With online surveillance and data tracking keep increasing, protecting your identity and data online is no longer optional; it’s essential. One commendable method that helps with the cause is onion routing. It is a technique that hides your internet traffic by passing it through multiple layers of encryption and routing the traffic through several volunteer-operated nodes (dubbed Tor nodes).
Onion routing is the foundational technique behind the infamous Tor network, which mostly journalists, activists, and everyday users (who value their privacy) use to gain maximum anonymity. Whether it’s hackers, ISPs, or even governments at your tail, onion routing makes it difficult for anyone to trace your activity back to you.
Understanding onion routing is crucial for anyone serious about digital privacy, as it effectively conceals your location and identity. This guide explains how it works, its practical applications in daily life, risks, and more.
What is onion routing?
Onion routing the technique that Tor Network uses for allowing users to hide their online traffic by routing it to several encrypted nodes. It enables private, secure, and anonymous communication over a network by encrypting messages in multiple secure layers (similar to the layers of an onion and hence the name).
Once you start using onion routing, every bit of the data you send to any destination becomes a code no one can understand. The code, then, travels across random volunteer-run servers in different parts of the world. These servers can only tell where the code came from and its next destination.
Then, the code is hauled around through onion relays and servers. As such, the content, its source, and destination are left for guesswork among the servers or anyone who tries to compromise the code. (Only the client, your device, and server, Tor’s intermediate relay nodes, can see where the coded data is coming from or what was sent).
While the package is passed through each hop, the intermediary node peels off one layer of encryption and only displays the next hop in the chain (just like peeling an onion).
Thanks to this concept, we have the onion domain “.onion”, and yes, you can’t easily find such on the clearnet. You may be wondering, what is an onion domain? Read along to find out about this.
Onion domain
An .onion domain is basically the hidden address of websites that are located in the “underground” internet. Unlike the regular websites’ URLs, onion website addresses are nonsensical—something like 3g2upl4pqufc4m.onion (always ending with .onion).
You can’t access these addresses using normal browsers like Chrome, Firefox, or Safari; you need a special browser like Tor to access them. Standard browsers don’t (can’t) follow the series of proxy servers that will take the user to this type of website.
In short, onion domains (.onion) are the URLs of services and websites that are hosted on the Tor network. And, they use the onion routing method to provide more privacy to both users and the servers that host .onion websites.
Consider .onion sites as the speakeasy bars of the internet; you must have two keys, the Tor browser and the password (the .onion address) to gain secret entry.
How does onion routing work? The science behind it
Now that you know what onion routing is, it’s time to discuss how it works.
The onion routing protocol turns your data into code multiple times. Then it sends it on a mystery tour through random nodes or “onion routers.”
Here’s how:
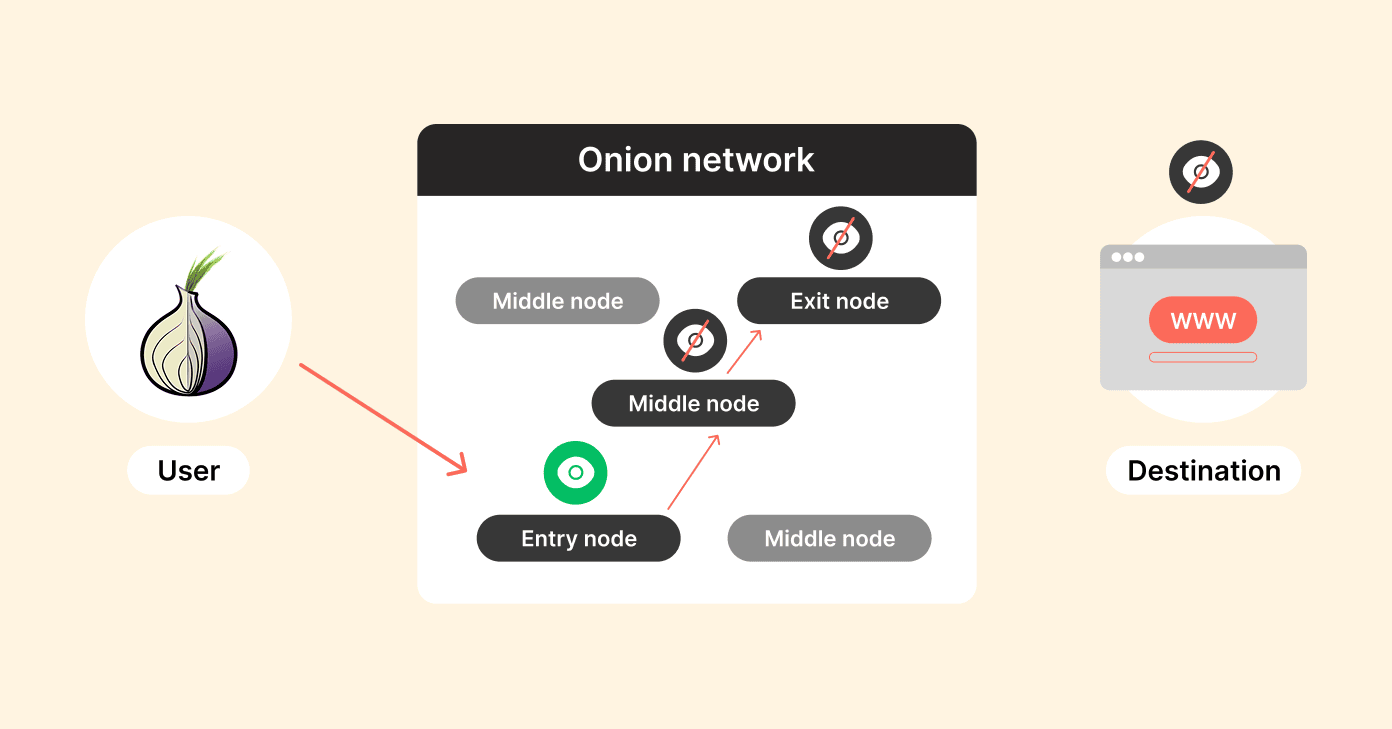
- Encryption layers: To begin, your data gets broken into codes multiple times and layers. Each layer has a random node tied to it in the network. Imagine putting your letter in envelopes upon envelopes with different addresses to different post offices.
- Randomized path: Your encrypted data takes a randomized path through at least three nodes. For example, an entry node (guard), a middle node (relay), and an exit node. Each time, the path changes, and you cannot predict where you’re going.
- Layer decryption: Each node can only decrypt the layer they are responsible for to determine the next node, and can see only the outside of “envelope” to know where to send the encrypted data. However, it cannot open the inside envelope or see the contents and destination.
- Exit node: The exit node decrypts the last layer of encryption and delivers your information to its ultimate destination on the standard internet.
How this works is quite beautiful: every node only knows the identities of its immediate neighbors in the chain; it never knows the whole route.
Therefore, if someone compromises one node, they cannot re-identify your traffic or discover where your traffic is going.
Onion routing use cases – Real-world scenarios
Onion routing makes network surveillance less challenging, so people can send messages, emails, and even browse without identity leaks. It’s a go-to solution for entities like activists, journalists, and whistleblowers bypassing government surveillance.
Let’s check a few examples:
| Application | Examples | Description |
|---|---|---|
| Anonymous communication platforms | Tor Messenger, Ricochet (an open-source anonymous instant messaging app) | These platforms utilize onion routing to make it possible to have secure and hidden conversations while at the same time preventing the participants involved from being identified by an outside observer. |
| Secure browsing tools | Tor Browser, DuckDuckGo Web Browser | These browsers run on the concepts of onion routing. They allow users to browse the net without IP leaks or browsing traces. |
| Circumventing censorship | Accessing blocked news sites, social media platforms | In countries where the internet is highly censored and monitored, onion routing provides a means for individuals to circumvent government-blocked content to enjoy a borderless internet. |
| Resistance to surveillance and analysis | SecureDrop, GlobalLeaks | Platforms like SecureDrop and GlobalLeaks use onion routing to safeguard whistleblowers and journalists so that sources can share sensitive information without the concern of retaliation. |
There is a misconception that only the dark web users use onion routing, while the truth is that everyday users who value their privacy use onion routing. Plus, with the given features, it’s common amongst investigative journalists in authoritarian countries.
Top onion routine features
1. Layered encryption
In onion routing, your data gets wrapped in multiple layers of encryption at the first node, known as the entry node or guard node.
After that, the data traverses multiple middle nodes to reach the exit node. Each of these middle nodes decrypts one layer of encryption, revealing only the destination of the next node in the circuit.
Each trip through a node removes a layer of encryption to reveal the destination of the next node in the circuit.
Only the exit node knows where the message is actually going. The layers of encryption conceal your IP address and data about your computer from both the web pages you visit and your internet service provider.
Each layer of the “onion” is encrypted with the public key of a specific node (entry, middle, exit). Since each node only has its own private key, it can only decrypt the layer intended for it. This ensures that no single node can see the entire path at once.
2. Volunteer-operated nodes
The onion routing protocol operates on a decentralized network based on thousands of servers (dubbed “relays” or “nodes”).
Mostly, individuals who do not require any oversight from an authority run these nodes. This limits the chances of surveillance, as there is no one authoritative party.
It’s just thousands of individuals around the world who are voluntarily running your privacy network as a hobby. They have no financial gain of running those nodes.
3. Enhanced shield against traffic assessment
The layers of encryption that onion routing provides make it difficult for bad actors to examine traffic patterns. So, it gets hard to run any traffic analysis. Snoopers can’t figure out the origin and final stop of messages passing through the network.
Even big tech firms may get a glimpse of the network, but finding out the whole path of communication won’t be possible.
It would be similar to trying to study someone’s movements through a crowd, and everybody is changing clothes and moving in all directions at random.
4. Access to the deep web
The deep and dark web are the hidden parts of the internet that you can’t access through typical browsers. You need a special browser, like the Tor browser (that again uses onion routing), to access the dark web safely. As Tor network is responsible for backing onion routing, it lets users access this darker side of the web securely.
Beware, it’s not ideal for your everyday browsing because of its black market elements. We recommend average internet users to be cautious and stay away from deep web.
5. Dodge censorship
The onion routing system allows users to bypass censorship and communicate freely on the internet. Now, this is common in jurisdictions of extreme restriction where government agencies surveil and block internet access.
It’s like having a secret tunnel under the Great Firewall; governments can and will try to block it, but the distributed nature of the onion routing protocol makes it almost impossible to shut it down.
6. No direct connection
This feature makes onion routing such a strong tool: data traveling between you and your destination doesn’t directly travel between those points.
Instead, it gets routed through a series of intermediary nodes where prying eyes (both from you and the public endpoint) do not have access to the contents.
7. Danger-free public Wi-Fi
Onion routing helps secure your online communications over public Wi-Fi networks, which are unsecured by default and have known security vulnerabilities.
That shady coffee shop Wi-Fi doesn’t look so bad anymore when your communications are wrapped in multiple layers of encryption.
Is it legal to use an onion router?

The use of onion routing services such as the Tor network is legal in most countries (explained in our dedicated guide here).
The onion routing protocol is mainly meant to:
- Address the privacy of the user while using the internet.
- Securing the communication over the internet.
Moreover, many people use the protocol for completely legitimate reasons – to protect personal privacy and bypassing censorship.
Journalists, activists, and researchers use it a lot to get their hands on secret news without revealing their real identity. Nevertheless, in some countries, government authorities regulate or monitor the spectating of onion routing due to the concerns associated with anonymous browsing.
They want to prevent access to the dark web and stop any act to circumvent government censorship. In some countries (such as Turkey, China, Russia, to name a few), governments may prohibit or block access to onion routing networks because of their anonymity. But the truth is, onion routing is just a technology, like a car or a kitchen knife. It’s neither good nor bad. It’s just technology. And it’s only what you make of it.
What are potential risks and downsides of onion routing
Onion routing may pose a holy grail tech, but it’s important to know its downsides too.
Could these attract risks in the future? Let’s find out.
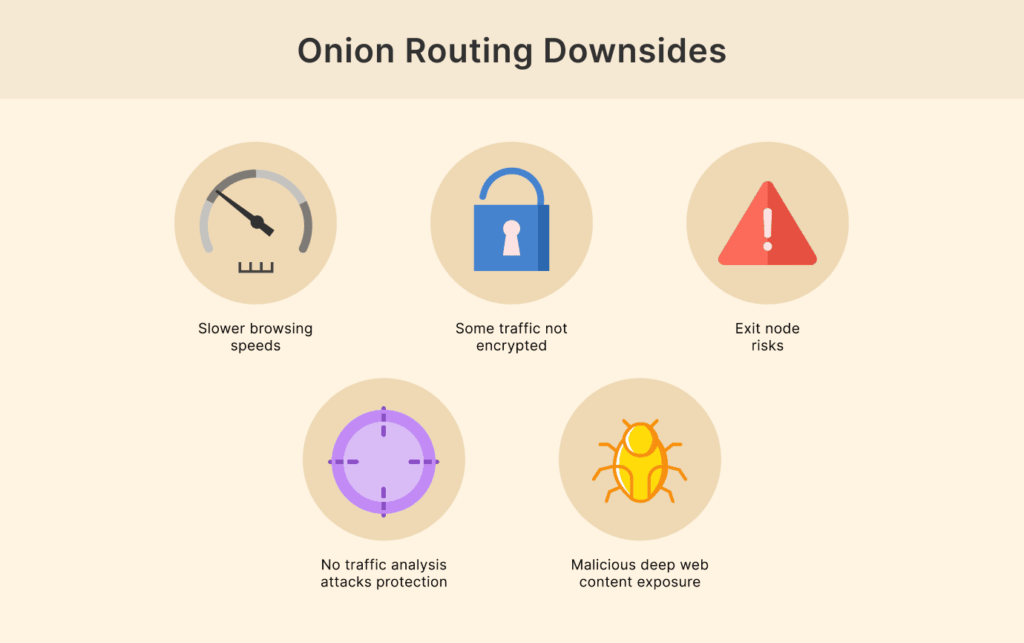
Slower browsing speeds
Let’s be honest—onion routing isn’t winning any speed contests.
All that hopping from node to node across the globe can seriously impact network performance and slow down your browsing speeds due to increased latency.
What takes seconds on a regular connection might take much longer through the onion routing network. There’s something you need to compromise on if you want privacy.
Some traffic is not encrypted end-to-end
Onion routing only protects your messages before they leave the network. The communication between the exit node and the destination is not encrypted by the onion routing protocol.
As such, it can be compromised and/or modified by traffic analysis, especially when you visit a non-encrypted HTTP website and not an HTTPS one.
Exit node risks
Individuals operate most relay servers on the onion routing network. However, there are “planned exit nodes” that attackers could place to facilitate their malicious activities. The exit node (where your data exits the Tor network into the regular internet) could be under the watch of the bad guys waiting to strike at any slight loophole.
There also have been reports of Tor exit nodes injecting malware in the past.
Not enough protection against aggressive traffic analysis attacks
Although what is in your messages never gets seen, attackers with deep pockets and resources can still monitor incoming and outgoing packets.
They might be able to deduce patterns and relationships between users and their activities through advanced correlation attacks.
Exposure to malicious content in the “deep web”
What you see in the deep web through onion routing is just a piece of cake. The real deal is on the dark web. The dark web is filled with illicit and illegal activities, including drug selling, pornography, and more. However, it’s not only the bad things about the dark web; you can also get useful information and browse anonymously on this darker part of the web.
If you must visit this dark corner, practice serious caution (use the Tor browser with a VPN). To be on the safest side, use onion routing for regular web browsing and forget about those darker corners.
Dependency on volunteer-run infrastructure
The nodes cannot all be equally well maintained or trustworthy. When there is high traffic, the increase in connections can deplete the network’s speed and tamper with its reliability.
If they are not configured properly, nodes can pose security risks instead of protection.
Tor vs I2P (onion and garlic routing) – The differences
The Invisible Internet Project (I2P) is unique in its approach to privacy, opting to use “garlic routing” as compared to onion routing.
Similar to Tor onion routing, I2P garlic routing applies encryption to bundle multiple messages in a single encrypted message referred to as a “garlic clove.”
To put it differently, onion routing delivers one letter at a time via different post offices, whereas garlic routing sends a group of mail at once in one single package. The garlic packets are bundled together, encrypted again, and routed through the I2P network.
I2P is different in that it operates as a completely distinct ecosystem on top of the main internet, a completely encrypted overlay network. An I2P website will end with the I2P extension, and a Tor onion routed domain with .onion.
Tor onion routing is used more often for general browsing on any public network, whereas I2P provides a greater level of privacy for communications within its own system.
Onion routing vs a VPN – What makes both different?
A common question people have is: What’s the difference between onion routing and a VPN? Since they both use encryption to protect your online traffic, what makes them stand out individually? Both onion routing and VPNs help hide your IP address from your ISP, foster anonymity, yet they differ.
Here’s how:
The encryption process
Onion routing encrypts your data in layers or ‘onions’, then routes it through numerous volunteer nodes around the world.
A VPN only encrypts and then sends your traffic through a secure tunnel from your device to a single, remote VPN server.
Privacy and accountability
The onion routing network is made up of nodes run by volunteers, and no one knows how many layers of encryption have already been applied to your online traffic.
So, there is no single oversight for the routing process. It’s a strong decentralization, yet it has a potential weakness because there is no single point of control. That’s a two-way sword. Someone could have a node running on the network just to collect information or traffic.
In contrast, most reliable VPN services have well-defined privacy policies (dubbed no-log policies) and do not store users’ connection logs.
Connection speed
This is another point where VPN is better than onion routing. Routing your data over several nodes on the onion routing network can dramatically affect your internet speed with substantial latency.
Using a reputable VPN doesn’t affect your speed much because you have fast, dedicated servers at hand and less encryption layers come into play.
Usability
For maximum anonymity on onion routing, you must be “extra cautious” in whatever you do on the network. Don’t give out identifiable details; use safer communication frameworks.
Meanwhile, with a VPN, you can go about your daily activities without many protection concerns as long as your connections are reliable. Plus, it can help you unlock geo-blocked content, keep an untraceable IP, and even use public Wi-Fis without any worry.
Pro tip: For the ultimate combination of privacy and performance, use a VPN over Tor. Our detailed guide on the topic explains how it works and how to get started with it if you need.
How to use onion routing safely – Best practices
Now that we have comprehensively explained onion routing, it’s time to explore how to use it. While onion routing is a safe protocol to use, it also needs extra precautions before you start using it.
There’s no rocket science here. But let’s show you some of the best practices:
Use a VPN (Optional)
A VPN is a go-to tool and a basic need in today’s digital world (when hackers and snoops are lurking around to steal your privacy). It gives you extra peace of mind and provides you secure online connection.
However, not all VPN services get the job done; the VPN should be as trustworthy as you trust yourself. We recommend NordVPN due to its dedication to users’ online privacy. Just connect, and it will encrypt your traffic before entering the Tor onion routing.
It’s not a must to use a VPN with this protocol. Regardless, it takes your privacy to another level entirely and adds another layer to your onion.
Keep your Tor browser updated
If you are using old software, that is another great area of concern because existing (known) security vulnerabilities can be exploited.
Make sure you frequently update your Tor browser to patch existing security issues. All those update notifications are more than just annoying; they are announcements that your digital shield is getting stronger.
Toggle off scripts and plugins
JavaScript and plugins in your browser can expose your real IP address or other sensitive information and defeat the purpose of using onion routing.
In the Tor browser settings, use “Safest” by default to disable these items. Here’s how you can select it:
- Open your Tor Browser.
- Tap on the shield icon on the right of the URL bar.
- Click “Settings.”
- Go to the “Privacy and Security” section in the settings.
- Scroll down till you find “Security Level” settings.
- Choose the “Safest” option.
- Then, click on “Save and restart” to activate it.
Utilize bridges if needed
In regions where you don’t have access to onion routing via Tor, Tor bridges help to bypass the censorship of onion routing. They serve as private access points into the onion routing network. So, it gets tougher for authorities to know if you use onion routing.
Do not sign into personal accounts
While using onion routing, do not sign into services that you think can expose your actual identity. This could be your email and social media profiles that carry your real names. Doing so is like wearing a mask and introducing yourself by your real name; the anonymity is compromised already.
Be conscious of metadata
Even after your content is encrypted by onion routing, don’t overlook the metadata. They often carry sensitive info like timestamps, document properties, file names, and more.
What you can do is use a reliable metadata remover like ExifCleaner to remove such info before sharing any files. Also, if you’re on the onion protocol, strong passwords should always be within reach. No matter the site, whether sensitive services or not, use passwords that are hard to guess.
Don’t use unverified Add-ons
Adding extensions to the Tor Browser adds attack surface and potential vulnerabilities to your use of onion routing. When accessing onion routing, consider using only the default browser settings for security.
Be conscious of legal risks
Although it might be legal to use onion routing in some countries, it can attract the attention of authorities given the statistics that many people use it for illicit purposes online. Be sure to know local laws and regulations regarding privacy tools you may use on the protocol.
Tor onion routing – The bridge to the dark web
Tor onion routing is the most famous version of onion routing. It works by routing traffic through multiple encrypted layers for anonymity while using the web and while accessing .onion sites on the dark web.
Here’s how it connects to the dark web:
Establishing an onion circuit
When you download Tor to connect to the onion routing protocol, the software automatically establishes a random circuit through three nodes.
This consists of an entry node (guard), a middle node (relay), and an exit node. An .onion circuit may include other “rendezvous points” to help both parties maintain full anonymity.
End-to-end encryption
The data sent between you and the .onion site remains in code form throughout the whole process. The exit node is not part of the layer where the data is decrypted at Tor, whereas with other websites, the exit nodes decrypt data to send you to your normal sites.
This is just another security benefit.
Hidden service directories
Tor onion routing implements hidden service directories that allow users to discover a .onion site without revealing their location.
When you enter a .onion address, the network will connect you through an encrypted path, with neither party knowing the other’s IP address. Thus, anyone can use the dark web safely without any surveillance or being traced.
FAQs
The protocol typically works with three layers of encryption to match the three nodes your information travels through (entry, middle, and exit nodes). This can change based on the protocol’s modus operandi or the privacy network itself. However, keep in mind that each layer has a unique server through which it travels within the network.
Certain VPN providers come with a unique feature that combines the privacy and security of a VPN with the onion routing benefits – the “Onion Over VPN” servers. They allow you to run the onion routing protocol with the Tor browser while being connected to a VPN server.
Onion Routing routes traffic through multiple nodes and layers of encryption for maximum anonymity. It’s much slower and complex to set up (unless you are not using Tor browser that does all the heavy work for you without you knowing). On the other hand, a VPN uses one encrypted tunnel to bridge your device and the VPN server. It’s fast and needs no tech know-how to establish. Think of onion routing as the Fort Knox of privacy, while a VPN is like a good home security system.
One can use onion routing for anonymous web browsing. It can provide secure communications, bypass censorship, and preserve your online identity. It’s a sturdy info security for journalists, activists, researchers, and so on.
It’s quite simple. Get the “Tor Browser” running on your device. Once the setup is complete, it routes your traffic through the onion routing network to Onionize your web traffic automatically. If you’re tech-savvy, you can customize which applications to run through the Tor routing. You can even host hidden services only accessible to the onion routing network. Nevertheless, always follow the best practices covered above in this article to be on the safe side (as much as one can).
