While browsing online, you might have noticed that the websites you are visiting have URLs starting with http. It is either ‘http://’ or ‘https://’. HTTP, which stands for Hypertext Transfer Protocol, sends data as plain text and is subject to interception. HTTPS, Hypertext Transfer Protocol Secure, transmits data in a secure way and practically makes it almost impossible for eavesdroppers to monitor (third-parties like your ISP can still see top-level domains you visit).
Both, HTTP and HTTPS are protocols used for data transfer, but they are different in many aspects. But, one being securer than the other is the main difference. In short, HTTP is insecure, but HTTPS is secure.
This article compares HTTP and HTTPS, what the two protocols do, and how they perform their tasks — and most importantly, help you understand why you should be concerned about your online privacy and start using ONLY HTTPS sites.
HTTP vs HTTPS – At a glance
The table below provides a quick overview of the key differences between HTTP and HTTPS:
| Feature | HTTP | HTTPS |
|---|---|---|
| URL prefix | http:// | https:// |
| Security | Insecure (plain text) | Secure (Network encrypted via SSL/TLS) |
| Port | 80 | 443 |
| Certificate required | No | Yes (SSL or TLS Certificate) |
| Cost | Free (no certificate needed) | Free or Paid (depends on certificate, if needed) |
| Performance | Slower (with modern protocols) | Faster (with HTTP/2 and HTTP/3) |
| Google’s stance | Google Chrome marks as unsafe | Positive (Google prefers it) |
| Port number | It uses port number 80 | It uses port number 443 |
| Trust signal | In browsers – “Not Secure” warning | In browsers – Padlock icon |
| Data transferring network | Transfers text, images, video, and through web pages | Transfers data securely through a network |
| Transparency | Anyone on the server can see your data | No one can intercept your internet traffic due to its secure connection |
What is HTTP?
Hypertext Transfer Protocol (HTTP) simply describes how to communicate over the internet. Think of it as computers’ language to connect as human use different languages to talk to each other.
It is the basis for the World Wide Web, which is primarily a communication protocol between a web server and a web browser.
When you enter an address on your web browser, the browser creates an HTTP request to the server to get an HTTP response, which contains all the information necessary to put the web page data together.
The fundamental flaw with HTTP is that it is a plain, unencrypted conversation. Think of it as equivalent of sending a postcard through regular mail. Anyone who gets his hands on that postcard, from the postal worker to a bad actor, can read its contents.
As such, if you enter your credit card information on an HTTP website or log into an account, you will expose everything you do. This is why the question; Is HTTP secure has a very clear and distinctive answer: No.
How does HTTP work?
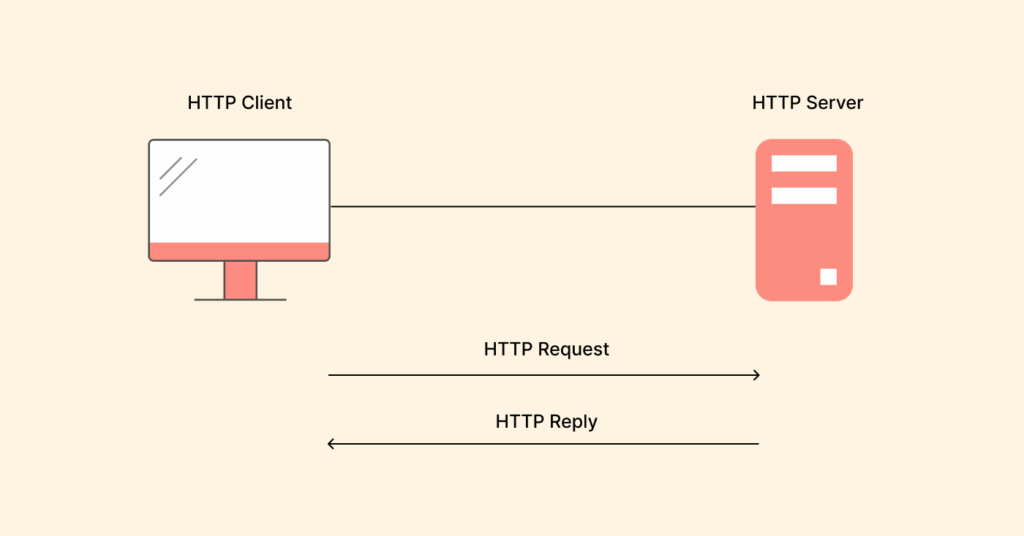
HTTP is a client-server, request-response protocol. Since HTTP is a stateless protocol, every request is a distinct transaction or a new request. The server doesn’t remember a prior request. Below is how it breaks the process down:
- Request: The user initiates the first action, which provides a URL or activates a hyperlink. The browser (client) generates and sends an HTTP request message to the server. The request is inclusive of the URL location of the resource, the method of transmission (GET, POST, etc.), and “metadata” about the client description (the user’s browser).
- Server processing: As soon as the request reaches web server, it processes the request and generates a response. Also, the server searches for the requested file or resource to identify it and constructs the content before it returns the response.
- Response: The client will get an HTTP response from the web server. This will contain some meta information regarding the HTTP headers and an HTTP status code (usually a 200 response if the requested resource is found and a 404 if it doesn’t exist). It will then proceed with the response to the web page (often contained as HTML, images, or text). The server can also give 500 Internal Server Error (along with a human-readable message) if there is a server-side issue.
- Display: Once it receives the response, the browser displays the webpage on the user’s screen.
Since HTTP protocol doesn’t encrypt data, all of that is done in plain text and is unencrypted. That means HTTP is insecure. The unencrypted internet traffic transfer of HTTP makes it easy for others to see the data being exchanged.
What is HTTPS?
HTTPS (Hypertext Transfer Protocol Secure) is a secure version of HTTP, where the S stands for “Secure.” As the name hints, HTTPS is successor of HTTP with an extra layer of encryption to scramble the data sent between a web server and a user’s browser.
Think of it that first most of the people used to send messages using a postcard (HTTP) and they later started using a secure locked box (HTTPS). With HTTP successor, HTTPS, the data is encrypted on your end, so it leaves your device encrypted, and then it gets decrypted only on the secure server on the other end.
This means anyone trying to intercept your data—including your ISP—will only see scrambled, unreadable information. It’s akin to knowing a message is being sent but being unable to decipher its content.
How does HTTPS work?
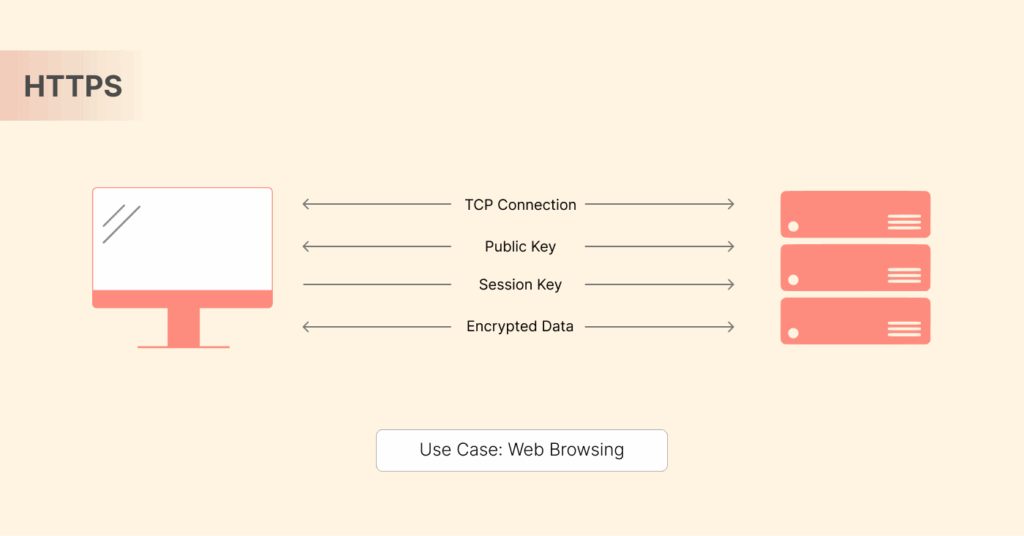
HTTPS uses a critical technology called SSL/TLS. For instance, you can view SSL/TLS as the lock and key for the secure box used above. Notably, HTTPS uses three stages as follow:
- SSL/TLS handshake: Initially, there is a “handshake” between a user’s browser and the web server when a user attempts to connect to an HTTPS website. They will negotiate a shared secret key that will only be used as the session key.
- Certificate trust: After that, the web server sends its SSL/TLS certificate to the user’s browser. The browser checks whether the SSL certificate is from a Certificate Authority (CA) that the browser trusts. If there is no established trust, then the user will see a security message from the browser showing that the certificate might be invalid/untrusted. All this mediation by Certificate Authority helps stop man-in-the-middle attacks as it enables verifying the identity of a service or website by issuing a digital certificate containing that entity’s verified public key.
- Data encryption: Once the handshake is completed and the browser and server have established trust, the data sent from the web browser and web server will be encrypted using an SSL/TLS symmetric key. The encrypted data will be sent over the internet to the intended recipient, and only the intended recipient can decrypt the data.
While the above process might look time-consuming, the whole operation is performed in virtually no time at all in the background. Thus, your browsing experience is the same as browsing an ordinary HTTP site, the unsafe site that doesn’t have encryption. The technical sounding of HTTP and HTTPS full form may seem complex, but the result is simple: one is open for everyone to see, while the other is a secure private conversation.
What’s the difference between HTTP/2, HTTP/3, and HTTPS?
Alright, HTTP and HTTPS are the two key data transfer protocols for communications, right? As the names suggest, HTTP/2 and HTTP/3 are simply updated and more efficient versions of HTTP. However, since they also don’t have that ‘S’ added to them, they can’t provide encryption either (just like HTTP). Then why HTTP/2 and HTTP/3? We hear you ask. Below we explain differences between them and simple HTTP.
HTTP/2
It’s an updated version of HTTP, standardized in 2015, with a focus on improving performance for loading websites by allowing multiple requests to be sent simultaneously over a single connection to decrease load time.
Though it still operates without encryption, almost all web browsers mandate (or at least recommend) that HTTP/2 use an encryption mechanism via an encrypted HTTPS connection. Depending on how you look at it, they are considered a package deal.
HTTP/3
You see ‘3’ added to it? This tells that it’s the successor of HTTP/2. HTTP/3 is the latest major revision of the HTTP protocol. The biggest difference comes from the use of an alternate transport layer protocol called QUIC, which replaces TCP.
QUIC protocol was built to reduce latency and it claims to have the absolute minimum performance under suboptimal conditions, which is especially important in mobile networks when stability can slip unexpectedly. Much like HTTP/2, HTTP/3 may also be deployed via a secure protocol (TLS) and is related to, as well as used within, an HTTPS ecosystem.
In a nutshell, the primary difference between HTTP/2, HTTP/3, and HTTPS is that HTTP/2 and HTTP/3 focus on maximizing performance and efficiency, while HTTPS implies securing assets with encryption and authentication.
Nevertheless, all three protocols are aimed towards giving an end user a better experience with HTTPS focused more on secure online experience and not going hard after performance like the other two.
What are the different types of SSL/TLS certificates?
Whenever you see the padlock symbol in an address bar, it represents a type of SSL/TLS Certificate in use. Not all certificates are equivalent, as there are different levels of security and verification.
Domain Validation (DV)
This is the most prevalent and basic type of certificate. In this case, the Certificate Authority (CA) only confirms that the person or organization requesting the certificate actually controls the domain name. It is inexpensive, easy to obtain, and secures the connection.
However, it does not provide a significant degree of identity validation. You will see this SSL type typically on most of the blog and information websites who don’t usually ask for sensitive information from users.
Organization Validation (OV)
OV certificate not only requires the CA to validate ownership of the domain, but it also takes the identity or organization legitimacy into account. When someone applies for this type of SSL, the CA performs background check to confirm the legal name and address of the company and validate its real existence.
This is a much more trustworthy certification for consumers to see. Mostly small businesses and e-commerce platforms use this.
Extended Validation (EV)
It offers the most validation and trust (as the word ‘extended’ in it suggests). In this case, a CA performs a full background check of the organization before issuing the EV certificate. Extended Validation certificates are exclusively issued to verifiable, registered businesses, government identities, or organizations. Individuals cannot obtain an EV certificate.
When someone applies for it, the certificate authority confirms not only the physical address of the organization, but it will also validate the identity of the organization and its legal existence. EV certificates are the most common for major corporations, banks, and big e-commerce businesses that must prove trust for a website or platform.
HTTP vs. HTTPS: Advantages and limitations
Swapping from HTTP to HTTPS is not simply like including a padlock that looks better. There are many benefits to using HTTPS that help (we better say protect) the user and website owner.
Like anything else, there always seem to be considerations of advantages and disadvantages within both protocols:
Advantages and limitations of HTTPS
Advantages
- Data integrity and security: This is the best benefit and the most important aspect if you ask us. HTTPS encrypts your data and protects it from third-party monitoring. While every page should be secure today online, given the rising cyber threats, this is especially critical for anything requiring user input, such as a log-in form or payment page.
- Improved search engine optimization (SEO): Google has revealed that they prefer pages that are HTTPS compared to competing sites that use HTTP protocol as a ranking signal since 2014. These improvements reduce risks for both the site owner and the user, which result in better user experience.
- User trust and branding: Trust and credibility are among the most important traits of any business. These two traits cannot be touted enough whether someone has an online company or a local business. The padlock icon that “https” brings in the address bar give some social proof to visitors that it is safe to interact with a particular website.
Limitations
- Slight performance overhead: Encryption and decryption takes some additional processing power and hence can make client and server communication data transfer slow. Nonetheless, with up-to-date hardware and the more efficient TLS protocols such as HTTP/2 or HTTP/3, the overhead is minimal, and is no longer an appropriate reason to not use HTTPS protocol.
- Cost and complexity: The implementation of HTTPS requires buying an SSL/TLS certificate (though there are many free ones now) and configuring it correctly on the server. This would generally require some additional complexity, but again, the advantages far outweigh the disadvantages. Nevertheless, some none profits such as Let’s Encrypt, offer free SSL certificates so this takes cost out of the equation in reality.
Advantages and limitations of HTTP
Advantages
- Simplicity and speed: HTTP is a very straightforward protocol. Without encryption or certificates involved, it is easier and faster to implement, as it is not burdened by the overhead of security details.
Limitations
- Security vulnerabilities: HTTP sends data as an ordinary, plain text, and is ethically exposed if no one at least tries to protect it at the endpoints. In worst-case scenarios, bad actors could intercept data, read it, which could contain usernames, passwords, financial data, etc. Once that starts to rain down, then you are opening up Pandora’s box. So, lack of security is the worst thing about HTTP.
- Data integrity: HTTP will not guarantee that the data is delivered to you unmodified and uncorrupted. An attacker can readily inject malware or unwanted ads into the traffic stream without your knowledge and consent.
- Obsolete technology: HTTP is a relevant protocol, but it is rather outdated. It does not permit new web functionalities that are attributed to modern websites, which are data-heavy and complex, such as multiplexing and sending parallel requests. Generally, web pages deployed on secure HTTPS today are faster than their non-secure counterpart.
Why choose HTTPS over HTTP

We think the question of choosing between HTTPS and HTTP is outdated. HTTPS is no longer an option; instead, it’s a must. There are a lot of reasons to do so, ranging from technical to practical, all with implications for everything from your site’s security to gaining users’ trust.
Security
This is the most important reason (one cannot emphasise it enough no matter how hard they try). HTTPS provides three key security aspects:
- Encryption: It encrypts all data in transit, so even if a hacker intercepts the data, they can’t steal anything (they can’t log your credit card number, address, or login credentials).
- Data integrity: An HTTPS connection provides absolute assurance that your data isn’t altered or messed with as it makes its way through the transition “pipe.” Thus, a malicious actor cannot inject malware or an unwanted advertisement into your data exchange.
- Authentication: This demonstrates intended site communication and not an imposter. You can use this as a base for protection against phishing scams.
Performance
Even if HTTPS looks slower than HTTP given the technicalities involved, you shouldn’t be thrown by that claim. With the modern protocols we have today (HTTP/2 & HTTP/3), HTTPS has become faster — and it keeps improving everyday.
HTTP/3 has a multiplexing capability that sends multiple, independent responses and requests over a single connection that is persistent. It’s a critical feature that HTTP/3 protocol inherits from QUIC, its underlying protocol. HTTP/3 uses UDP with QUIC (unlike HTTp/2’s TCP use), which allows it to bypass transport layer head-of-line blocking. What does that mean? It’s not that technical. Hold on. That means, if one packet loses in a stream, it won’t delay all other streams active on the very same connection, leading to significantly improved performance.
Search Engine Optimization (SEO)
Search engines including Google prioritize HTTPS and even have included it as a ranking signal. Today, in 2025, and beyond, if you are not using HTTPS, it will be nearly impossible for your business to get visitors from search engines such as Bing and Google. Browsers, such as Chrome, are starting to label HTTP sites as “Not Secure”, causing visitors to avoid such sites out of fear and thus increasing bounce rates.
How to shift from HTTP to HTTPS
If your website is using HTTP, you should make the transition to a secure web server. It’s an easy process, and it will be worthwhile:
- Get an SSL/TLS certificate: The first step you need to take is to obtain a certificate from a Certificate Authority (CA). Numerous hosting providers and Certificate Authorities (CA), such as Let’s Encrypt, have certificates that are FREE (or at least a significant discount), which leaves you without an excuse not to have a certificate.
- Install the certificate: Next, install the certificate on your web server. The installation process of the certificate may vary based on the host, but usually, the hosts have simple instructions or are automated.
- Redirect everything: The last step is to redirect everything from your old HTTP site to your new HTTPS site. This way, all visitors, including website crawlers, using your old site are sent to the secure version automatically.
Is HTTPS setup more expensive than HTTP?
In the past, setting up HTTPS was arguably a much more costly and complex task than HTTP. However, that is no longer the case.
- Cost: The cost for an SSL/TLS certificate can be free or thousands of dollars, but most sites will be able to get quality SSL/TLS certificates free from providers such as Let’s Encrypt. In addition, many hosting companies offer free SSL certificates as part of their regular packages. So, finding a free SSL is even easier.
- Complexity: The installation of an SSL/TLS certificate is now a one-click process as provided by most modern Content Management Systems (CMS) and hosting companies. The simplicity of setting up HTTPS even for first-timers is now incredible.
In short, there is no longer a real significant cost and complexity barrier for setting up or switching to HTTPS. The security and performance advantage of HTTPS well outweighs any minimal effort needed.
FAQs
No, you should avoid browsing any HTTP website, but most importantly, do not submit any sensitive information on any such website or platform. Any data that would be submitted is not encrypted, and hackers or third parties can easily compromise your data.
A website is able to set up a server to respond to both types of traffic. In a perfect setting, the HTTP traffic should automatically redirect to an HTTPS route at the back end. With such changes, users would always land on the secure version of the site.
Having an HTTPS secure page that contains images, scripts, or any other form of content over insecure HTTP is a mixed content error. Such content over insecure HTTP has a high probability of security attacks, and as an attempt to mitigate such security issues, web browsers tend to block such content that is likely to cause security issues. Often, web browsers try to fix such errors by failing to display parts of the page.
The distinction, or difference, between HTTP and HTTPS is simply about security. By default, data is transmitted over HTTP in clear text and can be very quickly captured and read. Using the HTTPS protocol, there is no clear text transmitted; data is encrypted as it travels between your web browser and the web server.
