You’ve likely used a VPN before to stream content unavailable in your region or to secure your connection on public Wi-Fi. But decentralized VPNs (dVPNs) take that familiar concept a step further. While they still route and protect your internet traffic, they do so without relying on a single company or centralized server infrastructure.
Instead, dVPNs operate through a distributed network of independent nodes, which other users or community participants run. This means no single entity controls the network or holds complete access to your data. Privacy and trust are spread across the system rather than concentrated in one provider. Intriguing, right?
If you’re curious about how decentralized VPNs work, how they compare to traditional VPNs, and whether they’re worth using, you’re in the right place. This guide breaks down everything you need to know before deciding if a dVPN fits your privacy needs.
Quick Take: Yes. decentralized VPNs (dVPNs) represent a fascinating, niche evolution for censorship resistance and radical privacy. But they come with significant trade-offs. Mostly in in speed, ease of use, and consistency. For the vast majority of users seeking robust privacy online, reliable performance, and simple (out of the box) security, a mainstream, audited no-logs VPN like NordVPN accomplishes the core job—encrypting your traffic and hiding your IP (more effectively and reliably as a complete package).
What is a decentralized VPN?
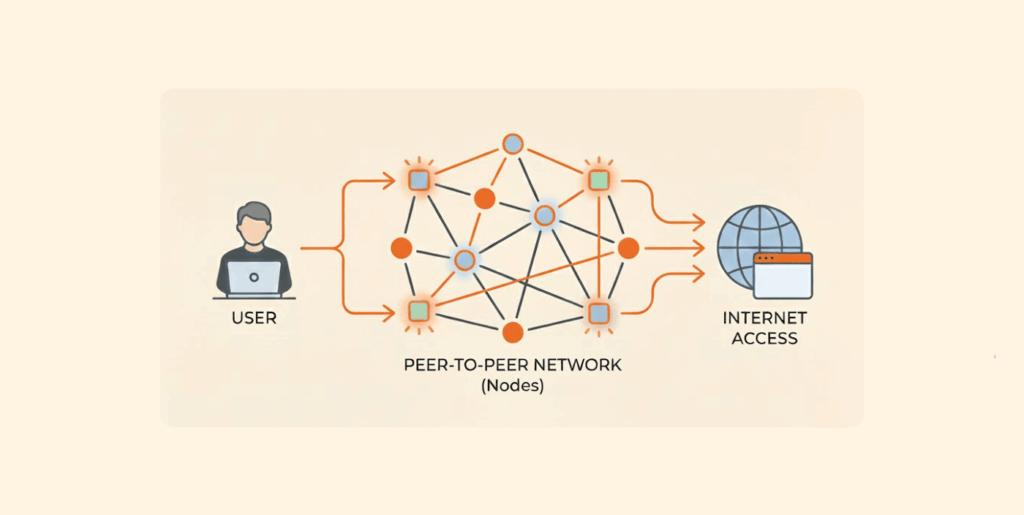
A decentralized VPN (dVPN) is a privacy tool that routes your internet connection through a crowd-sourced network of individual users’ devices, versus a company’s central servers.
Think of it as trusting all your money to one bank versus spreading it across hundreds of independent, neighborhood vaults. If that bank gets robbed, you may lose everything. However, if one vault gets robbed, your funds in the other vaults will still be safe.
Here is an example of how that looks:
The centralized VPN way
You open your VPN app and connect to one of the servers owned by the company you signed up with, like NordVPN or ExpressVPN. All of your internet traffic flows through their infrastructure. Your privacy relies solely on trusting their “no-logs” policy and their ability to protect their servers from hackers or legal issues. It’s a singular point of failure.
The decentralized VPN model
This system operates on a peer-to-peer network. Your connection isn’t passed over to a company’s server. It is encrypted and sent through several devices (referred to as nodes) hosted by other users around the world.
- That node could be someone’s home computer in Berlin.
- Or a device in a flat in Tokyo.
- Or a server in a data center in São Paulo.
The key here is that no company controls the path that your information takes. Instead, your data travels through a series of independent nodes, and no individual can see the complete path your data takes.
So, what makes this tick? Many dVPN services utilize blockchain technology. This handles node operations and payments transparently. Individuals who volunteer to share their bandwidth can earn cryptocurrency, and those who use it spend very small amounts of crypto to access the network (although, for a start, users can access some decentralized VPN free of charge using a free trial).
This process usually involves something called “multi-hop” routing. They split your data, encrypt it, and then route it through several nodes before it finally arrives at its final destination.
Using a regular VPN is more like taking a private taxi straight to your destination, while a dVPN is like carpooling with a group of strangers, all the while wearing a disguise and hopping from one random vehicle to another along the way. It will be nearly impossible to track your footsteps.
This multi-hop principle is also used in other advanced privacy setups. For a powerful combination that uses both a traditional VPN and the Tor network (which, seemingly, is the core idea behind all the dVPNs), our guide on what Onion over VPN is and its benefits explains how layering these tools creates an even more robust anonymity solution.
How does a decentralized VPN actually work?
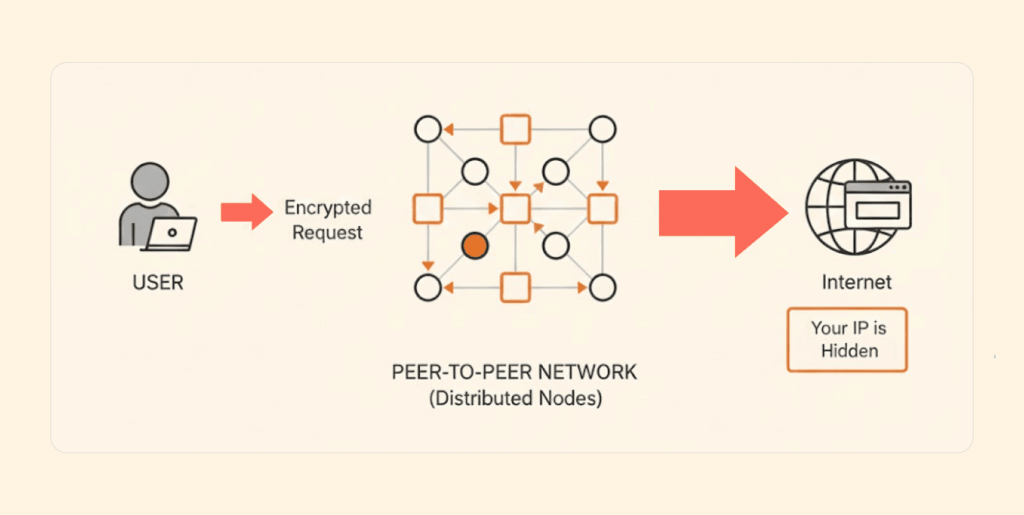
A regular VPN is quite easy to understand: you connect to a server owned by your VPN provider, and all the rest is done for you. A decentralized VPN device network is more complex but also really fascinating. It’s not magic; just a creative mix of peer-to-peer networking and encryption.
It all begins with the peer-to-peer (P2P) foundation. It’s kinda like a digital carpool system run by the users themselves.
- The node operators: People all around the world volunteer a bit of their internet bandwidth and use their devices as the “nodes”. It could be a home computer, a Raspberry Pi, or a dedicated piece of decentralized VPN hardware.
- The user’s journey: When you use a dVPN app, you are not linking to a company server. Instead, the app finds a way through nodes run by users. It encrypts your traffic, bounces it through a handful of these other nodes, and before taking you to the website, you are visiting safely and securely.
- The magic of residential IPs: Here’s the really cool thing about dVPNs. Since the nodes are on home connections, they utilize a residential IP address. It is more difficult for websites to block a residential IP than known corporate IPs from a large VPN data center. It’s more like borrowing an internet connection from your neighbor instead of using a corporate one.
- The built-in trust: There is no company headquarters for law enforcement to raid and no central server to seize or shut down. The dVPN exists as long as people continue to run nodes. Since it’s decentralized, there isn’t a single point of control—and that’s the whole point.
What about payments? Most dVPNs utilize a crypto payment system. Node operators earn tokens for sharing their bandwidth, and users spend tokens to access the network. It is both transparent and fully automated.
So where does your traffic actually go? Your data is transmitted in packets, and each packet travels a different route. The website you visit will never see your IP – only the IP of the last node. No single node operator can view where you began and where you ended up when you are using a dVPN.
This creates a system where users don’t need to place their trust in one corporation, but rather in a distributed protocol. Your data is not going to be sitting in one place.
Centralized vs. Decentralized VPNs: A head-to-head comparison

We have seen how dVPNs function; what does this imply for your everyday life? Let’s look at the differences between centralized VPNs and decentralized VPNs.
Decentralized VPNs use peer-to-peer networks and have nodes that are independent of one another, meaning that each one is run by an individual user, while a centralized VPN has one single company operating the entire service. This singular entity creates a space for censorship that doesn’t exist when there is no singular entity to target.
There is a downside, however; you often have to sacrifice speed and simplicity for that strong, distributed privacy. Since you could be creating a VPN connection through a number of residential nodes, you may receive a less direct connection than connecting to a server directly.
Furthermore, dVPNs are more complicated to set up than traditional ones and often involve cryptocurrencies. Plus, these VPNs have a reputation for not storing logs in a central place. However, there might be occasional logging at the node level to prevent abuse, such as IP blocklisting, spam, or DDoS attacks. A decent centralized VPN like NordVPN can offer the same level of privacy if it has strict, audited policies.
Let’s make it simpler with this comparison table:
| Feature | Centralized VPN | Decentralized VPN (dVPN) |
|---|---|---|
| Control and ownership | A single company is in charge. You trust them. | A peer-to-peer network with no central boss. |
| Privacy | Route your traffic through a secure tunnel. Good providers have audited “no-logs” policies. | Enhanced anonymity through node mixing. No central logs exist, making your activity harder to track. |
| Security | A “honeypot” target; if the central server is breached, data could be exposed. | No central point to attack. But be aware—a node itself could be run by a malicious actor (though they’d only see encrypted data). |
| Speed & performance | Speeds are often faster and more consistent on optimized company servers. | Slower and less reliable since the quality depends on each node’s connection. It’s nearly impossible. |
| Ease of use | Very simple to use. Download an app, click connect, and you’re done. | Can be trickier to set up, often involving crypto payments. Less hand-holding. |
| Censorship resistance | Vulnerable to government blocking since server IPs are known. | Very hard to block or censor because the network of nodes is always changing and growing. |
| Cost | Straightforward monthly or yearly subscription fee. | Usually, a pay-as-you-go model uses cryptocurrency tokens for bandwidth. |
So, which is better? It really isn’t an easy choice. Your selection relies on how much you value the raw, censorship-resistant capability of a dVPN or the dependability, speed, and simplicity of use a traditional service provides. In either case, research and read the Terms of Service before you select.
Advantages of using dVPNs
This is the main effect of choosing a decentralized network:
- Maximum censorship resistance: This is the star benefit. Since there is no central office or server farm that a government can target, blocking access is like trying to stop people in a large, moving crowd from talking. Almost impossible. This is particularly useful for journalists, activists, or anyone living in a part of the world where internet suppression is a reality. Also, this robust, hard-to-block nature is precisely why dVPNs are particularly popular among users and researchers of privacy-centric platforms like dark web sites, where maintaining access is critical.
- Radical privacy through anonymity: A regular VPN knows your IP address. With dVPNs, no single party, not even the dVPN network organizers, knows both who you are and what you’re doing online. The network blends your activity with that of other users, creating a very strong layer of anonymity that is hard to usurp.
- No central data honeypot: A typical VPN company is like a bank safe, a very attractive target for hack attacks. If hackers manage to breach it, it might affect millions of customers. On the contrary, a dVPN does not have a central vault. Your data is not stored in a central location, and you safely blast through a distributed network without anyone noticing. This model makes large data breaches practically impossible.
- Trustless operation: There is no need to gamble with your privacy on a company that simply claims a “no-logs” policy. With dVPNs, the trust is in the protocol and code. Trust doesn’t rest on the shoulders of anybody, and that is a revolutionary way to handle online privacy.
Potential drawbacks and challenges of decentralized VPNs
No technology is without flaws, and dVPNs are no exception. They represent a significant technological advancement in user privacy, but they are certainly not without their challenges. Here are some of the challenges to keep in mind before joining the decentralized movement:
- Limited network maturity: The dVPN ecosystem is still new. Many platforms are much smaller networks with limited nodes compared to traditional service-based providers like NordVPN, with over 8,000 servers. Quality of service may be inconsistent. Performance varies based on how active or reliable node operators are at a particular time.
- Performance issues: A decentralized VPN requires your data to traverse multiple independent nodes. There will, thus, be latency and reduced connection speed. Node operators are also using their personal bandwidth, so the level of quality you’d get on the network may not be consistent. Unlike traditional VPN service providers that use data centers with high levels of performance, dVPNs depend on a mix of residential and professional-level connections. They may, therefore, be a dealbreaker for streaming or anything that requires really good speed.
- Technical complexity: With decentralized VPN technology, there is often a steeper learning curve. Most of the platforms use blockchain technology to some degree. This often includes managing cryptocurrency wallets and engaging with consumer token-based payments, which may be overly complex, especially for non-technical users.
- Reliance on blockchain and tokens: The adoption of a blockchain adds some unique challenges. Since a token-based ecosystem utilizes volatile cryptocurrencies, predicting the cost of service becomes harder. Furthermore, the need to acquire or deal with cryptocurrency may also be off-putting to anyone who isn’t familiar with the digital wallet or the blockchain space.
- Limited geo-spoofing: The dVPN providers don’t often offer multiple choices of a specific country or city. You want to spoof “New York, USA,” for example? That location might not be available; instead, the location you choose depends entirely on where the node operators are. (Read our this article to explore the top centralized VPN services to use in the USA.)
- Security risks: Without robust verification processes in place, unscrupulous individuals could operate compromised nodes, allowing them to log in, access, or alter user data. Since dVPNs don’t have a central party controlling things, there is no one to hold responsible for ensuring security or resolving disputes.
- Lack of awareness and low rate of adoption: Decentralized VPNs as a technology have enormous potential, but at this time, it is still a niche offering. The larger scale and presence of traditional VPN services could hinder its growth. Additionally, users may simply find dVPN to be too complex.
- Regulatory concerns: The use of blockchain and cryptocurrencies as part of dVPN services introduces potential regulatory issues; some jurisdictions, such as Belarus, China, Iran, etc, consider these technologies illegal. Furthermore, in jurisdictions that have strict government control of the internet, dVPN services may become a target as part of an overall strategy to reduce online anonymity.
- Limited support: If something malfunctions, you are mostly on your own. There are community forums, but no committed group ready to assist you at any time. Troubleshooting becomes your responsibility.
- Missing advanced features: Split tunneling, protocol options, and automatic kill switches. Features available with traditional VPNs may not work well (or be absent) in decentralized networks.
Should these limitations scare you off? Not really. Just go in with your eyes open, and be fully informed. Decentralized VPN services are very good, and sometimes even better, especially when trying to evade censorship; however, in the day-to-day, the disadvantages outweigh the advantages.
Is a decentralized VPN safe?

This is a million-dollar question. The short answer is: they can be “very” safe, but the safety model is different.
The crux of a dVPN’s security revolves around its encryption. As with a traditional VPN, your data is encrypted before it ever leaves your device. Even if a node operator were to act maliciously, the operator would only see encrypted data, which they wouldn’t be able to read.
The safety advantage is really that there is no central data honeypot. A traditional VPN company is a much higher value target for hackers than a dVPN because, if hacked, the hacker could access the data of millions of users all at once.
A dVPN (decentralized VPN) does not have a central server to hack. Your activity is dispersed across the network and, thus, all of your web traffic is essentially untrackable and very hard to track or seize.
It’s actually a give-and-take; you’d be trading guaranteed performance from a corporate service for better privacy and resistance to attack.
Are decentralized VPNs legal?
Most countries consider using a dVPN equally as legal as using a traditional VPN. In either case, all they do is offer you enhanced privacy and security, and there’s nothing illegal about that.
It all depends on what you do with them. Whether you have a dVPN or a regular VPN, anything you do that is illegal remains illegal. Just because it is decentralized doesn’t mean it will give you immunity from the law.
There is one gray area for node operators, though. If you are operating an exit node in certain countries with restrictive internet laws, you could be liable for whatever traffic that passes through it, even though the traffic is encrypted. Anyone running a node should first check the rules in their country.
For the average end-user simply connecting within the network, it won’t put them at significant legal risk, just like when using any VPN.
Should you use a decentralized VPN?
Are you considering switching? Here’s a short guide.
You may love a dVPN if:
- You value privacy above all else and don’t trust any company.
- You are either comfortable with or want to learn about cryptocurrency.
- Your main use case is true anonymity, and you can live with fluctuations in speed.
You may be better off with a traditional VPN if:
- Your main goal is to reliably stream geo-blocked content (like Netflix movies).
- Sometimes you need a reliable ultra-high-speed connection for gaming or large downloads.
- You just prefer to keep things simple with a flat monthly payment via credit card.
How to buy and use a decentralized VPN

The process differs from subscribing to a typical VPN service since you won’t just enter your credit card number.
Step 1: Select your desired service
Choose the service you prefer that meets your requirements, your technical skills, and location from the list of decentralized VPN services we provided in the section below.
Step 2: Create a cryptocurrency wallet
Most dVPNs allow payment in crypto. You’d need to open a wallet that allows the token the service accepts (e.g., MYST, OXT, DVPN). MetaMask is a popular wallet choice, and it allows a variety of tokens. You can download it as an extension to your web browser or as a mobile app.
Step 3: Purchase tokens
Buy the cryptocurrency token from an exchange. Top exchanges like Coinbase or Binance often list popular dVPN tokens. You’ll then need to transfer the tokens to your wallet. Double-check for accuracy when inputting the wallet address, as you could lose your money forever if you input even just one wrong character.
Step 4: Download the dVPN application
Go to the official dVPN service website and download the appropriate app for your device. You must be sure you are on the official site and not a phishing scam. Verify the download signatures if you are techie enough.
Step 5: Connect your wallet
After downloading the dVPN application, open it and connect to your cryptocurrency wallet. This is what allows your tokens to be used for payment and, as such, will link your tokens to the usage of the service. The application will walk you through the authorization process. Since they use a pay-as-you-use model, you’ll have to pay for only what you use, and it’s often very affordable.
Step 6: Configure settings
You may choose your preferences here; services let you select regions or connection types, while others will automatically route you through the best available nodes. You may also have the option to set up any kill switch features.
Step 7: Connect
Click the connect button, and the app will find you the best nodes and then establish your connection. This may take longer than a traditional VPN service, especially on smaller networks.
Step 8: Test your connection
Verify your IP address to ensure that the IP address showing up is not your real one, but the VPN’s. Test for DNS leaks at a site like DNSLeakTest.com.
List of decentralized VPN services
Interested in trying out a decentralized VPN? If so, here is a sampling of decentralized VPN options that may be worth your consideration. Each one has its own strengths and limitations.
1. Mysterium network
This is probably the most established name in the decentralized VPN space. Mysterium has thousands of active nodes across 100+ countries, providing nice global coverage. It uses residential IP addresses, making it a better option for bypassing VPN blocks. Payment is in MYST tokens. The mobile apps are surprisingly easy to use, which is not common with decentralized services.
- Established network with wide geographic coverage.
- Residential IPs are good for bypassing blocks.
- Requires managing MYST tokens.
2. Orchid
Orchid is Ethereum-based and takes a different approach than average VPN services. It utilizes a multi-hop routing, which means your traffic bounces through various VPN service providers and not just peer nodes. You pay per gigabyte using OXT tokens. The app is cool, but the pay-as-you-go pricing may get costly if you are a heavy user.
- Multi-hop routing through various providers can enhance anonymity.
- Flexible, pay-as-you-go model (OXT tokens).
- Can become expensive for heavy usage.
3. Sentinel
Sentinel (or dVPN) is part of the Cosmos ecosystem and focuses on enabling a white labeling structure. It allows developers to build VPN services on top of the Sentinel network infrastructure. The currency used is DVPN tokens, and it also claims zero logging. It might be smaller than Mysterium, but it’s growing really fast.
- Focus on infrastructure for developers (white-labeling).
- Growing network.
- The DVPN token ecosystem is smaller.
4. Deeper Network
This service is unlike the others, as it is a mostly decentralized VPN hardware option. You buy a Deeper Connect device that you plug into your router. This requires just a one-time purchase of the hardware; there are no subscription fees afterwards.
The device routes your traffic through the Deeper Network. This option is very straightforward to use, more like plug-and-play, but it will require the up-front costs of purchasing the hardware.
- Hardware-based solution (Deeper Connect device).
- One-time purchase, no ongoing subscription.
- Less flexible than software-only solutions (tied to your router).
5. Lokinet
Built by the Oxen project, Lokinet is a VPN service similar to Tor as it uses onion routing, but with some enhancements. It is resistant to timing attacks and provides better speeds than Tor. It is free to use as it’s hosted by the service node operators of the Oxen blockchain. However, it’s a more technical option than some alternatives.
For the foundational technology it builds upon, learn about the strengths and safety considerations of the original Tor Browser itself.
- Advanced privacy via onion routing, resistant to traffic analysis.
- Free to use (community-supported).
- Considered a more technical option for users.
6. NYM
NYM takes a different approach, focusing on protecting the metadata of traffic instead of the content itself. The NYM architecture, called mixnet, makes it very difficult to analyze traffic. Although it is still in development, it’ll be a very strong option in the future. It has a token called NYM, which users use to pay for the services and for node operation.
- Next-generation focus on protecting metadata (mixnet architecture).
- Strong promise for future high-level anonymity.
- The ecosystem and user experience are likely still maturing.
7. deVPN (by IVPN)
A latest addition from a reputable traditional VPN provider is attempting an interesting model of combining a professional service with a decentralized service.
To choose the best decentralized VPN provider for your situation, check the size of their node network, the cryptocurrency that they are using, and user reviews of their application.
- Suggestions for everyday use: Try to check your token balance regularly. Running out of tokens mid-session will abruptly cut you off. Look at the app speed; if it seems like it is slow to respond, you may want to disconnect and then reconnect your phone to look for a better node. Update the app if you need to.
- Backed by a reputable traditional VPN provider (IVPN).
- Attempts to combine professional service with decentralization.
- Details on the exact hybrid model and its implementation are crucial to evaluate.
FAQs
While the primary service isn’t free, most networks provide free bandwidth offered as a trial to new users. They may give you 5 – 10 GB free of charge to test their service, and afterward, you’d need to pay for the service using crypto.
As a user, you need no special hardware. Any computer or phone will work. If you intend to run a node and earn tokens, you can also do so on a regular computer, Raspberry Pi, or by installing a custom firmware on a compatible router.
Very private. Since you will be sharing as well as mixing your traffic with many other users, and no central log to check, it is extremely challenging to trace activity to you. Any system will have privacy and anonymity challenges associated with it, though. But your privacy measures will also depend on your own habits and activities while using it, like not logging into a personal account, for example, while accessing that VPN.
The main reason is to earn cryptocurrency. Users can earn passive income by sharing their unused bandwidth. Others do it in the spirit of creating a free and decentralized internet.
Sometimes yes. Due to the decentralized nature, there isn’t a central server for copyright trolls to target. However, the inconsistent speeds may be a turn-off for larger torrents.
Most dVPN apps will automatically connect to another node if the current node goes offline. That usually takes a few seconds. Some services have “seamless failover,” which maintains backup connections in the background. You might notice a brief blip in connection, like when your home internet goes down temporarily. But more premium services will maintain connection pools, so the interruption will be as minimal as possible.
Yes, but results can vary. Decentralized VPNs utilize residential IP addresses rather than data center IP addresses, which are more trusted by streaming services and will therefore (in general) not trigger VPN detection. Oh, and quality and speed can change depending on the nodes you connect through. For 4K streams, you’re better off with a traditional VPN.


