You all know about fishing, right? You go out with a fishing tackle, choose bait, throw it in the water, and pull back when you catch a fish. But, ever wondered if you could be fished online via phishing emails?
It isn’t fishing, but rather phishing, that targets you on the internet. For this, a phishing email comes as bait to trap you.
Phishing is the digital variant of fishing and is the most common and the most straightforward internet attack. It is the most common way hackers use to steal user information. It is a venerable and ever-evolving sophisticated cyber attack.
Everyone connected to the internet, from organizations to individual users, is exposed to this danger. At the same time, most users have fallen prey to phishing attacks at least once.
Despite being an old strategy, phishing attacks remain the most successful cyberattacks because of the diversity of methods that criminals employ to trick users. Yet, the critical vector through which phishing attacks execute today remains emails.
For instance, you can receive an email from a fake lawyer claiming you are kin to a millionaire who recently passed away. To inherit the fortune left behind, you must meet the set requirements, such as sharing sensitive information.
Phishing comes in different forms, though fraudulent emails are the most common. Getting insights on phishing and how to prevent it is vital to avoid being a potential target for these cybercriminal phishes.
Hence, in this article, we’ll explain phishing emails meaning in detail and how to identify them. We’ll also guide you on things you can do to protect yourself if fallen victim to an email phishing attack.
What is phishing?

Getting the correct definition of phishing can confuse some people, as several explanations exist. However, each description you find out there carries the meaning of fraud.
The Oxford language dictionary defines phishing as fraudulent activities that involve people receiving emails or messages purporting to be from recognized companies, spurring them to share personal information.
Once your information, such as a bank or credit card details, gets into the hands of these hackers, you are likely to lose personal funds. Other attackers may target corporate data to sabotage businesses or lead to financial losses. Though cyberattacks differ, phishing uses a technique that provokes recipients to share personal or business-critical data.
Typically, phishing is widely used by cybercriminals as a digital tool to entice targeted people to provide data such as passwords and credit card numbers.
These phishing attacks are often conducted through emails and social networking sites. Here, cybercriminals disguise themselves as trusted sources or companies tricking victims into clicking malicious links or downloading particular attachments. Here is a breakdown of data types targeted by hackers through phishing;
- Personal data: Email address, name, and social security number
- Credit card information: PIN, password, CC number, and username
- Business information: Sales forecasts, patents, and product insights
- Banking information: Account number, online credentials, and PIN
- Medical information: Insurance claims
Phishing has existed since the mid-1990s, and these malicious attacks have become efficient and more advanced nowadays. Besides, a single hacker can quickly target a more extensive network or groups worldwide.
The history of phishing
Like how fishers bait fish through fishing, hackers set a trap for targeted recipients through phishing.
“Fishing” and “phishing” are similar terms with nearly identical meanings. So, you may wonder, why not refer to these forms of cybercrime as “phishing?”
Generally, the term “phishing” emerged in the 1990s to denote cybercriminals’ methods of stealing personal information.
Since the first hack occurred, hackers referred to themselves as “phreaks” and used “phreaking” techniques to breach telecom systems. For this reason, this is where the name “phishing” came, and it is the title we use to refer to these individuals today.
A quick glance at the phishing timeline
The first phishing event occurred in the 1990s, when AOL, one of the leading internet service providers, fell victim to hackers. Here is a brief Phishing timeline;
- 1990: AOL was the first company to experience this form of hack. Hackers introduced a software community on AOL and traded pirated tools. Then, they began stealing AOL users’ usernames and passwords. Hackers later generated credit card information from stolen data through their algorithm. Fake credit cards were used to create AOL accounts and spam users.
- 1995: AOL established corrective measures against fake accounts and algorithms. Hackers then turned to spoof emails, and this is where phishing started. Hackers purported to be AOL and began sending fake emails to users. Because it was a new thing then, most users fell into the trap readily. Hackers used duplicate emails similar to those sent by AOL officials at that time.
- 2003: Cybercriminals focused on this industry in the wake of digital currency. They used similar impersonation ploys and successfully tricked the then-E-Gold users. Most of them shared their information and ended up getting their funds stolen. The online payment company got charged with money laundering and forced to stop its activities. Phishing gained popularity leading scammers to create fake domains resembling genuine entities and convincing users to share personal data.
- 2004: With this new form of scamming gaining popularity, cybercriminals developed new means of phishing. Established organizations, such as global banking websites, were targeted in the year.
- In 2004-2005 the world began feeling the impact of phishing. About $929 million was lost through phishing in the U.S. alone from different users. Countless countermeasures and awareness messages were introduced with the motive of preventing phishing. However, phishing cases continued for individuals and organizations because they had become more advanced while scammers invented effective ways to scam their targets.
- 2019 saw nearly 88% of businesses globally experiencing at least one form of phishing.
What is a phishing email?
A phishing email is simply an email reaching you from cyber criminals, hoping you will get phished.
It means the criminals try to collect information from and about you by sending fake emails. The target information may range from login credentials to sensitive personal and bank data.
Sometimes, the emails may also deliver malware on your devices, then steal data from them.
These emails are never legit. But they always impersonate other legit emails that you frequently receive. For example, these emails may appear as an email from your bank, a response to your job application, or an alert from some social media service like Facebook.
Also, a phishing electronic message (the email) often appears as a message from your company’s CEO or colleague. This type of phishing attack successfully conducts large-scale attacks on different organizations.
Ironically, some fake emails also appear as notices from law enforcement agencies or legal notices to stress the target users psychologically. Besides, users keep getting targeted on eCommerce platforms, as in PayPal scams and Amazon phishing emails.
Often, it becomes challenging to distinguish these spoofy emails from the legit ones exclusively. Hence, users frequently open such emails, follow what’s asked, and inadvertently share their data with criminal hackers.
In other words, you end up being phished!
How phishing emails work
Phishing attacks don’t usually happen randomly. Instead, the hackers running such campaigns have a clear target in mind before moving on. Even if they aren’t clear about the victim user, they have a clear intention about the information they want to steal.
With this in view, the hackers craft their phishing campaign, which often includes carefully designed email messages. Then, they register the relevant domains to back their emails, design phishing web pages, and arrange data storage (if needed). Lastly, they have to decide about the future of the collected data, like selling it to third parties on the dark web, exploiting it themselves, or using it for other malicious purposes.
For instance, if the hackers want to steal the financial details of many users, they’ll go for impersonating banks. For this, they might register typosquatting (similar or misspelled) domains for a renowned bank, design web pages mimicking the target bank’s website design, and create forms where the victims would enter data.
Then, they’ll create email messages inducing a sense of urgency for the recipients to take action, like informing them of a stopped transaction, bank account closure, credit card expiry, etc. This urgency would likely compel the recipient to click on the given phishing link or proceed according to the provided instructions. That’s how hackers succeed in achieving their goals with phishing emails.
Types of phishing emails
Depending upon the target victim and how an email gets sent, phishing messages get classified into the following:
1. Spearphishing
It is the most common type of phishing attack conducted by most attackers. Spearphishing is almost always aimed at individual users or users of target organizations.
Unlike conventional emails that arrive in your inbox aimlessly, spearphishing emails bear a particular design to trap the target.
These emails won’t mention your name (in most cases), but they arrive in a manner in which you frequently receive emails.
For example, the emails may arrive as a notification from one of the social media services you use, like Facebook.
These emails may even appear legit, as the attackers would also do a little search about you before sending a phishing email. So, you may receive a Facebook notification regarding a photo your friend just uploaded, which, in fact, would be nothing but a phishing email.
This kind of precision of fake emails is also possible when the attackers aim at your organization while preying on you. For example, you may receive emails that would appear from your boss or a colleague.
The more precise a spearphishing email is, the more likely you will click on it and follow what’s asked.
Spearphishing may not look dangerous. However, this harmless strategy has resulted in high-profile state-backed attacks and other cyberespionage activities.
2. BEC (Business Email Compromise)
If you work in a big organization, you and your firm are prone to BEC phishing.
What is BEC?
This type of phishing email also resembles spearphishing attacks. But they are more specific to the corporate sector.
As the term implies, this attack works by compromising business emails. FBI explains that the attackers impersonate anyone you trust, like your office colleague, your boss, or a vendor your company deals with as a routine. Since the sender appears known and legit, you trust the emails received at your end.
The attackers attempt to trick others into making huge transactions through these emails. For instance, urgently asking for overdue payments or buying gift cards and promptly sharing the serial numbers with your boss.
This sense of urgency makes it difficult for the victim to look for details or verify the emails. Unfortunately, that’s the reason these attacks remain very successful for cybercriminals.
3. Whaling
Whaling is just another phishing attack with a corporate target. These attacks are particular, and the attackers aim at high-profile targets.
In other words, the attackers ensure that the target victim is capable enough to satisfy their demands. So, they phish whales instead of small fishes.
Precisely, whaling aims at high-profile people, such as a firm’s board members or senior executives. Here, the attackers pose as a junior employee who shares a sensitive customer complaint or a colleague discussing sensitive matters like a subpoena.
Given the email’s business nature, the victim will likely trust the sender and do as asked.
These attacks often have purposes other than financial gains.
For instance, the attackers may implant malware into the system once the target user clicks on the phishing link. Eventually, the attackers can gain a hold of the entire business network. They may limit the spread of infection to the particular device only and steal sensitive company information.
4. Clone phishing
Clone phishing is a little different from conventional phishing emails.
While those emails reach you like a new email, clone phishing relies on modifying your current email threads.
In clone phishing, the attackers impersonate the conversation and context of a previously delivered and legitimate email. The phishing email, however, includes some links or attachments, or both, that are malicious.
The attackers often spoof the sender’s email address as well. Hence, the email looks legit and continues the previous conversation.
For these phishing messages, the attackers often target previously hacked entities, either the sender or the recipient, to obtain previous valid emails.
How to identify phishing emails?
It is an essential thing every privacy-savvy internet user should learn.
Identifying these spoof emails can be a chore, mainly if you believe you can’t be a target of them.
So, first, make it clear that you, as an internet user, are equally vulnerable to phishing attacks as the CEO of a big firm.
Likewise, you’re as vulnerable to phishing attacks as any billionaire.
Whether you’re a student, an employee, a senior executive, a business owner, or merely an at-home but avid internet user with a much-used email address, phishing emails will always reach you.
It’s because criminal hackers aim at moneymaking with phishing and at, spying on your activities, and stealing your data.
So, you were, are, and will always be vulnerable to phishing messages online.
Clear? Great.
Now that you know you’re vulnerable — don’t worry. Here we elaborate on how to spot phishing emails.
1. Check the sender’s email address
The malicious hackers know you will likely go through the sender’s name before opening an email. That’s why they spoof names and, frequently, spoof email addresses too. It’s because they want you to believe those fake emails as legit.
So, the first thing to check before opening an email is the sender’s email address.
Usually, a phishing email address never spoofs the first part of the address. (Mocking the second part after the ‘@’ is seldom possible. This part is the domain name officially representing a service.)
So, if you receive an email with the sender name “Bank of America,” check the email address. Anything like “bankofamerica@ocp.jp” or any other fluff after the “@” in the email address is fake.
2. Check the subject line
Today, it’s unlikely for most users to communicate with friends or family via email. Instead, most email communication is usually done with business contacts, or for other official and semi-official purposes, like communicating with payment facilities or e-commerce sites.
So, if you receive emails with subject lines “Hi…,” “Hey mate…,” “Please open to check your gift,” or any other weird thing, don’t open. Though these subject lines tickle your curiosity, remember, “curiosity killed the cat.”
Yet, these aren’t the only subject lines to be wary of. The subject lines might be more evident if the attackers send phishing emails impersonating some official context.
It’s possible that the email subject line would read “Pending invoice payment” and come from a known vendor. But remember that such emails, when official, never come with vague subject lines. So, for example, if you had an outstanding payment at your end, the subject line would have a reference number or a known identification mark.
If there is some random invoice number in the subject line, double-check the sender’s email address for legitimacy before opening the email.
3. Check the salutation
You can open the message if the subject line and email address look okay.
But don’t trust it right away. Check the salutation style of the message.
Anything generic, such as “Dear Concerned,” “Dear Customer,” or “Dear Friend,” is likely, not legit unless your email is that of customer support. Random customers might address you that way since they don’t know you personally.
However, your kith and kin, business acquaintances, and colleagues don’t need to address you generically.
Even if you are just a random service customer, that company would have a good record of your name. Hence, you will undoubtedly receive emails with your name clearly mentioned.
(Even in the case of bulk mailing, the support teams use features like ‘mail merge’ to send messages with a personalized salutation.)
4. Assess the email language
Besides salutation, email content is also essential.
You may come across a phishing email in a personalized style. The hackers would perhaps have your username and email address, thanks to the frequent data breaches that various big and small companies face.
So, if the salutation looks okay, move on, and assess the content.
For instance, if you see an email from your boss asking for gift cards, wait and recall whether your company was planning anything like that.
Had your firm distributed gift cards among the employees?
When was the last time it happened?
What was the worth of those gift cards?
Is anything in the pipeline for the current year as well?
And above all, ask yourself. Has your boss ever made such urgent requests before?
Your answer would likely be no if not all, then at least to the last question.
And, there, you spot a phishing scam!
Likewise, you may also notice phishing emails with threatening contexts. For example, things like “unauthorized login detected…” or “your account will be deleted” are seldom genuine.
These emails attempt to intimidate you with a sense of emergency or urgency so that you take quick action without thinking much.
If in doubt, it’s better to reach out to the respective service the email sender impersonates via other means of communication.
For example, if you get an urgent alert regarding unauthorized activity on your Facebook account, log in to your account by manually typing the URL in a new browser window. Then, sign in to your account to review the activity. Or, check your account status via the app on your mobile phone.
Similarly, if the urgent email poses as a message from your bank, contact your bank via phone or means other than email to verify the message’s legitimacy.
5. Review the links and hyperlinks
Phishing emails usually include a link to the phishing web page. This link is either embedded as a hyperlink on the message or separately mentioned as a shortened URL.
Sometimes, you can even see legit links mentioned in the email, but hovering your mouse on the link would let you see the embedded link that would likely be different from the one visible.
These signs hint that the email is a phishing attack.
Phishing URLs are often not malicious themselves. Instead, they serve as bait. Clicking on such URLs often makes you land on phishing web pages.
In most cases, these phishing web pages impersonate the legit websites of the service the attackers spoof.
For example, if you receive a phishing email posing as an alert from Facebook, the corresponding phishing web page would mimic the Facebook website’s layout.
In most cases, the phishing website will likely impersonate the service’s login page. The attackers mainly execute phishing attacks to steal your account credentials. Believing the page is real, you will enter your email address and password and unknowingly compromise your account security.
If the phishing email poses as a message from your bank, the risk is even higher as the phishing web page will ask for your personal and financial data, including debit/credit card numbers.
Therefore, as a rule of thumb, if you have clicked on a phishing link and see that the web page asks for your information, beware! The link wouldn’t be genuine.
Again, for verification, you can always contact the respective service via other means.
6. Review the signature
Below the message, see how the email signature appears.
While notification alerts and emails often have no formal signature, the services tend to give unsubscribe links here. In addition, you will frequently see other details like the company’s office address, links to the privacy policy and terms of service, contact number, and disclaimer.
However, the criminal attackers behind phishing emails usually don’t try to include all such data. Even if they do, they will likely paste a snapshot of it with no clickable links.
But, if you find clickable links here, hover your mouse over them. You will undoubtedly identify the gibberish embedded behind it.
Also, such closing texts’ language would not appear legit, hinting at their vagueness.
Whereas, in the case of phishing email content impersonating formal communication, you may see standard signatures mentioning a company official’s name along with details like designation, address, email address, website link, and other stuff.
Since most services include this information in formal email communication, phishing emails also mimic them to trick users.
However, a closer look at the signature would let you identify the scam. For example, a bank official’s email signature would not mention a Gmail or Yahoo ID as the corresponding official address.
Also, if you see a seemingly legit email address in the signature, hover your mouse on it and see if the embedded address is the same as the one shown. An intelligent attacker may also hyperlink a legit email with a fake one.
7. Look for attachments
Sometimes, the emails may also include attachments, posing as invoices or essential letters. These attachments may also contain malicious links.
Frequently, such attachments also include malicious codes. Thus, opening such attachments would execute the malware on your system immediately without you knowing.
So, if you find any attachments in the emails, don’t open them unless you are sure about the sender.
8. Analyze what information is asked
As explained above, phishing web pages impersonate the website layout of legit services to bluff users. The primary goal of criminals behind phishing attacks is to steal your personal information.
This intended information may range from your account login credentials (email address and password) to your personally identifiable information (PII).
Your PII may include your full name, physical address, contact number, social security number, and financial data such as bank details, credit/debit card numbers, etc.
Depending upon the intention, the attackers design their phishing emails accordingly.
For example, if the phishing email and web page mimic Bank of America, the attackers would ask you for your PII data and financial information.
Whereas spoof emails exploiting Facebook, Apple, LinkedIn, or Microsoft Office, intend to steal your account credentials. It’s because once the attackers have your credentials, they can exploit your account however they want. They can even lock you out of your accounts and trick your connections by abusing your account.
If you receive official and legit emails, note that they never ask you to enter any information. For instance, if it’s about resetting your account password, Facebook won’t ask you to change these details immediately. Instead, it follows a lengthy procedure that includes sending verification codes to your phone number or a recovery email address.
Likewise, you may receive a phone call if there’s an issue with your bank or payment service. Or, even with emails, the service won’t ever ask you to enter necessary data on web pages.
Real-world phishing email examples
If you wonder what most phishing emails look like, here we list some basic scams the attackers execute this way. Thanks to the cybersecurity community that regularly identifies and discloses such scams to make people aware.
With these examples in mind, you can mostly protect yourself from falling victim to the latest phishing email scam.
Tech support scams
Tech support scams are the ones where the threat actors impersonate tech support firms (mostly from big firms like Amazon and Google etc.) to access your system. The scams begin from malicious ads and websites, as well as from phishing emails.
In these scams, the emails can either be harmless, merely alerting you of some problem in your system or redirecting you to the phishing web page. Or, the emails may include malicious code that freezes your system to trick you into connecting with the scam support.
For example, consider this LinkedIn phishing email campaign that leads to scam tech support.
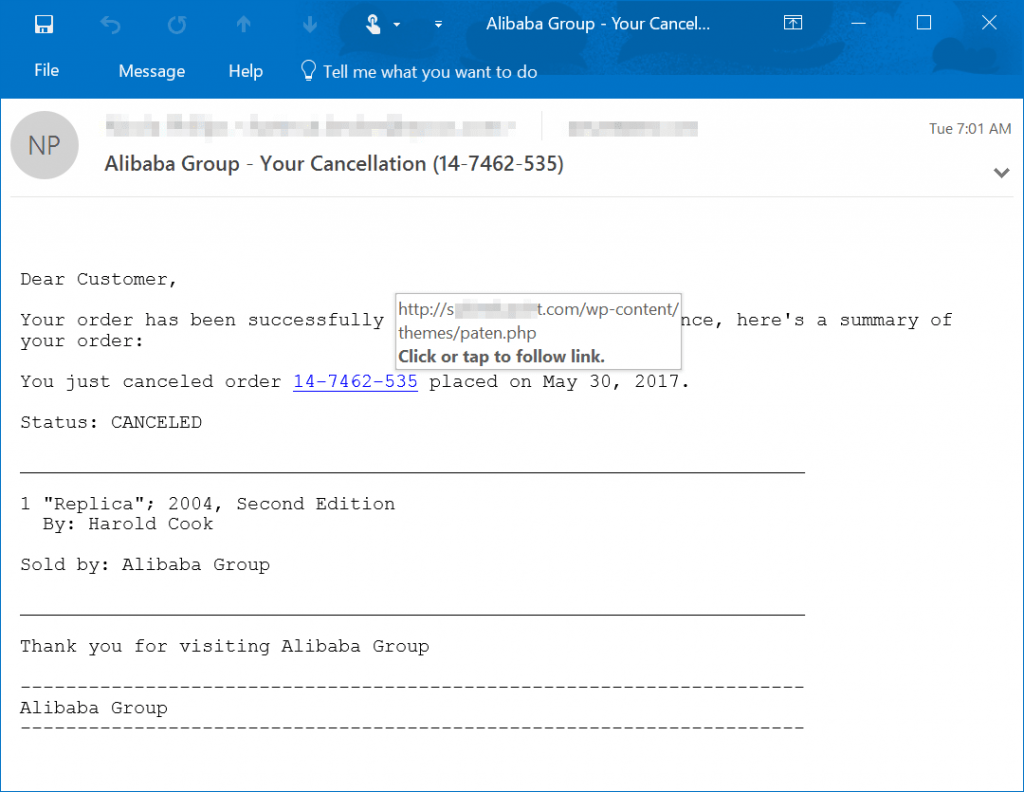
Suspicious login alerts
Social media users often are susceptible to the security of their accounts. Undoubtedly, Facebook, Instagram, and other social media sites remain on the hit list of criminal hackers.
Therefore, such users heavily rely on account login alerts received from these services via email or SMS to know when somebody attempts to breach their privacy.
That’s what the threat actors love to exploit.
The following email is an example of Instagram phishing, where the attackers send fake login alerts to the victims. Through this campaign, the attackers aimed at stealing users’ legit accounts’ login credentials.
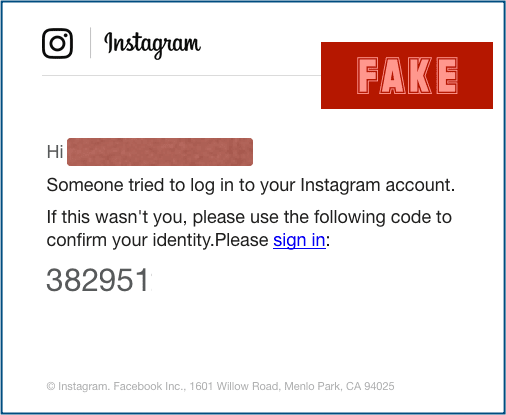
CEO fraud
Since turning down a request from your boss is almost impossible, hackers often target a firm’s employees with CEO fraud.
These are specific phishing email that impersonates your company CEO (or whoever is your boss) as the sender. The emails often ask the recipients to make urgent transactions on behalf of or for the boss.
Of course, loyal employees would be happy to address such personal requests to prove loyalty. However, little would they realize that they would face big trouble by responding to such emails.
Here is a classic example of a CEO fraud phishing email.
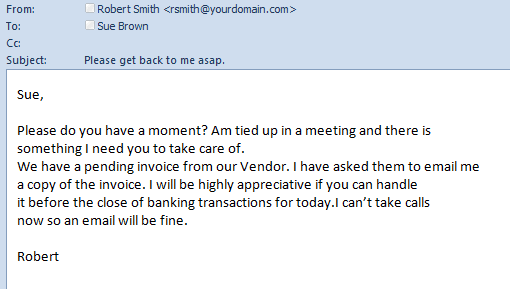
Account deactivation
These emails create a sense of panic by alerting users of account deactivation. It usually justifies this deactivation due to non-payment or license expiry, eventually panicking the end-users. Since the emails give the victims a short time to respond, they will likely click on the provided links and follow the instructions.
For instance, in the following example, the phishing email targets Microsoft Office 365 admins alerting them of license expiry. This one is a classic example of BEC scams:
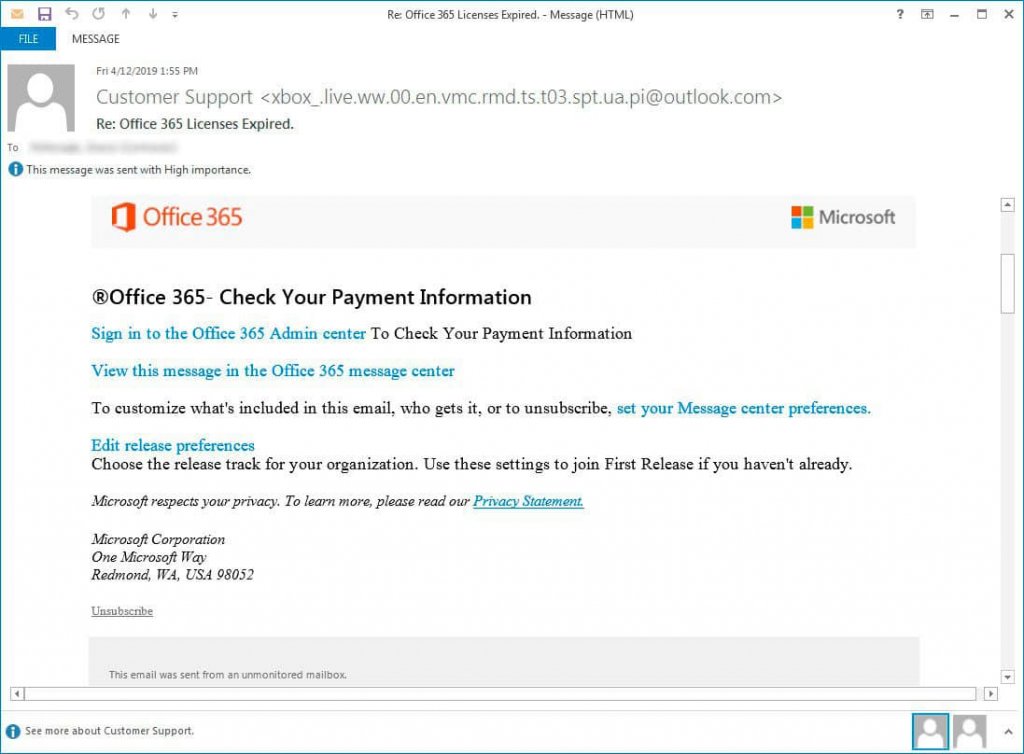
Payment card details
It is the most rapidly increasing phishing attack during the COVID-19 pandemic, as most buyers rely on online payments. The scammers are increasingly leveraging this opportunity to steal credit/debit card numbers. And, of course, what else could better suffice this purpose besides panicking you with a compromised card alert?
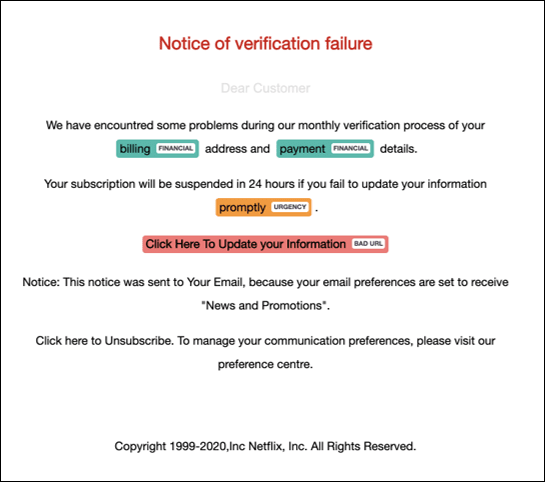
Take a look at this email as an example. The attackers collectively aim to steal Netflix account credentials and payment details.
Recent general phishing scams examples
Have you ever thought of losing your phone? It is unsettling, mainly when your information can be easily accessed.
Imagine if a hacker gains access to confidential information and uses it in fraudulent activities. It is an easy means to lose your mind because you have no idea where to find such an individual.
However, phishing scams have continued to increase, leading to critical information theft both individually and commercially. Several phishing events have recently occurred, and many people have been phished. Here are a few real-life phishing events to help you to understand better how these cybercriminals operate.
Coronavirus phishing scam
The global pandemic, COVID-19, came with countless uncertainties. It destroyed the economy and led to the loss of thousands of lives. Most people stayed home and avoided gatherings to conform to movement restrictions and social-distancing rules.
Unquestionably, everyone worldwide felt the pandemic’s impact in one way or another.
During these times, people encouraged and supported each other, especially those who had lost a family member or a friend. However, some corrupt individuals took this upon themselves to capitalize on this dreadful situation as an opportunity. Scammers used various techniques to ensure unwary people fell into their phishing scams.
Immediately after COVID-19 landed in the U.S., hackers used this opportunity to create different messages, evolving around the pandemic. For example, some sent fake text messages disguising themselves as the U.S. Department of Health and Human Services. This text accompanied various registration links claiming to be mandatory for COVID-19 testing. However, this was never the case.
The links contained malware that allows scammers to collect people’s personal information once they click on it. According to Google’s Threat Analysis Group, over 18 million COVID-related phishing emails and websites got blocked within this period. In other words, hackers wanted to use these desperate times to steal from unwary individuals through phishing.
Presidential Election phishing scams
If you were a voter, you would likely have received text messages regarding the 2020 Presidential Elections. Due to the pandemic, most practices occurred online, more so during registration. Scammers saw an opportunity and rushed to phish voters in the name of elections. Phishing seemed to take two forms; on-call registration and online phishing.
Hackers began sending voters spoofed emails and text messages, alleging their registration was incomplete. Hence, they must open the link and add personal information crucial for registration. Some messages also demanded social security numbers from the voters.
Some links received by voters were disguised as genuine and required voters to fill in their full details. In reality, these links redirect them to fake domains with forged forms, and hackers get hold of them once they fill in their information. That exposed innocent voters to cases of fraud, among other associated threats.
How to deal with phishing emails
If you have become a phishing attack victim, you may not fix it now if the incident happened in the past. But, if it has happened recently, here’s what you should do at the earliest. The same remains true if you ever suffer any phishing attack and subsequent data theft in the future as well.
Report the incident to LEA
Whether you become a phishing attack victim or marginally escape the threat by identifying it at the right time, report the matter to the Federal Trade Commission.
Reset your account login credentials
If you fear being tricked into entering your account credentials at a phishing web page, reset your password immediately. Also, if you have a bad habit of reusing passwords, change them across all the accounts.
Besides, keep an eye on your account for unauthorized login attempts, purchases, or other activities.
Inform your bank and card issuer
Inform the relevant authorities immediately if you have shared your payment card information or banking details on a phishing website. It will help them identify and block any unauthorized or suspicious transactions.
Ideally, you should close the compromised bank account and payment card immediately to keep your financial assets safe.
Reach out to credit bureaus
Thankfully, credit bureaus like Equifax, TransUnion, and others offer sufficient protection for identity theft. So, if you have likely suffered one, contact these services to protect your name identity from being misused for malicious purposes.
How to stop phishing emails
Given the ever-increasing and almost unstoppable extent of email spoofing, you might have fallen prey to a phishing attack. If not recently, then in the past. And, of course, you will remain vulnerable to such attacks.
Does that mean you can never prevent fake emails from preying on you? Certainly, no!
The key to stopping phishing emails from harming you is to be aware of them and make others aware.
After going through the phishing examples and the guide to identifying them, you will most certainly spot the next malicious email you receive. If you remember the key points and be a little observant, you will not become a victim of phishing attacks in the future.
However, if your family, colleagues, and company staff are ignorant, you will suffer the same impact indirectly. Therefore, once you learn what phishing emails look like and how to deal with them, spread the word to everyone you know.
Particularly, if you’re a senior executive at a firm or own a business, you must inevitably train your staff. Conduct different workshops and awareness programs to guide every employee about phishing emails. You can also test their skills through phishing simulation tools to see how they respond to spoof emails. It will help you evaluate the adeptness level of your employees.
SEE ALSO: How to Encrypt Emails.
Effective preventive measures against phishing

As you know how to spot phishing activity, another essential step is learning preventive measures. Such measures help you to avoid being a victim of scamming events experienced today. With that, here is how to prevent phishing on your device;
1. Be on the alert always
The spotting tricks are vital in helping you identify phishing scams before you fall victim. Learn thoroughly regarding these techniques, enabling you to sniff out scam emails, including calls and text messages.
We covered all that above in this article already. Being well-equipped with skills to spot phishing gives a better chance to avoid it effortlessly.
2. Install a reliable antivirus software
Sometimes, you may become carried away by fake emails and find yourself in the middle of getting phished.
But with perfect and reliable antivirus software, you can quickly protect yourself against the consequences of such spoofed emails. An antivirus helps block malware on your device, preventing hackers from accessing personal information.
3. Use an anti-phishing browser add-on
If you need additional preventive measures against phishing, an anti-phishing toolbar or browser extension comes in handy. These features help prevent hackers’ access to your device when browsing the internet and accessing malicious websites. Cloudphish is one such extension that is worth trying.
4. Turn to pop-up blockers
Most websites are full of pop-ups, which have become a nuisance and distracting attention when browsing. Hackers can use these pop-ups to create malicious pop-ups by either hacking official sites or on their websites.
The best way to curb such a problem is by using a pop-up blocker to avoid malware installation on your device.
5. Incorporate two-factor authentication
It is one of the most effective methods to avert cyber threats because 2-factor authentication requires double verification whenever you access sensitive information.
With 2FA (two-factor authentification) on, it can become nerve-wracking for hackers to hack your system successfully. Therefore, you must implement 2FA in your critical accounts, such as your bank, social, and email accounts.
6. Avoid clicking on links in an email or text message
Though it can be tempting, ignoring links sent to your email, especially from unknown addresses is crucial.
Double-check and verify the sender’s email address and name if you must. Besides, the email content can also shed light on the sender, mainly when it requests personal detail changes.
7. Be aware of events attracting scams
The world’s popular events are often a hotspot for attacks by cybercriminals, leading to phishing incidents.
A good example is the Presidential Elections mentioned above, where most scammers targeted to lure unwary voters into their traps. Intrinsically, identify these events and either avoid them or move cautiously because they use sophisticated tactics that are hard to ignore.
What to do if phished
If you suspect you have been phished because you never learned the signs or prevented it on time, here is what you need to do;
- Visit Identitytheft.Gov and follow the specified instructions to keep your details safe from theft.
- If you clicked and downloaded malware from a malicious link, upgrade your antivirus immediately and run the scan. In addition, you can update the system’s OS to patch any unknown vulnerabilities.
- Change your account details, more so passwords, from a different device immediately.
- Back up your data and conduct a system restore to a previous backup point.
Conclusion
Executing cyberattacks via phishing emails isn’t a new technique for threat actors. Yet, the thing that still makes this technique productive for bad actors is the people’s ignorance.
Despite being extensively studied by the cybersecurity community and anti-phishing strategies, spoof emails continue to increase their victims’ list because people aren’t aware of how phishing attacks work.
So, if you wish to protect yourself, your home, and your organization from common cyber-attacks, spread awareness about phishing emails.
We hope that this detailed guide will serve this purpose for you. Yet, feel free to reach out to us in case of any ambiguity.
Stay safe!
FAQs
Phishing is simply the modern cyber variant of the word fishing. Phishing refers to digital attempts to preying users online.
Not really. Phishing attacks can also happen via SMS, phone calls, ads, and messages on social media. In short, it can happen through any communication portal through which an adversary can manipulate you to share data or money.
Phishing attacks have a massive range of targets, seemingly impossible to list. Simply put, these attacks may target anyone from an individual user (such as a student, a home user, or a business professional) to an organization (small and large businesses, both) from any field. Some phishing attacks even come from sophisticated and organized APTs and crime groups.
Yes, phishing attacks aren’t confined to occurring via emails only. Instead, they can happen through virtually any means you use to communicate with others. For example, such attack techniques include Smishing (spam or unsolicited SMS messages) and Vishing (which occurs through audio files and voice calls).




