Thinking of taking a trip to the dark web? Your everyday browser won’t cut it. Not only will it not work, but it’ll also leave a big digital footprint.
You need the right tool for the job. A dark web browser. This is not about fear; it’s about smart privacy. We’ve listed the 10 best dark web browsers for 2026.
Let’s find your key to safe access to the best dark web sites and anonymous browsing. Here, curiosity is welcomed, but safety is paramount.
Legal Disclaimer: The information provided in this article (like any other page on our website) is for educational and informational purposes only. Regardless of your browser, accessing the dark web carries inherent risks, including potential exposure to malicious software and illegal activities. That means you can either infect your device or face legal action, depending on your use. The tools mentioned themselves are legal in most countries. However, their use for any illegal purpose or malicious activity is strictly prohibited almost everywhere worldwide. We, at PrivacySavvy, discourage any unlawful activities and do not endorse any such actions. You are solely responsible for complying with your region’s laws that apply and for ensuring your anonymity and security online. Proceed with caution and at your own risk.
Top browsers for dark web – Quick list
- Tor Browser: Gold standard for accessing the web anonymously.
- I2P: Robust network that is geared toward maximizing anonymity.
- Subgraph OS: Secure and hardened OS to run specifically a privacy orientated browser.
- Whonix: Workstation that is geared towards running applications anonymously over Tor.
- Mozila Firefox: Popular web browser made private by utilizing specific configurations.
- Waterfox: Quick and privacy-friendly fork of Firefox.
- Opera: Top mainstream web browser that includes a free VPN.
- Brave Browser: Blocks ads and trackers by default for a better overall user experience.
- Epic Privacy Browser: Chromium based browser that is focused on user privacy.
- Tails: The Amnesic Incognito Live System; it is a live operating system designed to leave no trace.
What is the dark web, and why is it important in 2026?
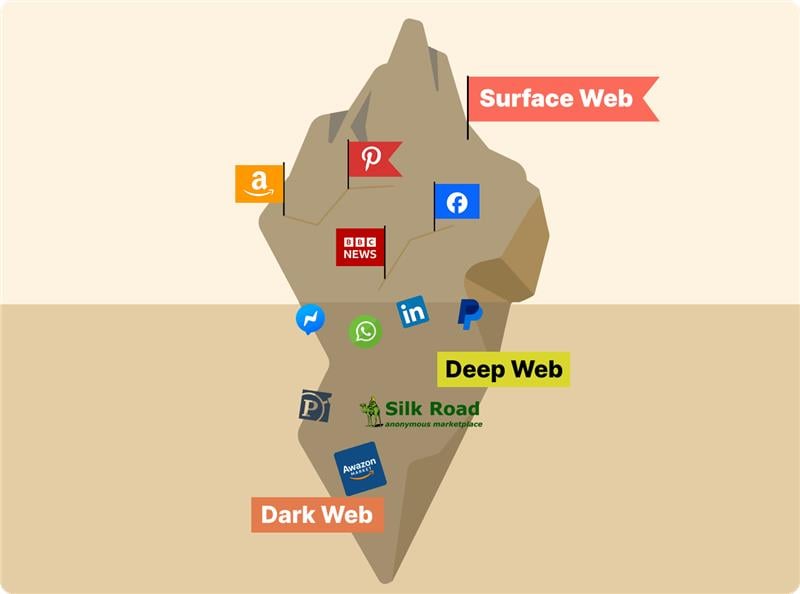
Picture the internet like an iceberg. The tip above water is the “surface web.” That’s where you have those sites you find when you search Google. Facebook, X, LinkedIn, YouTube, Amazon, and the rest of the websites you use daily.
Just below the surface is the gigantic “deep web.” Here, you’ll find all things that require a login, like your email, bank account, corporate intranet, government databases, etc.
The bottom part of the iceberg is the “dark web.” This is the tiny chunk of the internet that is intentionally built to be hidden away and cannot be accessed using standard web browsers.
To access the dark web, you must have specialized software, such as the Tor Browser. This separation is important. It creates a space for staying anonymous, which itself is kind of a double-edged sword.
Best dark web browsers today – Detailed list

Now, let’s go into detail about each of these secure, private browsers to access the hidden part of the internet:
1. Tor Browser
The Tor Browser is the most popular way to access the dark web. While not all Tor users are deep, dark web users, over 90% of the users who are interested in accessing the deep, dark web use Tor to access it.
The browser routes your traffic through a global network of volunteer-run servers (sometimes called nodes), encrypting your data and masking your IP address multiple times.
It is free, open-source, and based on a hardened version of Firefox. DuckDuckGo is the default search engine of the browser. For most people, it will be the best and safest starting point. It is the closest thing to a full dark web online anonymity suite.
Tor Browser has an official Android app if you want to use it on mobile. For iOS users, while there’s no official Tor app for iOS, a couple of options, including Orbot and Onion Browser, recommended by the Tor Project itself, exist.
- Gold Standard Anonymity: Its multi-hop encryption is unassailable when it comes to masking your location and identity
- Zero Configuration: You simply install it and go; it is pre-configured for secure access (of onion sites regular browsers cannot access) right out of the box
- Large Networks: It is supported by a large, active community of developers, advocates, and users, which continually bolsters its security
- Sluggish Speeds: All that routing and encryption can make the browsing experience feel like you are stuck in molasses
- Easy to Flag: Many of the most popular websites and services can detect and block traffic from the Tor network
2. I2P
I2P is another powerful anonymity network. Some people regard it as a more decentralized and resilient alternative to Tor. While the Tor Project relies mainly on a centralized directory of relays, I2P uses a distributed dynamic routing system, which makes it a much more robust alternative.
It can access the regular internet through “outproxies,” but that’s not its strongest suit. I2P’s most attractive angle is to access its own internal eepsites, which are its version of .onion sites. It is definitely a strong contender for the best, strongest, layered encrypted web browser.
- Decentralized Powerhouse: There is no central authority; its distributed framework means that it is hard to attack or take down
- Strong Support on Internal Services: Great at hosting and accessing hidden sites (Eepsites) within its network
- Steep Learning Curve: It’s not as user-friendly as Tor, and may be somewhat difficult for beginners to configure correctly
- Not for the Regular Web: Accessing the regular internet (“outproxy”) is slower and less reliable than on Tor
3. Subgraph OS
Subgraph OS is more than a browser; it is an entire operating system focused on security. The built-in browser is hardened for maximum privacy, and it is integrated with the OS’s security features.
It uses sandboxing to keep each application isolated from the other, preventing a breach in one app from spreading across the whole OS. This is a good option if you want a dedicated machine for sensitive browsing, because it is made to resist complex attacks.
- Fortress-level security: When we say the entire OS is hardened, we mean it (based on tests). Its entire sandboxing quarantines any threats, preventing them from spreading from a single incident
- Paranoid by design: Built from the ground up to counteract even the most sophisticated and/or targeted malware attacks
- All or Nothing approach: You have to install a whole operating system, making it impractical for casual use
- Niche Community: Smaller user-base leads to less support and slower development as opposed to some of the “giants” like Tor
4. Whonix
Whonix takes a very different approach to anonymity. It is made up of two virtual machines – a Gateway and a Workstation. All traffic must always go through the Tor network through the Gateway. This architecture protects your IP address even when the Workstation is before malware that may compromise it.
It is perhaps the most secure way to run applications anonymously. If you want a strong setup that has no leaks, Whonix might be the best dark web browser solution on the market.
- Unmatched Leak Protection: Its dual-VM architecture is reliable enough for security. Your real IP address is protected…even if you are hacked!
- Forces all traffic through Tor: You cannot bypass the anonymity network by mistake…you must use it
- Resource Intensive: Running multiple virtual machines takes a fairly powerful computer with ample RAM
- Complex Setup: The initial setup is more complicated than just installing a single app
5. Mozilla Firefox
The standard version of Firefox is not private enough for the dark web. However, with a little bit of configuration, it can be hardened into a capable tool. Hardening Firefox involves a lot of tweaking: config settings, disabling telemetry, and installation of privacy extensions such as HTTPS Everywhere and NoScript.
Although it requires more work, it provides tech-savvy users with a more familiar interface with better security for accessing Tor through a proxy.
Fun fact is that Tor Browser (Tor network is a different thing than the browser) is built from Firefox ESR (Extended Support Release), a modified version of Firefox. So, it’s worth using Firefox if you’re up for the tweaks needed.
- Full Control: Ideal for people who want to customize every single privacy and security setting themselves
- Home Everywhere: You get to use a browser you already know but is now a much secure version
- You Security Emphasis: The burden is on you; one wrong config setting can create a door every hacker would love to exploit
- Time-consuming: It’s going to take you considerable time to research how to do all the hardening steps and then carry them out
6. Waterfox
Waterfox is an open-source fork of the Firefox project. Its main appeal is that it offers more privacy and supports legacy Firefox add-ons. It also eliminates data collection, telemetry, and other suspicious code modern web browsers tend to use, which are troubling at best.

Though it still requires being routed through Tor (it is not a deep web browser by itself), it provides a clean, quick, and privacy-respecting base to use for your anonymous browsing sessions.
- No Data Collection: Provides a clean, fast browsing experience, without any telemetry and data collection
- Freedom to install extensions: Great support for legacy Firefox add-ons that have dropped in newer browsers
- No Standalone: Unlike hardened Firefox, there is some manual setup to be done in order route through Tor safely
- Smaller Development: Timelines for updates and patches might not be as fast as mainstream browsers
7. Opera Browser
Opera is a known browser with one significant advantage: it comes with a free, no-subscription VPN. The VPN encrypts your traffic and hides your IP address so that on the surface web, your information is kept private.
However, it’s important to note that this built-in VPN is not designed to connect directly to the Tor network or .onion sites. For general privacy on the clear web, it’s a really good option. But it’s recommended that you stick to Tor Browser still for true dark web access.
- Built-in Convenience: The free, built-in VPN is a killer feature for rapid and easy privacy on the surface web
- Easy to Use: Has a neater, more modern interface, which makes it very easy for anyone to just open and use
- False Sense of Security: Although there is a VPN, it is not for the dark web, and experts have raised questions regarding their privacy policy
- Closed Source Code: The main code is not open for everybody to audit, so we are simply taking the company at their word in terms of privacy
8. Brave Browser
Brave is a browser based on Chromium that, by default, blocks ads and website tracking. This creates a faster and privacy-focused browsing experience without any configuration.
Similar to Firefox and Waterfox above, Brave is not a dedicated dark web browser. You will have to manually configure it to connect to the Tor network. Its strongest appeal is that it has strong privacy defaults, making it usable for daily use that can be expanded upon.
- Blocks annoying pop-ups by default: Ads and trackers are blocked by default, making for a fast and clean browsing experience from the get-go
- Modern and Fast: Using Chromium-based technology, it feels fast and responsive while still maintaining the privacy of users as a priority
- No Automatic Anonymity: To access the dark web properly, you still have to configure manual Tor Routing for anonymous browsing
- A Focus on crypto: Some users who just need pure privacy may find the in-built cryptocurrency wallet and the reward system distracting
9. Epic Privacy Browser
Epic is created with the Chromium source code, but all Google-specific tracking data code has been removed from it. Additionally, it has an always-on encrypted proxy, blocks ads and trackers, and does not save your history or cookies.
It is a good free web browser for surface web privacy. But just to be clear, similar to Brave and Opera, it does not directly access the Tor network. It acts like a shield for privacy, not a tool for anonymity.
- Always-On Privacy: Your proxy and anti-tracking settings will always be in effect and require no setup
- Truly No History: It will automatically wipe your data (cookies, history, etc.) anytime you close it
- Limited Scope: Its proxy does simple privacy but does not offer the full anonymity of the Tor project
- Chromium-Based: (Yes, it is based on Chromium.) Its foundation stays tied to the Google ecosystem, which is a deal breaker for some hardcore privacy advocates
10. Tails
Tails is a privacy-focused live operating system that you can boot from a USB stick. It is designed to be used without leaving a trace on your computer. It forces all internet connections to go through the Tor network. It also comes with several secure pre-installed software programs, including the Tor Browser.

If you need to use a computer and do not want to leave evidence behind (like a digital ghost), Tails is the best tool. Tails has it all for amnesiac anonymous computing. While it’s not a browser, it includes Tor Browser installed by default that provides anonymity for web browsing and enables users to access the dark web.
- Leaves No Track: The ultimate amnesic computing device. It leaves absolutely no evidence on the computer, thus a perfect tool to use on public machines.
- Everything is routed through Tor: The entire operating system is built to route its traffic through the anonymity network.
- Session Only: It cannot permanently save your work and settings on the USB stick easily. So, every time is a new session.
- Not meant for daily driving: It will serve you best when you boot from USB and use it for special sensitive tasks. It is not intended as your main operating system.
Quick Comparison: Best anonymous dark net browsers
| Browser | Primary Use | Based On | Anonymity Network | Key Strength |
|---|---|---|---|---|
| Tor Browser | Dark Web Access | Firefox | Tor | Ease of use & strong anonymity |
| I2P | Dark Web & Anonymity | Unique | I2P | Decentralization & resilience |
| Subgraph OS | Secure OS & Browsing | Hardened Linux | Tor (Integrated) | Application sandboxing & security |
| Whonix | Anonymous Workstation | Debian Linux | Tor (Forced) | IP leak protection & security |
| Firefox | Privacy Browsing | Firefox | Configurable | Customizability & familiarity |
| Waterfox | Privacy Browsing | Firefox | Configurable | Speed & legacy extension support |
| Opera | Mainstream w/ VPN | Chromium | Built-in VPN (Not Tor) | Convenient free VPN for clear web access |
| Brave Browser | Ad-Blocked Browsing | Chromium | Configurable | Strong default privacy settings |
| Epic Browser | Privacy Browsing | Chromium | Built-in Proxy | Removes Google tracking code |
| Tails | Amnesic Live OS | Debian Linux | Tor (Pre-installed, Forced) | Leaves no trace on the host computer |
How to access the dark web using the Tor browser?
Accessing your preferred part of the internet using a specific browser is straightforward. All you need is a browser that works with it. Since the Tor browser is the most-recommended and easiest one to install and use, we’ve based this quick guide on it. Below you will find the steps:
- Download Tor Browser: Go to the official Tor Project website (always verify the URL to avoid malicious copies) and download the correct version for your PC’s operating system (Windows, macOS, Linux). Tor is also available for Android.
- Install the application: Run the downloaded installer and follow the on-screen instructions as you would for any other computer application.
- Launch Tor Browser: Open the Tor Browser application from your desktop or applications folder. You will see a connection window appear.
- Connect to the Tor Network: Click “Connect” in the connection window that appeared. The browser will automatically establish a connection through the Tor network. The connection can take a few moments, so you need to be patient, especially when you’re connecting for the very first time.
- Verify your connection: Many skip this step. We recommend not skipping it. Check your new IP address and confirm that you are on the Tor network by visiting check.torproject.org.
- Access .onion sites you need: Now paste the direct .onion URLs you want to visit that you obtained from dedicated directories or sources (e.g., https://duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion/) into the address bar and press Enter.
What makes the Dark Web still relevant?

The value placed on privacy has increased. With the growing abilities of corporations to monitor and collect our data, the core principle upon which the dark web exists is now more relevant than ever.
The dark web is no longer for journalists and activists avoiding censorship alone; regular citizens now use it too. They use it to:
- Communicate privately to avoid being monitored.
- Access news sources that their government blocked.
- Conceal their financial and personal data so uninvited, untrusted third parties or strangers cannot see it.
Understanding and knowing how to safely access this part of the internet is an important digital skill for today’s era.
How to remain safe when using darknet browsers

The correct top dark web browser download isn’t enough when it comes to safely accessing the dark web. A few other things and safety practices must be put in place.
Follow these steps to protect yourself:
1. Use a reliable VPN
You only need the Tor browser to access the dark web. But simply using Tor leaves a traceable trail for your ISP; they can see that you’re using Tor. So, always connect through a reliable VPN before starting your chosen web browser for the dark web. This is the first step; you must not skip it.
A VPN like NordVPN provides an additional level of encryption and shields your use of Tor from your Internet Service Provider.
Why NordVPN?
Setting up NordVPN will ensure that it encrypts your connection, so your ISP cannot see that you are using Tor. It’s your necessary cloak of invisibility for the trip there.

Key features of NordVPN:
- Onion Over VPN Servers: Specialized servers that streamline your traffic untraceably and totally through the VPN, then into the Tor network.
- ISP Activity Masking: Encrypted connection conceals that you’re using Tor from your ISP.
- Double VPN Encryption: Your data is routed through two different VPN’s for an extra layer of security before being routed into Tor.
- Strict No-Logs Policy: An independently audited policy whereby your browsing activity and data will never be logged.
- Integrated Threat Protection: Blocks malicious sites and stops downloads of known malware infected files.
2. Disable scripts
In your browser settings (like the NoScript extension in Tor), you will want to disable JavaScript and other active scripts. That is because many security exploits rely on these scripts to run; if kept enabled, they can be exploited through security vulnerabilities like cross-site scripting (XSS) to track user activity or inject malicious code. By disabling, you reduce such attacks’ potential (especially on untrusted websites).
3. Never download files
Downloading anything online can be dangerous, let alone the hidden internet.
You should never download things from the dark web. Downloaded files could have malware in them that may be designed to de-anonymize you or infect your device. If you must download something from the dark web, only download files and run them using a completely isolated virtual machine.
4. Don’t trust anyone
Assume that everyone and every site is trying to take advantage of you. Avoid giving up real information, don’t log into your personal accounts, and don’t engage in conversations that could identify you.
5. Block your webcam
This is a simple, physical step. A piece of tape over your webcam essentially prevents any possible remote activation by malware.
6. Verify .onion URLs
Use .onion URLs from reputable directories only. Or the ones you know are safe. Don’t be fooled into going to a malicious clone site that is designed to extract your information.
Conclusion
When it comes to accessing the dark web (and safely), selecting a good dark web browser is critical. Tor Browser is the #1 in our list above for all the good reasons. We recommend that you use only the Tor browser to access the deep, dark web, if you must. If you fancy exploration, we’ve listed nine other options as well.
But your tools are only half the story. To have the safest experience every time, always pair it with a robust VPN like NordVPN. This powerful combo keeps your journey secure and private. Stay curious out there, but always put your safety first. Happy and safe browsing!
FAQs
No. Using a dark web-specific browser such as Tor or I2P itself is legal in virtually all countries. These are privacy tools by nature. But using these tools for illegal purposes constitutes a criminal act either way. Criminal acts conducted on the dark web are still unlawful.
To provide anonymity, Tor is generally quite effective, but not completely foolproof. If the person tracking you is very advanced and has unlimited resources, they could conceivably de-anonymize you when you make certain mistakes, like downloading files or enabling scripts.
The safest and best dark web browsing tool for Android users is the official Tor Browser APK from the Tor Project site. Not just Tor alone, there are official sites for downloading every similar web browser APK. Always ensure you get your Tor browser or any other software directly from verified sources only, not from third-party sites.
It is strongly encouraged. Using a VPN with Tor (commonly referred to as “Tor over VPN” or Onion over VPN”) adds an essential layer of protection. It hides the use of Tor from your ISP and protects you if your Tor connection is compromised in some way.
The deep web is every part of the internet that is not indexed by search engines, like private messages from your social media or your online banking portal. The dark web is a small section of the deep web that is hidden on purpose, requiring specific software to access.
