A Distributed Denial-of-Service (DDoS) attack is one of the simplest yet most disruptive cyberattacks, and it’s only getting more common. By overwhelming a website, server, or network with massive amounts of traffic, attackers can take services offline within seconds, costing businesses money, reputation, and security.
Even individuals, gamers, and small organizations are frequent targets. The good news? Understanding how DDoS attacks work makes them far easier to defend against.
This guide helps you understand what a DDoS attack actually is, how threat actors launch one, the warning signs to look out for, and the most effective ways to prevent or stop an attack.
What is a DDoS attack?

Distributed Denial of Service (DDoS) attempts to undermine the functionality or normal traffic inflow of a website, web server, or web application. The criminals use botnets to send heavy traffic to targets to overwhelm their resources, cause a malfunction, or go offline.
Think of a DDoS attack as a massive traffic Jam. You are trying to get to the office, home, or other places but are stuck in traffic and cannot go forward or back. In the DDoS scenario, heavy cyber traffic prevents web services from functioning.
That is because the cybercriminal sends heavy automated traffic to the web application, which would make your website go offline. A nonfunctional webpage can lead to a loss of revenue. Also, it would cause a lack of trust and reputational damage.
A lot of high-profile organizations have suffered a DDoS attack. Organizations such as PlayStation, Amazon, Google, GitHub, and Pinterest were all victims of these attacks in 2018. Therefore, you should not take the threat of a DDoS attack lightly.
Having the technical expertise to stop a DDoS attack quickly could significantly prevent your organization from going out of business. That is because a successful denial of service attack can be highly devastating. It could cause your business website to even disappear from the web. Of course, your customers would not be able to interact with you if your website is offline.
Types of DDoS attacks

There are many types of denial of service attacks. But here are the three most common ones:
- Protocol Attacks
- Volumetric attacks
- Layer 7 attack (Application layer)
1. Protocol attacks
A protocol DDoS attack would target your connection tables in the network areas to damage them. The attack would send continuous, malformed, slow pings and partial packets, thereby causing memory buffers to overload and crash the system.
DDoS protocol attacks can also be used to target firewalls, and this is why deploying a firewall alone would not stop a DDoS attack. Botnets are a standard technology used in protocol attacks.
Criminals use it to send packets to the target server to process/assemble. The target server then endlessly waits for a confirmation from the originating IP address, but it would never come. While waiting, the botnet would continue sending more packets without confirmation. This would eventually lead to resource overuse and downtime.
The SYN Flood is one of the most common types of protocol attacks, which makes use of a three-way handshake process for establishing connections (TCP /IP connections).
The SYN Flood attack can make a network wait to receive signals for a prolonged time, which can tie up network resources. Often, a hacker would use a protocol attack to disrupt networks until a more potent countermeasure gets deployed.
2. Volumetric attacks
Volumetric attacks are another common type of denial-of-service attack. In this case, the originating IP would overwhelm the network bandwidth by sending it millions of false data requests on every machine’s open port.
The network machine would check the incoming data request, which would make it unable to accept legitimate incoming traffic. The most common types of volumetric attacks are the ICMP (Internet Control Message Protocol) and the UDP (User Datagram Protocol) floods. UDP is a phenomenon where data gets transmitted without checking its integrity, while ICMP is a phenomenon where network devices communicate with each other.
Volumetric attacks use the Botnet to consume the bandwidth of the server, thereby causing it to go offline.
3. Application-layer attacks
Application Layer DDoS attack is carried out in the OSI network model. It is also the nearest to the users’ direct interaction with the system. The application layer attack is focused on the website, web application, or web server traffic.
It exploits avenues such as SMTP, DNS, HTTP, and HTTPS. They are tough to stop because they use a smaller number of machines to carry out an attack.
In some cases, it uses a single machine to carry out an attack, and the target server can be easily tricked into believing the attack is legitimate traffic. It sends traffic to a website or web server as if it’s an average human trying to access the service.
But it gradually increases the number of traffic and eventually overwhelms the bandwidth. Application layer attacks are the easiest form of denial of service attacks, and they are the most commonly used.
How to prevent DDoS attacks

Such attacks have considerably evolved over the past couple of years, and they show no signs of slowing down.
They keep growing in sophistication, frequency, and size. In 2020, hackers are using a hybrid and blended approach to DDoS attacks.
Without adequate proofing systems and detection, it is almost impossible to stop these attacks. When an attack is launched, your website will dramatically slow down and eventually crash.
DDoS simultaneously attacks applications and infrastructure data to increase the chances of success. To prevent or fight a DDoS attack, you need a well-drawn-out battle plan and a state-of-the-art prevention mechanism.
Every organization must implement an integrated anti-DDoS strategy that can counter the hybrid DDoS attack systems. You must also find reliable ways to protect all the infrastructures so that there would be no loopholes to exploit.
Here are the major strategies to prevent these attacks that you should adopt:
1. Understand the warning signs and catch them early by monitoring traffic
The primary symptoms of a DDoS attack include spotty connectivity on the intranet, network slowdown, and intermittent website slowdown. You need to be on the alert to know the warning signs. You must understand the history of your traffic through constant monitoring.
That way, you’ll know when traffic is high, low, normal, or extremely high. Knowing your traffic history would enable you to know what to expect at all times and help you identify a DDoS attack quickly.
But you should be aware that your traffic can significantly go high during specific seasons and top marketing campaign periods. It would be best if you also realized that authentic traffic from viral social media activities could cause a similar crashing effect to that of a DDoS attack.
No network is 100% perfect, but a prolonged or unusually bad performance could mean a DDoS attack. So, stay on the alert by continually monitoring your traffic and checking your network performance.
2. Get more bandwidth
Every organization should practice what is known as over-provisioning, which is the practice of going for a bandwidth that is higher than its capacity. Going for unlimited bandwidth is not the ultimate solution to a DDoS attack, but it can significantly reduce the impact of an attack.
You can also determine your server capacity and opt for a higher bandwidth that is higher than your average power. Overprovisioning would give you more time to tackle the attack, especially if the attack scale is not outrageous.
This excess bandwidth will protect your website, server, or application from the overloading effect.
3. Leverage the cloud
You can outsource your DDoS prevention plan to specialist cloud-based service providers. Cloud services typically have more bandwidth than a private network, which is a significant advantage.
These days the magnitude of DDoS attacks is enormous, and relying on your private infrastructure or on-premise network system would likely fail.
Secondly, cloud systems have a diffuse resource, and cloud applications can absorb much more malicious and harmful traffic than an on-premise system. Lastly, specialists and software engineers whose primary duty is monitoring the web and knowing the latest DDoS systems operate cloud-based services.
Using the right platform/environment for your applications and data can drastically improve your chances of mitigating DDoS attacks. All in all, you should opt for a hybrid environment such as the cloud to achieve the right balance between flexibility, scalability, and security. Some of the top cloud services that we can recommend include Microsoft Azure, Google Cloud, Amazon Web Services (AWS), and Alibaba Cloud.
4. Use a Content Distribution Network (CDN)
Organizations such as Facebook and Gmail understand the use of CDN. They have servers in various parts of the world to prevent downtime. If one server fails, they pull up data from the next server to avoid service shutdown.
These attacks cause a network to malfunction or completely go offline. So, storing your data and applications in various servers around the world can keep your systems running while you work on the affected server. You do not need to spend a fortune on CDN today, as a free provider like Cloudflare will do the job as well.
5. Maintain strong network architecture
Building and maintaining a secure network architecture is the first step in ensuring security. You should build a redundant network architecture if you are not using CND. A redundant on-premise network can enable you to switch to the next server if one gets attacked.
Spread out your resources and, when possible, locate your network servers in different geographical places. That will make the life of DDoS attackers extremely tough.
6. Consider DDoS-as-a-Service.
Using a DDoS as-a-service can significantly improve your flexibility, especially in environments that combine third-party resources, dedicated hosting services, and in-house network systems.
It would also ensure that your security infrastructure meets compliance requirements and the right security systems. It is more like training your system hard so that you know it can stand tall against such attacks. Moreover, this model is a tailor-made security architecture that needs high-level security against DDoS attacks. It is deployable for businesses of any size.
The takeaway here
All these strategies are okay, but early DDoS threat detection is one of the most efficient ways of preventing it. They come in various forms, and it is absolutely essential to recognize their multiple forms and put up a fight through a defensive mechanism.
Understand when there is an unusual lousy flood, understand your equipment capability, and identify application and network layer attacks. You should work with your data center, security vendor, or ISP to get the necessary defensive mechanism if you do not have adequate defensive measures in place, then.
You would be able to manage an attack if you have a proper threat detection system. Finally, you should set up rate limiting and always clear your server logs to free up resources.
I have become a victim of DDoS, what should I do?

Having the technical expertise to stop a DDoS attack and restore your network, website, and applications makes a big difference.
You could quickly go out of business when a DDoS attack occurs. But if you know what to do, you can keep your business running while you tackle it.
As noted earlier, the effects of a successful DDoS attack can be devastating, and your websites or applications can quickly go offline. Your customers, affiliates, and partners would not be able to reach you, and your apps will not function again.
Of course, the best play is to have done everything possible to prevent a DDoS attack in the first place. However, you can do the following if you are under an attack and your server(s) are offline:
1. Call your hosting provider
You need to call your hosting vendor if you do not own your servers as soon as you notice a DDoS attack. They have the technical expertise to look through and probably blackhole your traffic until the DDoS attack subsides.
Blackholing is a system whereby your Hosting platform drops both legitimate and illegitimate requests and traffic to avoid server crashes. After the traffic has reduced, your providers would reroute your traffic through a scrubber. This filters out the illegitimate traffic from the legitimate once the normal request is completely restored.
2. Get a specialist
You should consider hiring the services of a network specialist if you are experiencing a DDoS attack, especially when you do not have in-house technical expertise.
A specialist can study the attack and divert traffic to other (bigger) servers to handle the traffic inflows. They would also scrub the lousy requests on the target servers.
3. Wait it out
You can decide to wait out the DDoS attack if you do not have the technical expertise or the finances to hire a specialist. How long a DDoS attack lasts depends on the intention of the cybercriminal and your defense mechanism.
However, on average, a DDoS attack would last 2 to 3 days. So, you can wait it out if you feel you can accommodate the revenue loss for a few days. But you would need to put in measures to make sure such attacks don’t happen again.
4. Activate country blocking
You can deploy country-based blocking to minimize the effects of a DDoS attack. Nowadays, most botnets used in carrying out DDoS attacks are made up of thousands of infected computers, compromised CCTV, hacked websites, and other internet-connected gadgets.
Deploying a country-based blocking can significantly reduce the thousands of bots that are spamming your network.
It does not mean that country-based blocking completely restores your system because you might also be receiving illegal traffic from your country. But illegal traffic from other regions would be blocked, which can significantly improve the network operation
Who launches DDoS attacks and why?
A man from Utah was sentenced to 27 months in jail because he carried out a DDoS attack on Sony’s PlayStation, Microsoft Xbox, Nintendo, Valve Stream, and other platforms. Austin Thompson was the first to start a trend in 2013. He launched DDoS attacks on online gaming platforms, and his reasons for carrying out the attack were to “spoil everyone’s holidays.”
That DDoS attack was super successful because it happened at a time when very few people would put in measures to stop DDoS attacks. His attacks caused most of the biggest online gaming platforms to go offline, which resulted in massive revenue loss for them.
Other hacking groups, such as Lizard Squad, started their attacks as well, which caused the FBI to act. Lately, denial of service attacks have grown too sophisticated to counter anti-DDoS systems — anyone can now develop a DDoS system or hire people who can carry out these attacks. There are botnets on the market that can be bought and used for a DDoS attack.
Moreover, a DDoS attack can be carried out to give a competitor an edge over others or carried out for ransom. Sometimes, cybercriminals initiate it for fun or fame as well. Other times, the reason for a DDoS attack may be to restrict access to specific content.
Who is at most risk of a DDoS attack?
Hackers often target larger corporations, business websites and services, gaming platforms, and Government portals. Such attacks could shut down a web service and cost millions in lost revenues. Personal websites are the least recipients of DDoS attacks.
That said, having a mitigating measure against such attacks in place is extremely important, irrespective of the business size/type.
Developing a denial of service response plan
Every organization should carry out a thorough security assessment and develop a comprehensive DDoS prevention plan.
A large organization would require a complex infrastructure with many DDoS experts, while smaller organizations would require less.
There is usually no time to think (at least not too much) when a DDoS attack occurs. DDoS attack restoration steps must be defined in advance, and a prompt reaction is necessary to avoid severe impacts.
A DDoS incident response plan is highly critical in building a comprehensive defense mechanism. DDoS response plans can get quite exhaustive depending on the kind of infrastructure you need to build.
In most cases, the first step you take when a DDoS attack happens would play a significant role in determining when and how it would end.
Make sure the entire technical team is aware of their responsibilities. Also, ensure that your data center is adequately prepared. That way, you can save your organization from financial loss, months of recovery, and the attack’s impacts can be significantly minimized.
Here are the key elements organizations need to have in place as their denial of service response plan:
- System Checklist: Organizations should develop a full list of assets that would help them identify threats, provide filtering tools, software-level protection, and hardware systems.
- Form Response team: You should define responsibilities for key technical members to ensure that there is an organized reaction in the event of a DDoS attack.
- Define escalation procedure and notification: Your technical team members must know whom to contact in the event of an attack. They should also know whom to escalate to should they encounter a problem they can’t solve independently.
- Develop a communication strategy: Companies should also develop a communication strategy and have a list of internal and external contacts in an attack. Have another means of communicating with your customers, your partner, your service providers, and other security vendors.
How to tell if your computer has been enlisted into a botnet (and what to do)
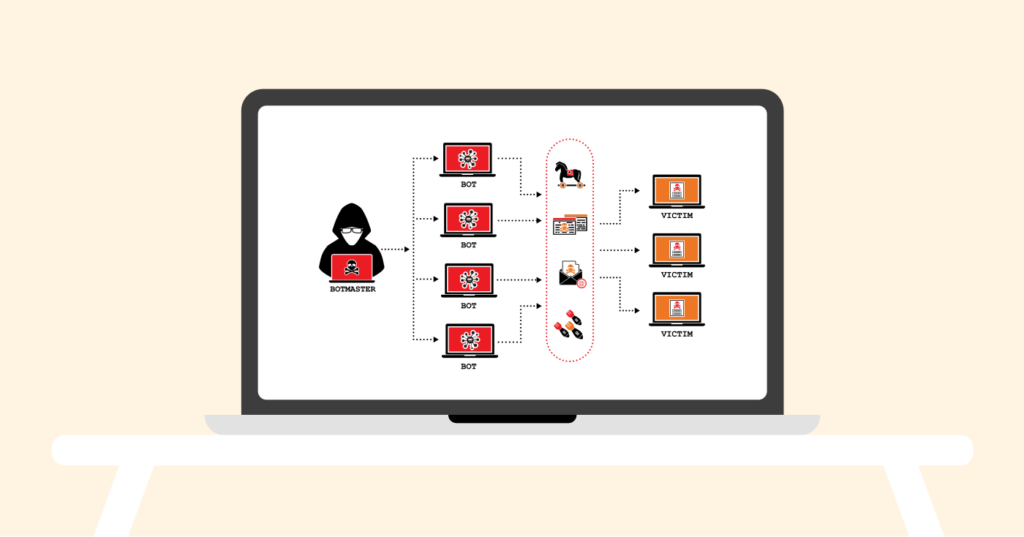
Botnets are a network of cyber robots developed by hackers to commit a crime. A botnet is one of the biggest threats to cybersecurity because it is used to launch a DDoS attack.
They are rapidly growing in popularity among cybercriminals because of their tremendous ability to infiltrate various types of internet-connected devices. Cybercriminals who control botnets and use them to commit crimes are known as Botmasters.
Did you know that individuals can be enlisted into a botnet through their computer without their notice? And guess what, not only can your device then be used for DDoS attacks, but cybercriminals can also use it to send spam and steal data.

There are various signs to look out for, and you should act fast once you notice irregular activities in your systems. Here are the signs to look out for:
- Longer load times
- Frequent crashes
- Slower system
- Unknown error messages
What to do about it
It’s best to take swift action if your computer starts behaving abnormally. You should install and run a trustworthy antivirus application alongside a quality spyware removal tool to check for viruses and malware.
Running a full malware scan on your system can detect if there is a botnet on your system or not. If the antivirus is strong enough, it would be able to eliminate botnets and other malware on your system.
Also, remember to be very careful about attachments, even the ones that come with emails. Only download an attachment if you know and trust the source. Downloading attachments can install phishing scripts on your system without notice.
Are DDoS attacks illegal?

DDoS attacks are illegal worldwide, and you can be sentenced to prison if you carry out a DDoS attack or make a supply.
It is unlawful to intentionally obstruct the free flow of the network or prevent/hinder access to any data. This makes DDoS attacks a criminal act.
Cybercrime is a severe issue, and offenders are prosecuted.
Such a crime can result in a significant prison sentence, paying a penalty fee, having your computer taken away from you, and having a criminal record.
