Today, the digital world is evolving faster than ever, and so are the threats lurking within it. From AI-powered cyberattacks to stricter global privacy laws, the landscape of online security is shifting in real time. What worked to keep you safe yesterday may not hold up tomorrow.
So, expectedly, large corporations, financial institutions, and government agencies will be significant targets for cyberattacks from 2026 onward (according to recent stats and figures).
This guide explores 28 major online security and privacy trends shaping 2026; from the rise of decentralized identity systems and post-quantum encryption to new challenges in data protection and digital trust.
Whether you’re a cybersecurity professional or just someone who cares about privacy, these trends will help you understand where the internet is headed—and how to stay one step ahead.
An estimate of the data protection and privacy market volume
According to Statista, global spending on cybersecurity and technology risk management will be $87 billion in 2024 (details in the table below), primarily due to three factors:
- As remote work becomes popular, businesses seek methods to provide safe home-based work environments.
- Shift to a zero-trust network access paradigm, partly due to more people working remotely and limited VPN protection.
- Switch to cloud models, where managing the infrastructure gets simpler for businesses.
It’s reported that in 2024, data security grew by $6.86 billion, data privacy by 16.9%, and a combined volume spending of $5,474 million. Following the increasing growth rates in cloud security and application security, the cybersecurity market is undoubtedly expanding at the highest rate.
Table: Global end-user spending (in USD) on information security and risk management between 2021 and 2023
| Market segment | 2021 Spending (millions) | 2021 Growth (%) | 2022 Spending (millions) | 2022 Growth (%) | 2023 Spending (millions) | 2023 Growth (%) |
| Application security | $4,963 | 20.8% | $6,018 | 21.3% | $7,503 | 24.7% |
| Cloud Security | $4,323 | 36.3% | $5,276 | 22.0% | $6,688 | 26.8% |
| Data security | $3,193 | 6.0% | $3,500 | 9.6% | $3,997 | 14.2% |
| Data privacy | $1,140 | 14.2% | $1,264 | 10.8% | $1,477 | 16.9% |
| Identity access management | $15,865 | 22.3% | $18,019 | 13.6% | $20,746 | 15.1% |
| Infrastructure protection | $24,109 | 22.5% | $27,408 | 13.7% | $31,810 | 16.1% |
| Integrated risk management | $5,647 | 15.4% | $6,221 | 10.1% | $7,034 | 13.1% |
| Network security equipment | $17,558 | 12.3% | $19,076 | 8.6% | $20,936 | 9.7% |
| Additional information security software | $1,767 | 26.2% | $2,032 | 15.0% | $2,305 | 13.4% |
| Security services | $71,081 | 9.2% | $71,684 | 0.8% | $76,468 | 6.7% |
| Consumer security software | $8,103 | 13.7% | $8,659 | 6.9% | $9,374 | 8.3% |
| Totals | $157,749.7 | 14.3% | $169,156.2 | 7.2% | $188,336.2 | 11.3% |
Furthermore, the International Data Corporation (IDC) forecasts that the European market will see an estimated 9.4% annual growth, hitting over $66 billion by 2026. The Czech Republic is predicted to have the highest growth in cybersecurity spending in the next three years, followed closely by Belgium, France, Germany, and Switzerland.
Similarly, expanding remote working and high dependence on cloud computing models have supposedly increased the vulnerability to attack surfaces. As such, the Public Administration sector will likely expand the most for the following reasons:
1. Cloud workload protection
As more public administration services move to the cloud, the need for cloud protection will likely increase to ensure the confidentiality and integrity of the data and systems in use.
Businesses and individuals with expertise in cloud security may see opportunities to provide services and solutions in this area.
2. Data security
Data security encompasses efforts to protect sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. Private data includes personal identification numbers, addresses, phone numbers, health records, location, financial data, and other classified information.
Data security will be crucial for maintaining trust and confidence in government institutions and protecting citizens’ privacy.
3. Securing collaboration platforms
Remote work and collaboration in public administration will likely become more prevalent. Consequently, securing communication and information-sharing platforms will be crucial.
Measures to help secure collaboration platforms include access controls, encryption, monitoring and logging, incident response planning, and regular security assessments.
Online security and privacy trends in 2026
1. Increase in ransomware attacks
Targeted ransomware attacks will likely rise as more cybercriminals aim at multinational corporations, financial institutions, and government organizations. In addition, attackers will likely invent new ways to stay ahead of defensive measures put in place by these entities.
Attackers know that their targets often have adequate resources to pay the ransom and more critical data to protect. In 2024, cybercriminals gained advanced techniques, which is why 65% of financial organizations reported ransomware attacks, which is more than the stats of 2023 and 2021.
Hackers can now access cloud storage and threaten third-party providers in many ways, a strategy that could significantly impact user data. As such, the prevalence of these attacks is bound to increase steadily in 2026 and beyond.
2. Heightened user awareness
There has been a growing understanding of the need to secure personal information from third parties. This has been sparked by data breaches at organizations that handle essential personal data, including credit reporting agencies and social media platforms.
This challenge will continue in 2026, necessitating organizations to find ways to build their reputation and image.
3. Improved transparency in data collection and use
The increasing concerns about data privacy and the need for users to gain more control over their sensitive information will drive greater transparency in collecting and processing personal data.
In 2024, we saw more firms communicating clearly with users regarding data rights. Additionally, they will require explicit consent from users to collect and process personal information.
Essentially, firms will provide a clear and concise explanation of what personal data they collect, how they will use it, and with whom they will share it.
4. A cookieless future
Organizations are searching for alternative ways to collect user data, such as device fingerprinting, browser fingerprints, and browser storage APIs like local storage, session storage, and IndexedDB.
Essentially, cookies have become a privacy concern in the last few years due to their ability to collect personal information without users’ consent. Thus, we envision a future where web browsers and mobile applications will no longer rely on cookies to track and target users with personalized ads and content.
In this regard, some structural changes are underway within the advertising industry. For example, Google and Apple have been working on new ways to do the cookie job without cookies for a while.
Additionally, the trend among the major browsers is to end the support for third-party tracking. Though Google Chrome will keep cookies around until 2023, other significant browsers have phased them out already.
So the writing is on the wall. The old way of channeling information about potential online consumers is on the way out.
As cookies become a thing of the past, data-driven businesses might start a race (maybe even a war) to find new methods to farm user data.
So, how helpful will the disappearance of cookies be for privacy? It remains to be seen. Most experts anticipate that as new privacy regulations are enforced and closed-off mobile platforms keep expanding in the digital universe, invasive technology won’t simply disappear. Instead, it will adapt to the new realities and online privacy movements.
But for now, the future of internet usage seems more centered on data rights, creating a trustworthy relationship between individuals and organizations.
5. Increased threat to nations
Sophisticated and destructive cyberattacks will serve as tools of statecraft used to advance nations’ strategic goals. As a result, more countries will turn to contract hackers and Advanced Persistent Threats (APTs) to carry out attacks.
Moreover, cyber technology will likely be used for espionage, disrupt harmony, and interfere with the political stability of other nations.
6. Human error will become a leading cyber threat
Human error will become a leading cause of cyber incidents. For example, phishing, social engineering, and insufficient knowledge and skills in cybersecurity will induce more cyber threats. As a result, cyber incidents will grow as individuals continue to accidentally or unknowingly introduce security vulnerabilities into cyber systems.
Most entities will launch employee training programs to combat human error to educate individuals about cybersecurity and threats. Educational programs will entail security awareness training and simulation of different cyber threats.
7. A rise in supply chain risks and security
Potential vulnerabilities to the world’s supply chain will be more imminent. Today, supply chains have evolved into more complex and difficult networks that are challenging to manage.
In addition, the growing reliance on outsourcing certain activities to third parties will introduce new risks into the supply chain. Vendors and contractors in the supply chain can be weak links (the SolarWinds cyberattack in 2020 is a classic example) as they may not be equipped as organizations in terms of online security and privacy.
To combat this, organizations will embrace comprehensive and proactive approaches, such as a strong security culture that will dictate business ties. Importantly, firms will likely incorporate cybersecurity considerations in their partners’ selection process and decision-making.
8. Adoption of the “zero-trust” security model
The zero-trust model embraces a cybersecurity approach that views all devices, users, and networks as threats until proven otherwise. This contrasts with conventional security measures, which tend to trust internal networks and users by default.
With the increasing cybersecurity threats, the approach will see new rules that require prior verification for all users, networks, and devices before granting access to the organization’s network and resources.
Further, increased limitations will apply based on the principle of least privilege, granting users only the access needed to perform specific duties. This will minimize insider threats by preventing unauthorized access and potential attack surfaces of a network.
9. A shift in MFA perspective
In 2023, multi-factor authentication (MFA) will no longer be a robust standalone solution. Instead, it will be seen as part of the zero-trust security model. The model should embrace behavioral approach analytics to comprehend user behaviors. The analytics should be used to authenticate actions performed using specific details.
Moreover, the MFA debate will be dominated by issues of usability and accessibility. Unfortunately, these issues will only worsen, especially with high cloud and SaaS adoption.
10. Expect biometrics everywhere
Identity authentication is one of the central facts in the new digital economy. Password authentication has been around for decades. More recently, the rise of mobile devices gave way to an improvement: two-factor authentication.
However, both prevalent authentication methods are outdated and offer cybercriminals endless opportunities for abuse and exploitation.
Nonetheless, unlike other technologies that can address a specific segment, authentication has to work for everybody. Hence, the process must be accessible for experienced and naive internet users.
Currently, things like “authentication apps” ensure better identity verification. However, they are still new to the market and have failed to acquire a “killer app” status. These apps can help only if this technology becomes the industry’s standard.
But before that happens, there will be an app war, blurring the immediate necessity for a universal yet foolproof authentication method.
However, the global internet environment seems ready to adopt a single, maybe universal, form of ID authentication to use in every instance. For this, biometric data is the most obvious approach. Hence, it’s among the expected 2026 online privacy trends.
Things like fingerprints, retinal scans, and facial recognition have matured for deployment. Moreover, they are convenient because they don’t require memorizing anything and are challenging to reproduce.
But is biometric authentication safe to adopt? The jury is still out.
For a moment, recall how many corporate data breaches have happened over the years and imagine how something similar can happen. It would include a massive batch of biometric information that can unlock online accounts or access other assets. And, perhaps, no one could reset that breached information ever. So, this security issue still needs attention from the community.
Nonetheless, biometric verification still seems to be a better authentication strategy by far.
11. Data-centric security
In a world where data has become increasingly important, we expect increased data-centric cybersecurity.
Data will increasingly be stored in the cloud, shared across multiple platforms and devices, and accessed remotely. This will lead to a decline in traditional data security approaches. Instead, a data-centric cybersecurity approach will ensure data protection, even if the devices or networks containing it are compromised.
Furthermore, encryption tools will be used to improve data security. With the growing amount of data being collected and stored by organizations and government entities, there will be a greater need to protect this data from unauthorized access and use. This will spark more interest in adopting end-to-end encryption to protect user data.
12. Spiked investments in cybersecurity technologies
Organizations are set to invest more in privacy technologies for protection and compliance with newly imposed privacy laws. In addition, investment in cybersecurity will improve competitive advantage.
Firms that invest in cybersecurity will gain an edge over their rivals by showing potential customers that they take data protection seriously and are doing their best to protect user privacy.
Furthermore, organizations will use it to boost their reputation and image. Having robust cybersecurity technologies demonstrates the firm’s seriousness in protecting sensitive data and respecting individual privacy rights.
13. Increasing regulations to protect privacy
The introduction of the General Data Protection Regulation (GDPR) in Europe heralded the beginning of a new era in online privacy trends. Consumers and data subjects appeared pleased with how GDPR pushed governments to refresh their internet privacy laws.
GDPR has placed Europe at the vanguard of regulations regarding collecting and using personal data.
GDPR is a good start, but it’s only the beginning and remains theoretical in many ways. Online privacy breaches are still there, and the fight keeps going. However, the importance of GDPR in the European legislative systems cannot be overstated.
The closest counterpart to GDPR outside Europe is California’s CCPA from 2020, among all other online privacy laws in the US. GDPR has inspired it in many ways.
CCPA specifies the new obligations that companies doing business in California must face. It has also empowered them to have more control over their personal data.
In the coming year, we will see how these two legislations continue to have their ramifications expand across society.
Many countries and jurisdictions may introduce strict compliance measures to protect personal information. These changes will necessitate organizations and other entities operating in these regions to comply with the new regulations or face significant repercussions.
14. Increase in privacy-related charges and fines
The years 2021 and 2022 witnessed increased GDPR fines imposed on huge companies. With the growing need for privacy regulations, privacy-related fines and charges will likely rise.
Recently, with the large amount of sensitive data collected and sold to third parties, there has been a growing public demand for stricter privacy protection laws. Further, organizations are called upon to be responsible for user data or held accountable if they fail to protect personal information.
In addition, government agencies are investing more resources to conduct investigations and enforce privacy regulations, which makes it even more likely that individuals will be charged with privacy and security violations.
15. More cybersecurity job positions
As mentioned earlier, cyber threats will increase steadily in the coming years. This will increase the demand for cybersecurity experts to help curb the threats.
In addition, most organizations will seek to implement new cybersecurity measures to improve online security and privacy. Consequently, there will be an increase in data security and privacy employment positions in the job market.
16. Extension of data protection policies to Metaverse
Facebook’s rebranding to Meta made the futuristic concept of the “metaverse” popular among the masses. Eventually, the possible adoption of this online realm triggered concerns about users’ online security and privacy, becoming one of the crucial cybersecurity trends for 2026 and beyond.
Like the actual world, the Metaverse will produce a ton of data about its users and their activities, some of which may be personal, such as location, bodily movements, facial expressions, and conversations. So, data protection and security will be significant problems in the Metaverse.
Personal data must be acquired, stored, and handled ethically and legally. This will call for the implementation of fresh data protection policies and procedures designed to incorporate the Metaverse.
17. Increasing focus on Internet of Things (IoT) security
Security issues are emerging due to the growing number of internet-connected devices, such as smart homes and wearable technologies.
These devices gather large volumes of data that can be distributed across multiple devices and networks. This makes data security difficult and raises the possibility of data breaches.
As a result, bad actors will continue devising ways to exploit user data and breach their privacy. Therefore, it’s critical to make sure they are adequately protected.
18. Increase in crypto-jacking incidents
In 2026, cybercriminals will venture more into crypto-jacking. This technique entails unauthorized use of other people’s computer resources, such as processing power and electricity, to mine cryptocurrency without their knowledge.
The popularity of cryptocurrency mining has led to an outburst in crypto-jacking. This has increased the risk of security breaches and data loss, as the process requires malware installation to serve as a backdoor for attackers.
There will also be an increase in energy consumption since crypto-jacking is an energy-intensive process. It will lead to more significant financial losses among individuals and organizations.
19. Broader adoption of passkeys technology
Passkey technology will likely become more widely used. Organizations seek more secure options as users become more aware of the security and privacy threats associated with using standard passwords and the rising incidence of data breaches.
Passkeys will be helpful now that biometric technologies, such as fingerprint and facial recognition, are widely accessible. We will likely see more entities adopt passkey technology in the coming years.
20. Awareness of CISO liabilities
Organizations will become more conscious of the liabilities a Chief Information Security Officer (CISO) may face in the case of a data breach as cyber threats continue to evolve.
Thus, we envision that in 2026, firms will become more aware of providing CISOs with the tools and support needed to manage cyber threats. This entails investing in appropriate security tools and technologies and providing CISOs with adequate access to relevant data.
Also, companies should empower CISOs through training and development to stay updated with the latest trends and best practices.
Other security trends for 2026
Based on market and economic changes, we expect more trends in the online security and privacy niche in 2026.
21. Scarcity in human resources
Human resources will likely become scarce and challenging to retain. Since the COVID-19 outbreak, the employment sector has changed tremendously, with employees now seeking higher-paying roles and flexible working conditions.
Organizations struggle to retain talent as most people are venturing into other fields, with some exploring self-employment opportunities and working from home. The resource constraints will continue in the coming years, with the employment sector seeking to readjust its talent pool.
22. Rise in FinOps
In 2026, we expect to see a rise in FinOps, an emerging trend encompassing technology use and automation to improve the efficiency and security of financial operations. The trend will become more integral to business operations, especially financial data analysis and reporting.
FinOps will be primarily adopted to automate critical processes such as generating accurate and timely financial data. The technology will also provide real-time access to financial databases, enabling firms to make more informed business decisions based on empirical data.
23. Application Security
In the coming years, there will be a growing need for greater collaboration and alignment between security and development teams to address the complexity of modern security threats.
We will see firms integrating security into development by leaning towards DevSecOps. This will ensure that organizations build security from the ground up instead of bolting it after development.
As part of this trend, many organizations are implementing security controls such as static code analysis, dynamic application security testing, and penetration testing earlier in the development process and incorporating them into their CI/CD pipeline.
Another trend in application security is an increased focus on secure coding practices and guidelines to help developers write secure code and avoid common vulnerabilities such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
24. Generative AI governance
Recent developments in generative AI have raised many questions about data privacy. For this reason, generative AI governance will be a hot topic in 2026. AI models like ChatGPT and Google Bard are expected to advance exponentially over the next few years. Similarly, AI usage is expected to increase enormously.
Software developers are among the users hugely affected by generative AI. While the importance of these AI models in code generation cannot be overlooked, developers should use them responsibly to avoid future data breaches.
We should also not underestimate the power of AI in the wrong hands. It could be used for unethical purposes, like scraping biometric information from photos and videos on the web. Chat models like ChatGPT could also expose private information. If you provide personal information to an AI model trained to collect personal data, it could be exposed as output to other users.
So, what should happen if an AI model gains knowledge it shouldn’t? Should the AI model be destroyed since there is no way of deleting just some of its knowledge? Developing a clear framework for this new field might take a while.
25. New laws regulating AI
Many countries are expected to create AI legislation in 2026 to keep up with its evolving landscape. The EU AI Act became law in 2025 after an agreement was reached between the European Council and the European Parliament in December 2023.
The Digital Markets Act and the Digital Services Act are also expected to receive major amendments in 2026 after AI’s integration into digital products and services. Both acts regulate online advertising networks, video-sharing platforms, social networks, cloud services, and search engines, among other tech services and products owned by large corporations.
The US issued an AI Executive Order outlining safe and ethical AI usage guidelines. In addition, a multi-agency team led by the UK’s National Cybersecurity Center and the US Department of Cyber Security released Guidelines for Secure AI System Development.
26. The ‘Pay or Okay’ Approach
The ‘Pay or Okay’ method is a controversial approach to data privacy offered by Meta to its EU users. The approach requires EU users to pay a monthly Facebook subscription to avoid data collection or use Facebook for free in exchange for their data.
However, the approach was met with resistance and is still being evaluated by the European courts. One of the main concerns about the ‘Pay or Okay’ approach is its violation of GDPR provisions that require consent to be offered freely.
The case will continue in 2026, and should the courts uphold the approach, it will be a breakthrough for Meta and other social media platforms like TikTok, which are already experimenting with it. On the other hand, Meta could pay heavy fines if the courts find out the company violated GDPR laws.
If the approach is upheld and adopted by all social media platforms, it will be very expensive to use social media platforms and maintain privacy.
27. Automotive industry privacy restart
The automotive industry is also in the spot for excessive collection, sharing, and selling of consumers’ personal data. According to an article by the Mozilla Foundation, car manufacturers use sensors, microphones, cameras, and direct trackers to collect extensive consumer data.
The study calls for urgent investigation and has caught car owners’ attention. The investigations continued in 2025, and the outcome could greatly impact the automotive industry’s privacy.
The privacy concerns raised by the Mozilla Foundation article clearly indicate that stricter regulations must be implemented in the automobile industry to protect consumers’ privacy.
28. Applying AI to mitigate privacy risk
Privacy risks are expected to grow exponentially in 2026. They will also get more complex because of artificial intelligence. According to a report by IBM in 2025, it takes an average of 227 days to detect and stop a data breach. Within that period, hackers can use breached data to cause harm.
Could AI be the solution for mitigating privacy risks? An AI model integrated with Security systems can analyze large datasets and detect trends, prompts, and patterns across complex data. In addition, AI models can easily adapt to changes in policies and regulations without necessarily restructuring the entire system.
Preparing for the 2026 online privacy and security trends
Key data security and privacy trends expected in 2025 are related to Gartner’s Hype Cycle. The Cycle is a graphical representation of technology’s maturity, adoption, and application stages. It is crucial to organizations as it helps them understand the hype and the technologies’ potential by plotting them on a graph based on their maturity and adoption rate.
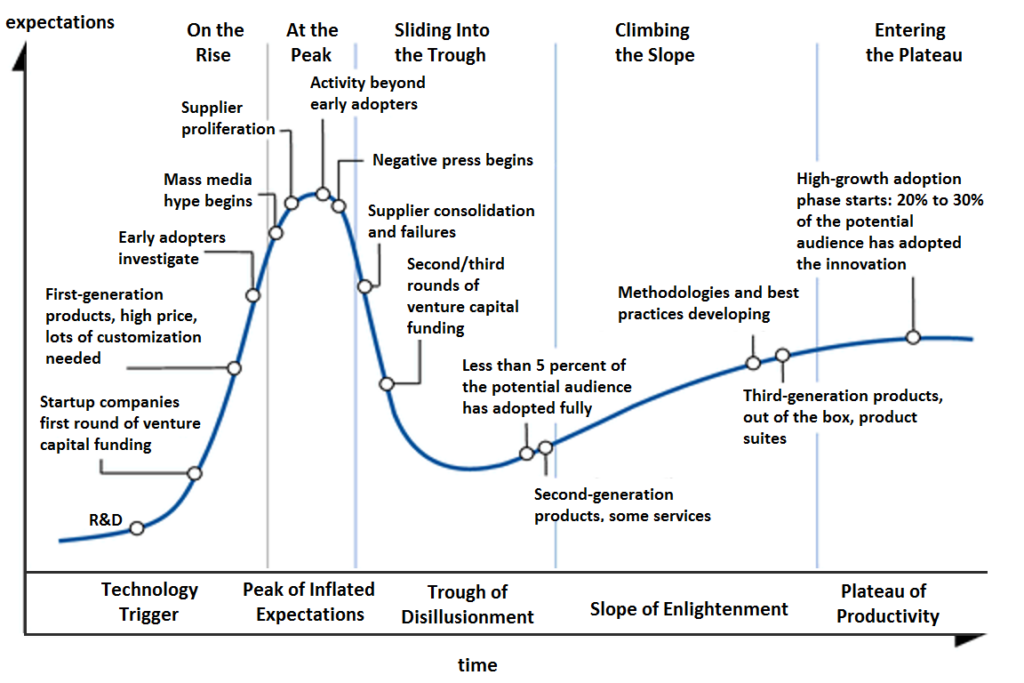
From the Cycle above, we see five phases of technology plotted on a time and expectations scale.
- Technology Trigger: This marks the onset of a new technology characterized by the emergence of new research and proof of concept.
- The peak of Inflated Expectations: This phase shows hype and excitement around new technology. Under this stage, the technology reaches a high point, with most entities jumping on board to capitalize on its potential.
- Trough of Disillusionment: The excitement and hype drop tremendously with limitations and challenges of the technology becoming more imminent. This causes more firms and individuals to abandon or minimize their investment in the new technology.
- The slope of Enlightenment: The phase is characterized by experimentation and learning. Individuals and organizations are beginning to truly understand the actual value of the technology and how they can effectively capitalize on its potential.
- Plateau of Productivity: This is the final maturity stage, where technology becomes broadly adopted with its benefits clearly understood.
Further, technologies such as Data Classification, CASB, Homomorphic Encryption, and Differential Privacy are present in different stages of the Hype Cycle. They are becoming increasingly important for organizations as they help to comply with laws and regulations, establish effective data governance programs, and protect private information.
In a nutshell, the world will see more organizations utilizing the Hype Cycle to assess various technologies better. In particular, the Cycle will be useful in helping firms make more informed decisions regarding which technologies to invest in.
Organizations can now analyze technologies to understand when they will reach the peak of hype and when they may be going through a trough of disillusionment. Hence, they avoid overinvesting in something that may not live up to its potential.
Privacy Laws 2023 Outlook
The United States privacy laws
The United States already has various internet privacy laws and regulations in place. However, California Privacy Rights Act (CPRA) became fully operative in 2024. The Act could strengthen protection measures on sensitive information such as driver’s licenses, bank account information, social security numbers, passports, addresses, phone numbers, etc.
Other government Acts that will also go into effect in 2025 include the Connecticut Data Privacy Act, Virginia Consumer Data Protection Act, Utah Consumer Privacy Act, and Colorado Privacy Act. In addition, other states, including Michigan, New Jersey, Ohio, and Pennsylvania, have pending privacy protection bills that should be implemented shortly.
Regulations already implemented guide business practices, and organizations must abide by them according to state laws. If your business activities fall under the categories discussed below, you might expect several changes in the coming years:
1. Data Brokers
Laws regulating the sale of personal information exist in California, Nevada, and Vermont.
Brokers must register and disclose what data they gather and sell to third parties in California and Vermont. Nevada’s data brokers must allow users to have their information deleted.
2. Internet Service Providers (ISPs)
Regulations have been enacted in Maine, Nevada, and Minnesota to limit ISPs’ consumer data usage.
In Maine and Nevada, ISPs cannot sell or disclose user data without consent. Likewise, ISPs in Minnesota must obtain customer permission before disclosing or selling their browsing history.
3. Data privacy for minors
California and Delaware have passed rules that limit certain types of advertising to minors (below 18 years) to safeguard their internet privacy.
The California Consumer Privacy Act (CCPA) has provisions that forbid using information obtained from minors to target them with advertisements or other forms of internet marketing. Additionally, it prohibits the promotion of goods like cigarettes and alcohol that are illegal for children to purchase. The right to be forgotten allows minors to ask that their information be deleted from websites, apps, or other web-based services.
Similar legislation exists in Delaware as well, which, like California, limits internet advertising to children. The Delaware Online Privacy and Protection Act holds advertisers accountable if they are aware of the legislation yet engage in illegal behavior. This implies that violating advertisers risks legal charges.
4. E-Reader Privacy
Several states, including Arizona, California, and Missouri, have implemented laws forbidding the disclosure of details on a library user’s activity.
For example, releasing data about a subscriber’s use of a digital book service is prohibited in California and Delaware. In addition, information can only be disclosed if there’s a warrant or a threat to life.
5. Data sharing
California and Utah require online non-financial enterprises to inform clients of the data they share or sell.
6. Electronic monitoring of employees
Connecticut, Colorado, New York, Delaware, Tennessee, and Hawaii inform employees that their web activities, emails, and location are monitored. While phrased differently, all the aforementioned states are required to notify employees about tracking incidents.
7. Comprehensive privacy laws
The states of Utah, Connecticut, Virginia, California, and Colorado are expected to undergo comprehensive privacy laws in 2025. Therefore, firms should review and amend their privacy policies, employee training, data processing agreements, data security standards, and marketing, advertising, and cookies policies to ensure compliance.
Employee training will help individuals know their rights and the laws that apply to their workplace and state of residence. Furthermore, organizations must post their privacy policies, including the type of data collected, shared, or sold to third parties. Incorrect information will attract legal charges.
Europe Privacy Laws
The General Data Protection Regulation (GDPR), passed on May 25, 2018, is the main privacy regulation in Europe. However, new laws and regulations have emerged, mainly the Digital Markets and Digital Services Act.
The following is a list of proposals you should keep abreast of in 2023:
The General Data Protection Regulation (GDPR)
The GDPR is a specific privacy regulation that applies to all European Union (EU) businesses that handle people’s personal data. The GDPR aims to standardize data protection regulations throughout the EU and give EU citizens more control over their personal information.
Organizations that fail to comply with these privacy regulations are subject to administrative fines of up to €20 million or 4% of their annual global turnover. Some key points in the GDPR include:
1. Consent
Companies must be able to show that a person has provided their informed consent and, if questioned, must be able to produce proof that this consent is unambiguous and freely given. In addition, the controller shall cease processing the data if a person withdraws their permission.
2. Data breach notification
The controller should notify the relevant supervisory authority of data breaches and, in some instances, affected persons within 72 hours of becoming aware of the breach.
3. Data subjects’ rights
Under GDPR, data subjects have several rights concerning their sensitive information:
- The right to be informed: Data subjects have a right to information about how their personal data is collected, used, and stored, including why their data is processed, the categories of personal data being collected, and how long the data will be retained.
- The right to access their data: Data subjects have a right to access personal information about them and retain a copy of their data.
- Right of rectification: Data subjects have a right to request that their inaccurate or incomplete personal information be rectified.
- Right of erasure: In some situations, such as when the data is no longer required for the reason it was obtained or when the data subject withdraws their consent, data subjects can request the erasure of their sensitive data.
- The right to restrict processing: Data subjects can restrict how their personal information is used.
- The right to data portability entails transferring personal data in a machine-readable format and transmitting such data to another controller.
- The right to object: Encompasses the right to object to specific data processing at any time, including processing based on legitimate interests or direct marketing.
Digital Services Act (DSA)
The EU is considering passing the Digital Services Act (DSA), which would regulate the obligations and liabilities of online platforms. The legislation will handle the challenges that the evolving digital environment presents.
The DSA’s primary goal is to establish guidelines for companies offering digital services that strike a balance between user rights and freedoms and the need to safeguard the public from manipulative, false, or unlawful content.
The Act applies to the following business categories:
- Internet Service Providers.
- Hosting service providers, e.g., cloud services.
- Online commercial and networking platforms.
- Huge online platforms that reach out to more than 10% of European consumers.
Each of the business categories above has different requirements:
All business categories must:
- Practice transparency by disclosing court orders and measures.
- Terms of Service should be updated to reflect fundamental rights.
- Cooperate with the government authorities.
- Identify sources of contact for the authorities and, if necessary, legal counsel.
Hosting services, online commercial and networking platforms, and huge online platforms must:
- Report criminal offenses.
- Offer a notice-and-action feature that enables consumers to flag potentially illegal content for removal by the company.
Online platforms and huge online platforms must:
- Implement measures to ensure the transparency and traceability of online advertising.
- Develop user-facing transparency for online advertising.
- Avoid advertising to minors.
- Formulate a complaint and redress mechanism for users.
- Implement effective measures to address illegal content.
- Take keen interest and action on marketplaces.
- Identify trusted flaggers crucial to content notices.
Large online platforms must:
- Cooperate with supervisory and public security authorities to detect and prevent illegal activities and promote the protection of individual rights.
- Share data with researchers and authorities.
- Adhere to their codes of conduct.
- Provides users the right to object.
- Appoint an internal body responsible for compliance with legal obligations and self-regulatory commitments.
- Implement risk management practices and response strategies.
Digital Markets Act (DMA)
The Digital Markets Act (DMA) aims to regulate the behavior of gatekeepers in digital markets.
The Digital Services Act (DSA) and the DMA are being developed by the European Commission to address the changing digital landscape and the new challenges it poses.
The DMA aims to create a framework of rules for digital gatekeepers, defined as companies with significant market power in a specific market, and to prevent them from engaging in anti-competitive practices.
Who is a “gatekeeper” in a market?
A company should meet the following to be considered a gatekeeper:
- Has an entrenched or durable position in a particular market: The company must have a chronic position in a specific market, which makes it difficult for others to compete or enter that market.
- Has a strong economic position, certain revenue thresholds, and a significant impact on the internal market: The company would need to have a substantial effect on the EU market, be an active member state, and possess the potential to create barriers to entry for new players.
- Provide a core platform service: The company would need to provide an essential service of the digital economy used by many businesses or consumers.
DMA’s policies for gatekeepers
The proposed draft of the DMA includes several requirements for businesses that qualify as gatekeepers, including but not limited to the following.
- Prohibition on self-preferencing. Gatekeepers are prohibited from favoring their products or services over their competitors.
- A duty to provide fair, reasonable, and non-discriminatory access to the infrastructure, services, and data they control. That means they must not discriminate against rivals wanting to use their services or access their data.
- Compliance with transparency and data access requirements. Gatekeepers must share data in some instances and provide access to certain functionalities established by authorities.
- Interoperability: Gatekeepers must ensure that their services can interoperate with third parties.
- Compliance with ex-post behavioral remedies and ex-ante structural remedies. Authorities have absolute power to impose measures that correct any anti-competitive behavior.
- Compliance with the principle of fairness of terms of business.
- Respect of core guarantees: Gatekeepers must guarantee transparency and non-discrimination in their commercial policies and practices.
- Fairness and predictability in contractual relationships: Gatekeepers must apply fair and objective criteria to contracts with third-party firms and provide transparent terms of use (ToS) for their services.
- Ease of use: Gatekeepers must make it easy for users to change a service’s default feature or uninstall the program.
Gatekeepers risk fines of up to 10% of their annual global turnover if they violate the DMA. Additionally, in the event of repeated violations, the fines may be increased up to 20% or forced divestitures.
The penalties will depend on the specific circumstances of each case and are imposed by the European Commission (EC) after a thorough investigation and decision process in which the gatekeepers will have the opportunity to respond and defend themselves.
Key EU Proposals in 2023
1. The EU-US Data Privacy Framework
Initially, the EU relied on Privacy Shield Framework to share data across the US. However, the Framework was rendered ineffective in protecting data, calling for a more comprehensive framework to strengthen the relationship between the two jurisdictions. Consequently, President Biden approved an Executive Order to implement the EU-US data privacy framework.
The Executive Order includes several key elements, such as:
- Added safeguards and transparency obligations conducted in compliance with national security directives regardless of a person’s country of residence.
- To ensure compliance, the US Intelligence Community must update policies and procedures to accommodate new standards that protect a person’s privacy and civil liberties.
- A redress mechanism to address any privacy violation. This mechanism allows parties from regions to request independent review and redress. The responsible party must comply with the outcome.
- Legal, oversight, and compliance authorities will extend their duties to ensure compliance and remediate any violations of the Framework.
Framework implications
The EU-US Data Privacy Framework has significant implications for businesses, organizations, and individuals.
The Framework establishes obligations for businesses and organizations to transfer personal data between the two jurisdictions legally. These include implementing data protection policies, appointing a Data Protection Officer, and responding to data access requests. Organizations not complying with the Framework may be subject to fines and penalties.
The EU-US Framework provides additional protections for personal data. It calls upon intelligence activities to comply with defined national security directives and to consider personal privacy rights, regardless of the nationality of residence. It also includes a redress mechanism, allowing individuals to request an independent review of privacy violations and a binding outcome.
Inconsistencies across states will complicate compliance. For instance, entities must register in not more than one state. Addresses, contact information, and websites may suffice for registration. However, some may ask you to specify the data being collected.
Further, the need for cybersecurity best practices to be implemented increases the compliance burden.
Cybersecurity implications
Staying abreast of cybersecurity best practices can be overwhelming and may require additional resources and expertise.
The business must perform critical practices such as regular security audits, incident management, incident response plans, employee training, security firewalls, intrusion detection systems, data encryption, and data security. These practices can take away key resources needed to compete in the market.
However, the alternative is to face huge penalties and legal fines, which could harm the business. Working with an expert could help comply with new legislation and still stay competitive in the market.
2. EU ePrivacy Regulation
The EU ePrivacy regulation is long overdue. In 2022, the EU Council drafted the policy, but it is expected to come into effect in 2023.
The law would introduce new rules for processing user data, including provisions on the confidentiality of electronic communications, the use of cookies and similar technologies, and the processing of sensitive information concerning the provision and use of electronic communications services.
The ePrivacy regulation applies to the use of cookies, tracking services, and similar technologies, as well as the processing of personal information in the context of electronic communications services such as emails, text messages, instant messaging, and internet-based phone calls. It lays down rules on how such services can be provided and used, especially regarding protecting users’ privacy and personal data.
3. Artificial Intelligence Act (AI Act)
The Artificial Intelligence Act (AI Act) aims to regulate the use of artificial intelligence in the EU.
The proposed legislation seeks to promote the development and use of AI in a safe and trustworthy manner while simultaneously protecting fundamental rights and values, such as privacy and non-discrimination.
Based on the Act, businesses that venture into the technology must:
- Conduct risk assessments, comply with transparency obligations, and keep records.
- Avoid AI systems that could manipulate individual behavior, causing mental and physical harm.
- Deter from AI systems that exploit minority groups.
- Not develop AI systems that provide sensitive data such as biometric information.
- Stop developing systems that exploit individuals or groups based on their age, disabilities, or behaviors.
Other international data privacy laws

Covering all data privacy laws under a single article can be challenging. However, on top of the laws mentioned above, there are a few other important regulations to note:
- The Brazil General Data Protection Law (LGPD): This law applies to organizations operating in Brazil and governs the collection, use, and storage of personal data.
- The Personal Information Protection and Electronic Documents Act (PIPEDA): The law guides organizations in collecting and using personal information during commercial activities.
- Japan’s Act on the Protection of Personal Information (APPI): The law governs the collection, use, and storage of personal information. It applies to local and foreign companies operating in Japan or handling Japanese citizens’ data.
- The Australian Privacy Act: This law applies to organizations operating in Australia and governs how they collect, use, and disclose personal information.
- The Health Insurance Portability and Accountability Act (HIPAA): This US federal law applies to organizations that handle protected health information (PHI) and sets standards for protecting the privacy and security of PHI.
- China’s Personal Information Protection Law (PIPL): The law came into effect on November 1, 2021, and governs personal information protection and data security for organizations, both private and state-owned, and individuals as a response to the increasing need of Chinese citizens to protect their personal information and rights.
Tips for complying with data privacy laws in 2026
Complying with data privacy laws in 2026 will be challenging. So, here are a few tips organizations can use to ensure compliance.
1. Understand different Privacy Rights Acts
Different data privacy laws apply to different types of organizations and their area of operation. So, it’s essential to understand the actions that apply to your business and how you are enforcing them. It will provide a solid background for complying with various stipulations and avoiding legal charges.
2. Conduct a data audit
Today, data is highly sought after in the business world. Organizations rely on user data to understand consumer behavior and tailor ads and marketing content. Therefore, to ensure compliance with privacy laws, it’s essential to know what personal data your organization collects and stores and how it’s used.
A data audit can help identify need gaps and provide a starting point for creating a data protection strategy needed for compliance.
3. Review and update the data privacy policy
With increasing changes in privacy laws and regulations, organizations must regularly review and update their data protection measures. In addition, data privacy laws and regulations can change over time. As such, reviewing and updating your data policy is recommended to comply with measures by various regulations such as DDPR or the CCPA.
Further, you should review your cookies and ad tech strategy to ensure their compliance with data privacy laws and regulations. You should also implement mechanisms to obtain informed consent and ensure transparency.
4. Review contacts and agreements with third parties
A crucial tip in ensuring compliance with privacy laws is to review contracts between the organization and third-party service providers.
Compliance with relevant regulations is only as good as the level of compliance exhibited by your business partners. Ensuring third-party partners abide by relevant data privacy laws can be beneficial in mapping out your data flow from collection to disposal.
Therefore, you should review agreements with vendors and other parties to understand their data privacy policies. That will ensure you conduct business with vendors who comply with industry standards and regulations.
5. Stay abreast of your businesses and systems
Compliance with data privacy laws and regulations requires a thorough understanding of your organization’s data processes and being able to implement best practices for data protection.
You should update your business systems to ensure you follow the required regulations. Also, you should identify areas that may pose a risk to personal data privacy and where they can change the existing processes.
Computer systems and databases should also be regularly updated since obsolete systems could be gateways for data breaches. Regular reviews and updates of these systems will improve your security as new updates come with bug fixes, updated privacy policies, and improved security measures.
6. Staff training and development
Employee training and development is an excellent step to ensuring your organization complies with existing privacy regulations.
Data privacy laws require you to implement various measures to protect personal data. However, these measures can only be effective if employees are properly trained to comply.
Training should be regular and tailored to the specific duties of different employees within the organization. For example, employees handling sensitive data in the marketing department will require more in-depth training in consumer data than those handling less sensitive data.
7. Be flexible
With the world becoming more dynamic and not forgetting the continuous updates on privacy laws to accommodate these changes, it’s only right if you remain flexible and anticipate further changes. This will help you stay prepared and ready to adopt new policies and procedures as they occur.
Monitoring existing regulations will help anticipate areas likely to undergo amendments. For instance, the growing trend in AI definitely hints at the future changes in regulations governing the creation and use of AI.
Personal data covered under modern privacy regulations
Gartner estimates that by 2023, about 65% of the global population will have its data covered under privacy laws and regulations. This will be a tremendous increase from the 10% recorded in 2020.
With more imminent privacy laws, GDPR has attained its threshold, becoming the benchmark for global privacy standards.
Current privacy regulations, including GDPR and CCPA, cover a wide array of personal data, including:
- Personally identifiable information: This includes name, address, location, phone number, and government-issued identification documents,
- Biometric data: This entails facial recognition data, fingerprints, and voiceprints.
- Health data: This includes medical records and health insurance information.
- Financial data: Includes bank account details and credit/debit card details.
- Online data: This includes internet usage data such as cookies, browsing history, IP address, etc.
Reasons why data privacy compliance must take center stage in 2026
1. Expansion in data privacy laws
GDPR has set the bar so high that other nations are adopting new privacy laws to meet the standards. In the United States, states such as Utah, Connecticut, Colorado, and California are keen to enforce modern privacy laws.
Therefore, with increased expansion, organizations will likely take compliance seriously in 2026 to avoid lagging behind in the online security and privacy war.
2. Complex cross-border privacy laws
Data privacy regulations vary from one country to another. For instance, an action considered to violate privacy law in one country might be acceptable in another. The difference in these laws makes it challenging for organizations to comply with all regulations across borders.
While meeting the laws in one nation is possible, adjusting an organization’s policy to accommodate those of other nations is a key issue. These variances call for more attention to data privacy compliance debates in 2026.
3. A shift to cloud services left most organizations vulnerable
Following the COVID-19 pandemic, the economy saw most organizations shifting towards virtual working spaces. The use of new cloud services for data sharing and video-based conferences became common.
At that time, companies were more concerned about adopting cloud technologies speedily to stay in business to the extent that they forgot about privacy. Consequently, most organizations became exposed to security and privacy vulnerabilities, rendering themselves non-compliant.
Today, most of these firms are playing catch-up to ensure that cloud technologies align with the existing privacy laws.
4. Data privacy fines
Many privacy regulations, like the GDPR, have substantial fines for non-compliance, such as the 4% of the overall global turnover.
In the past, numerous multinational corporations received hefty fines for non-compliance. For instance, Amazon was fined $887 million for lack of compliance on its EU properties. Similarly, WhatsApp was also fined $266 million because of poor data collection and use transparency.
With privacy fines becoming more prevalent, organizations will increase compliance with existing laws to avoid facing legal charges and fines.
5. Changes in how organizations collect, use, and share user data
Organizations will likely change how they gather, process, and share user data in response to increased data privacy regulations and growing consumer awareness of data privacy risks.
Firms will be more stringent in adhering to data protection laws. These include data localization, cross-border data flow compliance, and other laws that may vary by jurisdiction.
In this light, firms will be more inclined to adopt privacy measures aligned with industry standards.
6. Growing consumer awareness of data privacy
As more people become aware of the risks associated with data breaches and the misuse of personal information, they will likely demand greater transparency and control over data collection and use. Such public outcry to gain control over personal information will necessitate data privacy compliance.
7. The rise of new technologies
As new technologies such as IoT, AI, and 5G become more prevalent, they will create new opportunities for data collection and analysis and potential risks to data privacy. Therefore, organizations must comply with privacy regulations as they adopt these new technologies.
Cybersecurity threats to prepare for in 2026
1. IoT attacks
As more devices connect to the internet, cybercriminals may target vulnerabilities in IoT devices to gain access to networks and steal sensitive information. This can include attacks on smart home systems, wearable devices, and other devices.
As the number of connected devices grows in the coming years, IoT attacks will likely become more sophisticated and frequent. Additionally, as the IoT ecosystem becomes more complex, attackers will have more opportunities to exploit vulnerabilities in IoT devices and networks.
To protect yourself from these attacks, ensure you perform regular updates on your devices, use a secure network, and create strong passwords for your profiles.
2. Mobile attacks
The smartphone industry is growing exponentially. Unfortunately, most users lack the know-how to protect their information on mobile phones. This has resulted in more cases of phishing and stolen passwords. As more and more people continue using smartphones, attackers will inevitably advance their interest in stealing private data.
Updating devices with the latest security updates and downloading programs from trusted app stores like the Google Play Store or the Apple App Store can help you prevent mobile attacks. Likewise, you should avoid clicking unknown links, sending suspicious texts and emails, and entering personal information on untrusted websites.
Additionally, use multi-factor authentication and anti-virus software while logging into internet accounts.
3. Critical infrastructure attacks
Cybercriminals are always excited by the magnitude of their attack. Their joy would be to see the entire tech giant’s network system down. However, in 2026, attackers will likely target entities associated with critical infrastructure–an attack would leave a mark on the cybersecurity incidents ever reported worldwide.
With cybercriminals advancing their techniques, we cannot dispute the likelihood of witnessing such a devastating incident in the coming years. Therefore, organizations and authorities must be careful and thorough with their security frameworks to prevent the world from witnessing such events.
The biggest challenge facing the cybersecurity industry
The transition to remote and hybrid work has significantly impacted the cybersecurity sector. The epidemic hastened this tendency, and more people are expected to work remotely and in hybrid environments in the future.
However, due to the scattered workforce and greater use of digital tools and technology, defending against cyberattacks that expand the attack surface for cybercriminals has become more challenging.
A key concern facing the cybersecurity sector is ensuring that remote and hybrid employees get access to the data needed to perform their duties fully while limiting their access to sensitive data and systems beyond their clearance.
Controlling access to vital infrastructure and information systems was simpler in a traditional workplace. But, with a distributed workforce, security policies must be established around remote access and digital identity management.
Due to the relatively flexible security standards for remote and hybrid employees than the traditional office setting, there is an increased risk of data breaches and cyberattacks.
Therefore, businesses must take the initiative to develop robust security standards from the ground up and guarantee that all employees, regardless of location, have the same level of protection. That includes guarding access to digital assets, including cloud-based services and connected digital supply chains, and ensuring proper training for all staff members on optimum security procedures.
Data privacy challenges
Data privacy is a complex and multifaceted issue that poses several challenges for organizations. Privacy regulations are becoming more stringent today, making it challenging for companies to use traditional data collection techniques.
Organizations must achieve a balance in the collection and use of data. While data is vital to operating a business, there is a need to protect personal data and adhere to privacy regulations.
Organizations must be transparent about their data collection and sharing practices and obtain consent from individuals to collect and use their data. Navigating privacy laws is often difficult. However, organizations must understand the requirements of these regulations and develop strategies to comply with them despite their complexities.
Firms must identify and protect sensitive information such as personally identifiable (PII), financial, and health-related data. This requires organizations to implement robust security measures, such as encryption, access controls, and monitoring, to prevent unauthorized access or breaches.
Moreover, to improve security, firms must also ensure that their business partners comply with existing privacy laws, which can sometimes be overwhelming, considering different regions have differing regulations.
