For years now, VPNs have been considered state-of-the-art when it comes to online security; however, recent reports reveal it’s not so. VPNs might in fact put your whole business at risk.
New warnings show these tools are now a top target for hackers ransomware gangs are exploiting VPN weaknesses to breach networks. Once inside, they can lock down entire systems and demand huge payments.
Why hackers love your company VPN
Virtual Private Networks (VPNs) have long been the go-to solution for remote security. They created a trusted tunnel into a company’s network. But that is far from the new reality we now face, because this good old model is now a weak point.
Cybercriminals see VPNs as a perfect front door. They provide direct access to everything inside. Attacks from ransomware groups like Qilin, INC, LockBit and BlackCat have been traced back to compromised VPNs. These groups are key drivers in a relentless criminal industry whose growth and evolving tactics are captured in the latest data on ransomware trends.
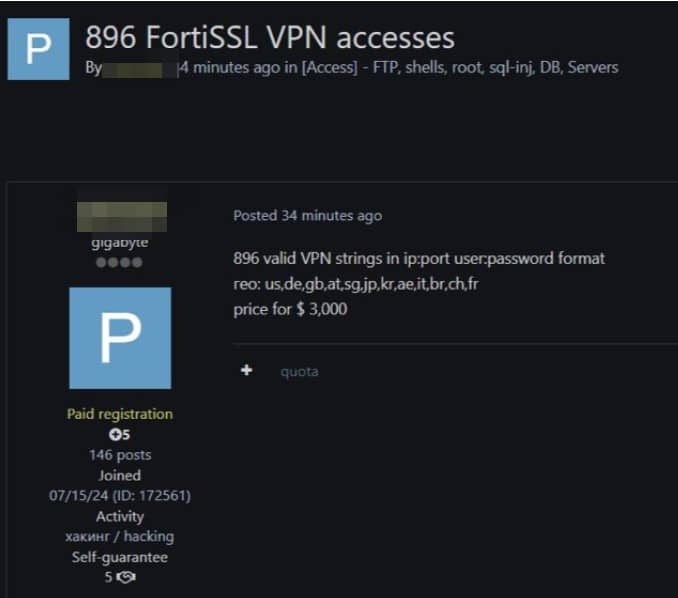
Attackers get in through several common holes. Use stolen login credentials bought on the dark web. They exploit unpatched flaws in the VPN software itself. They can even hijack an active user’s session.
The problem got much worse with the rise of hybrid work. Companies rushed to set up remote access for millions of employees. Security and proper network segmentation were often an afterthought. The result is a dangerous setup. If a hacker compromises one VPN password, they get the key they need to enter the system.
A move to “Zero Trust” Security
Since security experts have agreed that traditional VPN is not enough anymore, a new baseline for protecting your network has come up. They call it ZTNA (Zero Trust Network Access). It works in a simple way, it trusts no one.
It totally changes how VPNs work. Instead of access by network connection, it’s now all about verifying who the user is. People only get permission to reach the specific applications they need. The system blocks broader network access.
Continuous security checks protect your systems, giving hackers very little chance to get into a computer on your network. Even if they do manage to find a password, they wouldn’t be able to cause much damage.
Experts recommend immediate action by companies. The first step is to augment or replace old VPNs with Zero Trust controls. Another thing they recommend is using logins like security keys or passkeys that are resistant to phishing.
Fixing up VPN security weaknesses immediately is also very important. For individual users and smaller teams, layering security by using a reputable public DNS service can also provide an additional, often-overlooked line of defense against phishing and malicious sites. So is setting up systems to monitor for weird remote access behavior. The final piece is network segmentation. VPN users should never have access to everything on a corporate network.
The professionals in cybersecurity have given us a clear message ransomware actors have now improved on their tactics, and are going after outdated remote access systems. These threats are amplified by the rise of Malware-as-a-Service, which lowers the barrier for cybercriminals and can lead to incidents affecting tens of thousands of users at once. Relying on a traditional VPN alone in today’s threat landscape isn’t just old-fashioned.
It’s an active danger to any business. For individual users seeking privacy protection in their personal browsing, however, the choice of a secure, reputable, and modern VPN service is more critical than ever.