Cloud computing powers everything from file storage and business apps to global infrastructure, but moving data and systems online also introduces new security risks. That’s where cloud security comes in.
Cloud security refers to the policies, technologies, and controls designed to protect cloud-based data, applications, and infrastructure from unauthorized access, breaches, and cyber threats. It covers everything from encryption and identity management to threat detection and compliance.
Whether you’re a business running workloads on AWS, Azure, or Google Cloud (or an individual storing personal data online), understanding cloud security is essential. This guide explains what cloud security is, how it works, and why it’s critical in today’s cloud-first world.
What is cloud security?
Cloud security is your complete set of policies, procedures, and tech tools designed to protect your data, apps, and other vital assets from threats and vulnerabilities in the cloud. To put it simply, cloud security is a digital castle to store your digital assets.
While cloud providers give an extensive security apparatus, security is usually a shared responsibility. Understanding this shared responsibility model is one of the most vital components of cloud security.
Cloud security is not just a tool; it is a total solution that contains areas that range from cloud network security, data encryption, identity management, and disaster recovery, amongst others.
In today’s world, cloud security is part of the new ecosystem of cybersecurity. With regard to protection and security controls, cybersecurity and cloud security have the same approach when it comes to applying them. (Go through our hacking statistics to explore recent cybersecurity stats and facts to note today.)
This is because cloud security tries to achieve the same level of protection for the data in the cloud as that of an on-premises data center.
How does cloud security work?
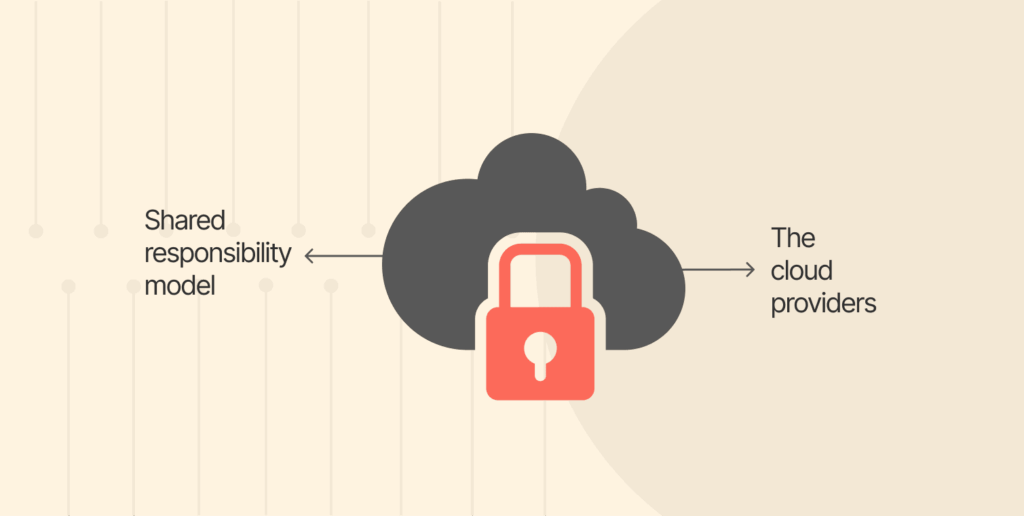
Cloud security utilizes a layered defense strategy, similar to layers in an onion. This defense system involves some combination of technologies and techniques to help protect against many types of threat vectors or entry points.
- Shared responsibility model: When discussing the shared responsibility model, this is a critical aspect of cloud security.
- The cloud providers: Google Cloud, AWS, or Azure, have a shared responsibility in securing the cloud (the hardware, software, and physical facilities), while the user has a responsibility to secure the cloud (their Information, applications, operating systems, and network configurations). The extent of shared responsibility varies by the service model: IaaS (Infrastructure as a Service), PaaS (Platform as a Service), and SaaS (Software as a Service).
What do you need to secure in the cloud?
Securing your assets in the cloud cannot simply be a copy-and-paste approach because it involves many different assets with varying protection capabilities:
- Cloud networks: Virtual private cloud (VPC) creates a secure, private network within a public cloud. The process needs a strong virtual firewall to secure the VPC and provide inspection and filtering of the network traffic while keeping the critical foundation connection active. You can’t use your old on-premises firewalls in the cloud. That’s because cloud environments spin up and down constantly, so your security needs to adapt in real time.
- Compute instances (Virtual Machines): Compute instances are the assets performing the work in the cloud. These assets must be secured against nasty malware and vulnerabilities. Because one can spin up and down cloud instances at any moment, your IT team must always see them and secure them under a strict policy.
- Containers: They are much like shipping containers for apps that require special security both before they start operating and while doing so. This entails scanning container images for vulnerabilities and adding security layers to any container orchestration, like Kubernetes.
- Cloud applications: Security is important at the application level, whether there are virtual machines or they exist in a serverless environment. This includes securing their configurations, implementing strong authentication, and monitoring traffic for malicious behavior. IT administrators must have a central view for detecting and responding to threats that emerge.
How cloud security differs from traditional on-premise security
While the goal of security is the same—protecting data, the methodology of security is different in the cloud than on a traditional on-premise setup. The main difference is responsibility and the mechanisms of the tools used to deliver it.
| Feature | Cloud security | Traditional on-premise security |
|---|---|---|
| Responsibility | Shared responsibility model | The customer is solely responsible for everything |
| Infrastructure | Managed by a cloud provider | Managed by the customer |
| Tools and controls | Dynamic, via APIs, scalable | Static, via hardware, manual |
| Scalability | Elastic on-demand | Bound by physical hardware |
| Location | Distributed across multiple data centers | Centralized on company premises |
In a traditional setup, the company secures everything – the physical servers, the applications, the data. Now and in the cloud, the burden is shared, which vastly simplifies security and reduces overhead costs.
Cloud security tools are different, too. They rely on software-defined protection that you can scale up or down instantly to match your needs.
8 key cloud security solution categories

A comprehensive security strategy requires a suite of tools and services. Here are eight critical categories of cloud security tools:
- Cloud Access Security Broker (CASB): Your cloud sees a CASB as a bouncer. It sits between users and cloud services to apply security policies and provide data encryption and malware protection.
- Cloud Security Posture Management (CSPM): CSPM tools can be described as a continuous security auditor, scanning your configurations constantly to detect and remediate insecure configurations that may lead to a breach.
- Cloud Workload Protection Platforms (CWPP): Think of CWPP as bodyguards for your workloads. They apply consistent security policies across your VMs, containers, and server-less functions. For many users, this protection starts with a robust cloud antivirus solution scanning for malware at the workload level.
- Cloud Compliance: These solutions provide a broader view of your cloud environment from 50,000 ft. up, ensuring compliance with regulatory standards and requirements.
- Security Incident and Event Management (SIEM): A SIEM is the central security operation. It ingests and interprets data from multiple sources to help you suspend, inspect, and remediate cyber-attacks.
- eXtended Detection and Response (XDR): eXtended detection and response is the next evolution in security. It ingests data from multiple sources, automating the writing of attack timelines, so security teams can inspect incidents at superhuman speeds.
- Secure Access Service Edge (SASE): This is a network architecture that features a mix of functions related to network and security, designed to guarantee secure remote access to systems and cloud providers via a single, cloud-delivered platform.
- Security Service Edge (SSE): SSE narrows its focus to security defenses designed to secure user access to web, cloud, and private applications; consolidating functions so the user experience is seamless while reducing complexity in security functions.
Top strategies for protecting your data in the cloud
The best software will only get you halfway there; knowing how to use it is the other half:
- Create a more secure remote work environment: Although remote work is here to stay, creating vulnerabilities while your employees access data on unsecured public networks open to a virus (i.e., over open Wi-Fi to their personal devices) if they click on the wrong links. A solid cloud security system is essential to safeguard data.
- Use a safe data storage strategy: Use your cloud environment for data backup, and also ensure that you have appropriate governance around data retention and compliance (at minimum), even if you don’t work in sensitive industries (such as healthcare and finance). (Choosing a reputable provider is the first step in a safe storage strategy. We’ve reviewed the top 20 best free cloud storage services to help you make an informed choice.)
- Encrypt data: Encrypting data scrambles your data to prevent anyone without the encryption key from reading it. You should encrypt stored data and data that is moving (in transit) from one system to another.
- Enforce strong access controls: Consider the use of multi-factor authentication (MFA), so you have more than just a password. You can use the “principle of least privilege” here; only give users as much access as they need to do their jobs.
- Conduct regular audits: Cloud environments are not meant to be “set it and forget it.” In fact, you need to regularly audit your cloud environment for misconfigurations or any other vulnerabilities. Good security practice uses a living document, not “set it and forget it” documents.
What are the common types of cloud security services?
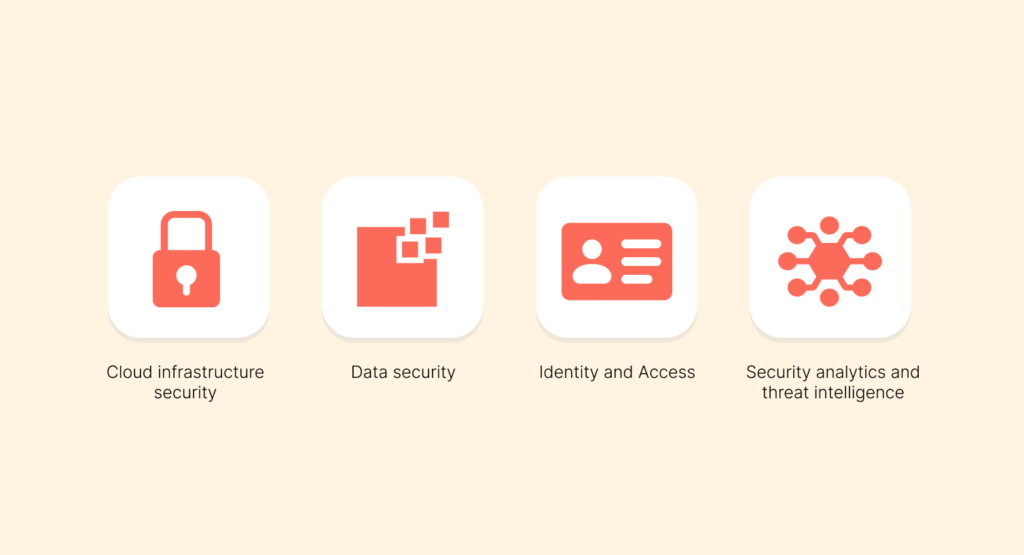
There are several types of cloud security services that can be put into a number of significant areas that cover more aspects of a cloud environment:
- Cloud infrastructure security: This includes the security of the primary infrastructure of the cloud provider. It can include secure firewalls, intrusion detection systems, vulnerability management, and other information security requirements to secure the servers, networks, and data centers where cloud resources exist.
- Data security: This emphasizes the protection of data, including data at rest (stored) as well as data in transit (data moving between systems). It also uses Data Loss Prevention (DLP) to stop sensitive information from leaving your network.
- Identity and Access Management (IAM): The IAM service is one of the primary foundational services that is put into place in a secure cloud environment. It focuses on access controls, ensuring that only authorized users and/or applications can gain access to specific resources. This service manages digital identities, authenticates users, and controls what they’re allowed to do.
- Security analytics and threat intelligence: It uses machine learning and artificial intelligence to process large amounts of data to be able to detect maliciousness, security threats, and to strategically respond in real-time to incidents of harm.
Risks and challenges in cloud security
Every security model has its flaws. The first step in overcoming cloud security challenges is to know what they are:
- Misconfiguration: One of the biggest risks of cloud security is human error. When you misconfigure a cloud service, there are always vulnerabilities that an attacker can exploit. Mistakes like storing sensitive data under the security of a public account can lead to sensitive data being available to anyone online.
- Insufficient identity and access management: When not properly managed, identity management can lead to overpowered users. When attackers compromise accounts, they can gain access to critical information and systems.
- Insecure APIs and interfaces: Many available cloud platforms use APIs to access the service. These APIs present needed security; otherwise, they can be a vulnerable entry point for attackers.
- Data breaches: Even with forms of security in place, accessing sensitive information can still occur. A breach incident could arise from a compromised password, phishing, or poor data management. (We have covered the biggest data breaches in recent history.)
- Shadow IT: Shadow IT provides security vulnerabilities that aren’t visible to IT. When employees leverage unapproved cloud software applications to do their jobs, this alone is a security risk.
Benefits of cloud security
There is a multitude of benefits to a well-defined cloud security strategy. While this security may feel daunting, it is more than a defensive mechanism and can effectively be a business enabler:
- Cost savings: You can take advantage of the economies of scale that the cloud provider has and the reduced user cost associated with maintaining hardware and security staff.
- Scalability and flexibility: Cloud security is flexible and can scale up or down as your needs dictate. The elasticity of cloud security provides you with the ability to protect your data without having to cater to excess capacity. This is a significant point for businesses that have needs that vary.
- Centralized security: Cloud security allows you to manage all aspects of security – policies, threat detection, and alerts – from one location with a single dashboard. In essence, it allows you to manage everything from a “single pane of glass.”
- Reduced compliance burden: Cloud providers give you access to built-in controls and certification to help you have systems that meet regulatory specifications. This reduces the desirable number of opportunities for audits and assessments of compliance.
- Reduced threat environment: Cloud providers spend billions on cloud security research and security technology development. In other words, the cloud provider invests in research and development that typically would be impossible for you to create on your own.
FAQs
Cloud Security in cybersecurity is a domain that focuses on the protection of cloud computing environments. The measures taken are the same as traditional cybersecurity principles regarding data protection, identity management, access, and threat detection, but they are contextually centered around the cloud computing vendor’s responsibilities within the unique shared-responsibility model of cloud-based platforms. Cloud security is also inclusive of the policies and technologies to secure the infrastructure (platforms), data, and other applications stored in the cloud.
Cloud security examples are numerous and involve practices as well as solutions. One illustration of cloud security involves organizations implementing Identity and Access Management (IAM) systems to restrict access to certain resources in the cloud, ensuring that only authorized users gain entry.
Consider the intervention of a Cloud Access Security Broker (CASB), a role designed to enforce an organization’s security policies. Data encryption is also an example of cloud security, for both data at rest and data in transit, which is probably the most basic enactment of cloud security precautions.
While this article doesn’t list specific cloud cybersecurity salaries, our research confirms they’re generally higher than other cybersecurity roles (thanks to high demand for these specialized skills).
There isn’t a universal amount as it varies depending on experience, certifications, location, and job title, such as cloud security engineer or cloud security architect.
Some of the biggest cloud security challenges entail dealing with the shared responsibility model, misconfigurations, and, in general, a lack of visibility into cloud environments. There are other human error challenges, as well as using unauthorized (Shady IT or Shadow IT) applications. The constantly evolving threat landscape and remuneration/recruiting specialist talent are also major hurdles.

