence, purchasing or downloading genuine applications from authorized, reputable sites is always better.
5. Install an anti-malware program
All the quality anti-malware programs protect against threats such as Trojans, rootkits, keyloggers, and other spyware applications. Furthermore, they periodically scan your PC, fix hardware and software issues, and optimize your system. Hence, ensure you install it right after buying and setting up a new PC.
Also, ensure the anti-malware program’s virus database definition is updated regularly. An out-of-date anti-malware system may not adequately protect your PC against newer threats.
Many quality anti-malware apps exist in the market today, offering multi-platform compatibility. Hence, you can download any of those robust apps without spending money. One such resilient anti-malware available for free is Malwarebytes Anti-Malware, which runs deep scans alongside daily updates.
6. Start using a VPN
A Virtual Private Network (VPN) provides integrated protection against cyber threats by anonymizing your online existence. It encrypts your internet traffic, preventing snoopers from sniffing your online data. In this way, it also potentially hinders hackers from accessing your keystrokes.
VPN technology is also helpful in the corporate environment, given that organizations are the primary target of cybercriminals.
Nonetheless, ensure you always opt for the best VPN only because most VPN services (especially the free ones) lack credibility. Unfortunately, some services would even log your information and use it for monetizing and other malicious purposes.
7. Exercise caution when opening an attachment
People often go online to download free files and attachments. However, most of the attachments and files you download have malicious applications. Especially those you download through shared networks and drives.
Therefore, you should exercise caution when downloading files on the internet. Ensure you visit only reputable sites to download genuine software.
Besides, be wary of unsolicited, promotional, marketing, spam emails or emails from unrecognized senders. Such emails may carry phishing links and malicious attachments.
Furthermore, be skeptical about the attachments you receive from your friends and colleagues. Some might be poisoned and can install a keylogger on your system.
8. Be watchful for your passwords
You should periodically change your passwords and aim to use strong passwords only because hackers usually trail you for some time before committing malicious activities. Therefore, changing passwords frequently may confuse them.
Also, do not use the same passwords and usernames for all your accounts.
To make your job easy and secure your passwords, consider using the best password manager that offers password encryption.
9. Use of an alternate and virtual keyboard
Try to use a virtual keyboard when logging in to your online accounts. Since keyloggers can’t often detect virtual keyboards, it is handy in protecting your privacy. Not only a virtual keyboard like DVORAK will help protect your keystrokes, but it will also prove beneficial in other ways.
Periodically changing your keyboard layout will prevent acoustic keyloggers from determining the characters through the keypress sounds. These tracking tools use each key’s tone to define your input, and changing your keyboard layout assigns different tones to your keys.
10. Anti-keyloggers
Anti-keylogger program compares all computer files to a keylogger database for similarities suggesting a concealed keylogger. Since anti-keyloggers are designed to identify keyloggers, they are more effective than ordinary antivirus software. This is because some antivirus clients don’t consider keyloggers as malware.
11. Live CD/USB
You can reboot your PC with a protected Live USB or CD to safeguard it from keyloggers. Further, a clean CD ensures no malware and that the OS isn’t infected after starting the system.
12. Network monitors
Reverse firewalls network monitors and alert you whenever keyloggers attempt to establish a connection. As a result, keyloggers won’t send back typed information to hackers.
13. Automatic form filler programs
This can protect you from keylogging by reducing the need to input private information such as passwords. Form fillers let Web browsers input checkout pages and sign in users automatically without using the clipboard or keyboard, eliminating the chance of confidential data being captured.
However, anyone physically accessing your computer can install a program to intercept data in transit on the network or in the operating system. Transport Layer Security (TLS) helps minimize the danger of data interception by proxy programs and network sniffers.
14. Security tokens
If a keylogging attack is successful, you can protect yourself with security tokens and smart cards to prevent replay attacks. Gaining access to private data will need both the security token and the correct password. In addition, an attacker can’t exploit knowledge of a user’s actions on one computer to obtain access to a protected resource on another PC, regardless of what was typed on that machine’s keyboard or mouse.
15. One-time passwords (OTP)
This is an excellent way of preventing keyloggers. Once a password is used, it automatically becomes invalidated. As such, the system asks for a new password whenever you need to log in. Therefore, the method is ideal when using public computers.
16. Keystroke inference software
These programs mislead keyloggers by adding random keystrokes. This leads to more data being recorded, distracting the hacker from extracting crucial keystrokes.
17. Speech recognition
Speech recognition eliminates the need for physical or virtual keyboards. However, the method has limited functionality since the program may have challenges decoding or relaying information to the target software.
18. Handwriting recognition and mouse gestures
Many tablets and PDAs can transform stylus motions into computer-readable text. Besides stylus, mouse motions employ this technique to transform strokes into movements like typing. You can also use light pens and graphics tablets to input these motions like touchpads.
However, the method shares limitations with speech recognition.
19. Macro recorders/expanders
This approach involves using a macro expander or recorder to automate tasks that generally entail typing private information, thus avoiding typing this data directly into the physical or virtual keyboard. The method makes it more difficult for keyloggers to capture private information as they cannot record the keystrokes.
20. Deceptive typing
The technique encompasses intentionally typing slowly, making mistakes, or intentionally pausing while typing to throw off a keylogger. Deceptive typing makes it more difficult for a keylogger to accurately record your keystrokes, making it harder for cybercriminals to gather sensitive data from the keylogger’s logs.
Bonus tip
Finally, you can also use a comprehensive security solution. Protect all your digital devices – smartphones, tablets, PCs, Macs, and any other device used to access the internet. A solution like McAfee can give you all-around system protection such as firewall protection, antivirus system, data protection, and identity manager.
History of keylogging

Keylogging has a long history dating back to the early 1970s, but it has become more prevalent with the growth of personal computers and the Internet. In the 70s, The Soviet Union designed a hardware keylogging device targeting IBM’s typewriters. The Union installed the Selectric bug into electric typewriters in the United States Embassy and Consulate buildings in St. Petersburg and Moscow. The device could track the printhead’s movement by measuring its magnetic field emissions and acquiring sensitive and classified information.
With the advancement of technology, such as the rise of the Internet in the 1990s, keylogging became a popular tool for cybercriminals to steal sensitive information such as credit card details. However, with new technologies, cybercriminals didn’t have to install keyloggers manually. Instead, they targeted devices using keylogger malware.
Today, keyloggers have become more sophisticated, with hackers now targeting businesses, homesteads, and other entities. As recent as 2014, the U.S. Department of Homeland Security issued a warning to hotel businesses following an incident where a keylogger was uncovered in hotels in Dallas.
Further, in 2015, it was found out that a mod for Grand Theft Auto V game had a hidden keylogger. Finally, in 2017, some HP laptops were found with a keylogger.
Why keyloggers are a threat
Keyloggers are dangerous to individuals and organizations. While the malicious program does not adversely affect your computer system, it isn’t suitable for your confidential information. In addition, keyloggers are challenging to detect because they operate in the background and do not typically show visible signs of their presence.
Cybercriminals can install the program on your computer through various means, such as tricking you into installing them, exploiting vulnerabilities in your operating system or software, or through malware disguised as legitimate software.
Once the program is installed, hackers intercept passwords and other personal data entered via the keyboard. As such, they can get your passwords, PIN codes, banking account information for e-payments, email addresses, online gaming passwords, etc. Cybercriminals can process payments, make transfers or compromise your accounts after getting hold of your sensitive information, such as credit card details.
Keyloggers can also be used as tools for political and economic espionage. They can compromise the security of private and public sector companies by helping gain access to confidential and sensitive information.
The manager of Brazil’s Computer Emergency Response Team, Cristine Hoepers, opines that keyloggers have surpassed phishing as the most-used method for stealing confidential information. Keyloggers are becoming more sophisticated and can now track user websites and log keystrokes on sites of interest to cybercriminals.
In recent years, there has been a widespread of keylogging-capable malicious programs. No internet user is immune to cyber criminals, regardless of their status. As such, you should be cautious with your internet activity.
How does a keylogger get on your PC?

Typically, keyloggers get into your system when you visit poisoned websites.
That happens by exploiting a vulnerability in your browser where hackers install keystroke loggers through a webpage script. Then, when you visit a malicious website, it launches.
Another way a keylogger gets into your PC or other device is when someone else deliberately installs it on your machine after gaining physical or virtual access.
A keylogger is secretly embedded in your operating system and can perform all its tasks without getting noticed. It can exploit an infected machine and can sometimes download and install other malware onto the infected system.
You should install a reputable anti-malware application and regularly update your system to prevent this attack. Also, be careful when downloading files from the internet. Visit reputable sites only because many websites potentially carry keylogging software.
Unfortunately, despite cybercriminals’ frequent use of keyloggers, most antivirus programs overlook it. Therefore, opting for a reputable antivirus program with a broad definition of keyloggers in its database is essential. (More on how to protect against them later in this article.)
Do mobile devices get keyloggers?
Yes, mobile devices are prone to keylogging software, too. Although currently, no known hardware keylogger for smartphones exists. However, every mobile device, including iPhones and Androids, is vulnerable to software-based keylogging tools widely available.
A mobile keylogger can capture whatever a user types on the screen, irrespective of the device type. It even records virtual inputs on the screen and tracks all your activities.
You should know that mobile keylogging software typically records more than your keyboard entries. It takes account of your emails, screenshots, images, text, log-in details, and so much more.
Once installed, these malicious programs even connect to your phone’s microphone to record your calls and connect to your camera, network traffic, mobile printers, etc.
But the most dangerous part of smartphone keylogging software is its restriction algorithm that bars you from accessing some websites, such as security sites and antivirus application download portals, obviously, to prevent you from tracing it.
Keylogger construction
The primary idea behind keylogging applications is to get between a chain of events while typing to log user input. In simple words, it works between two phases; when a key is pressed and when it appears on the screen.
Technically, keylogging software would typically intercept DDL functions in the user mode and request information from the user’s keyboard through the SDM (Standard Documented Method).
There are several ways to achieve this, but the typical form is through software and/or hardware bug. This is what defines whether a keylogging tool is software or hardware-based.
Physical keylogging devices are typically small and can be attached to the keyboard or other peripheral devices. Whereas software keyloggers record users’ keystrokes and relay them back to the developers through the Internet.
Other methods include secret surveillance through other hardware such as network devices, mice, joysticks, etc.
How keyloggers spread
Keyloggers are malicious applications that spread the same way as other malicious programs on your computer. They can reach your device.
- Upon opening a malicious attachment from an email or other sources.
- Via P2P networks, especially when you launch a file from an open-access directory.
- Through a web page script that automatically runs on your system when you visit a malicious URL.
- Via other malicious applications.
- By an adversary with physical access to your unsecured device in your absence.
Increased use of keyloggers by cybercriminals

Keylogging software has existed for a long time. Yet, criminals have increasingly used such tools over the last few years. The recurrent cybersecurity incidents, both on a small and large scale worldwide, also hint at the same.
Research carried out by Verisign suggests a tremendous rise in the use of malicious programs with advanced keylogging functionalities. Another study by Symantec indicates that almost 50% of the world’s malicious programs aim at harvesting internet users’ personal data.
Also, a study conducted by Bambenek suggests that keylogging applications infect more than 10 million systems in the USA alone. The possible annual losses stand at an estimated $24.3 million each year.
Did you know the Kaspersky antivirus database currently has definitions of more than 300 types of keyloggers? These numbers do not include those embedded with other forms of malicious applications, such as spyware. That is the colossal extent of keylogging software, and users must take the necessary steps to protect their privacy.
Some devastating real-world keylogging attacks
- In August 2006, hackers stole over $1 million from Scandinavian Bank (Nordea) clients. The imposters sent fake automated emails to bank clients asking them to install the anti-spam application in the attachments. However, the app had a lethal keylogging Trojan ‘Haxdoor,’ that recorded users’ input upon accessing Nordea’s online service. That helped cybercriminals access the users’ information and steal money from various accounts.
- 2004 the most significant cyber epidemic occurred when the MyDoom virus conducted a DoS attack on www.sco.com, rendering it unstable for several months. The worm also attacked anyone who visited www.sco.com with its keylogging functions to harvest credit card numbers and log-in details to steal money.
- In early 2005, the UK police prevented cybercriminals from stealing banking data via keylogging. The attackers planned to steal a whopping $423 million, for which the keylogging Trojan created by then 32-year-old Yeron Bolondi tracked users’ keystrokes for their banking sessions.
- In May 2005, the London police arrested an Israeli couple and charged them with developing malicious keylogging applications used by individuals and organizations to carry out massive espionage. Some companies involved in this crime included Israeli cellular services Cellcom and Pelephone and the satellite TV provider YES.
- During the first quarter of 2006, Brazilian Police raided and arrested 55 people for spreading malicious keylogging applications. The tools were embedded in users’ browsers and activated upon opening a bank’s URL. These miscreants used the stolen data to steal $4.7 million from 200 clients.
- In 2004, a group of young Russian and Ukrainian attackers conducted a massive keylogging attack via malicious emails targeting bank clients in France and other countries. They harvested users’ bank account credentials and used them for money transfers, stealing as much as $1 million within 12 months.
FAQs
Free keyloggers are typically easy to detect, even by using antivirus programs. However, paid ones like realtimeSpy, Sniper Spy, and Win Spy are difficult to detect.
While some keyloggers can record your screen, most only monitor keystrokes.
Yes. Keyloggers work by recording keystrokes, hence when they detect passwords when typing.
Yes, using keylogging on the phone is possible using hardware, software, or firmware-based keyloggers.
Yes, you can stop a keylogger. Standard methods include using antivirus programs, anti-spyware protection, anti-keyloggers, deceptive typing, 2-step verification, encryption software, VPN software, security tokens, use of virtual keyboard and speech recognition software, network monitors, etc.






