Has Apple.com been breached? A actor on the dark web claims a data breach on Apple. The claim came from a post by the “303” profile name on an underground dark forum site.
Nature of the data breach claim
The threat actors announced the data breach claim on DarkForums, just as they do with most breaches. The 303 actor posted on their page the following:
DarkForums, the platform 303 actor used to broke the news is a popular the dark forum. The attacker also attached code snippets and alleged “samples” representing JSON data structures, supposedly taken from internal AWS Backup APIs, along with references to compiled Java files. However, there’s no tangible evidence to suggest Apple-exclusive content.
Additionally, the thread includes tags for some well-known groups like @KaruHunters, @UNIT_PEGASUS, and @NodeSillent; all meant to boost the claim’s credibility and visibility.
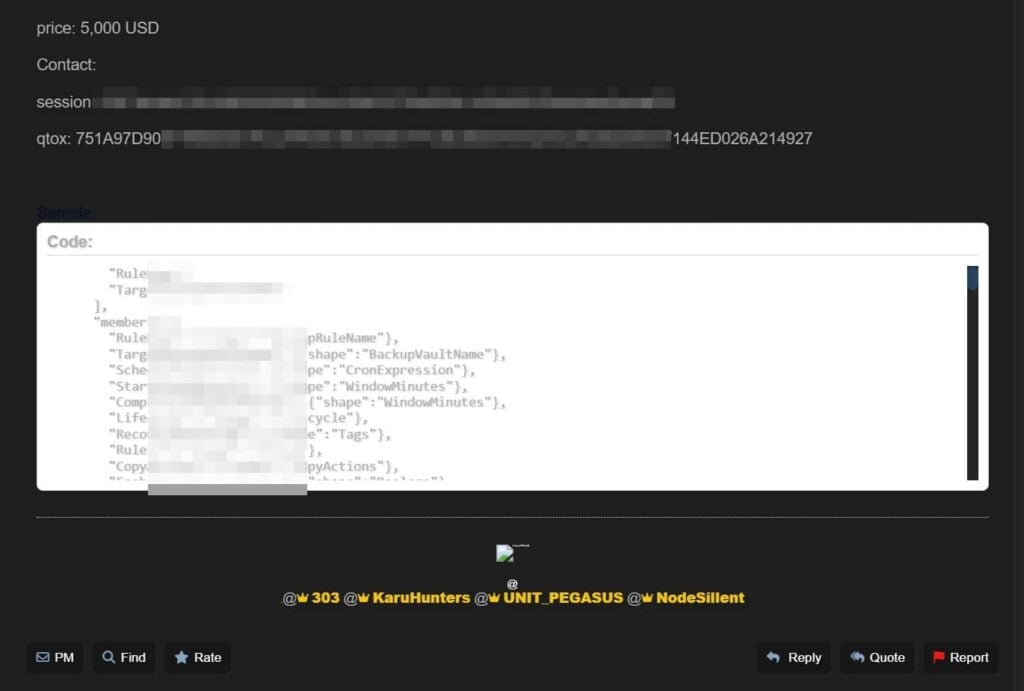
Data for sale
The 303 actor has put up the alleged stolen data package for sale on the underground portion of the internet. The price is $5,000, and public contact is through session and qtox.
Interestingly, there are no verified previews and visible samples are all compatible with the public AWS documentation without unique Apple elements.
The posted samples perfectly match the public structures listed in the AWS Backup documentation, which is freely accessible online, meaning they cannot be uniquely tied to Apple’s systems.
Moreover, the fact that the 303 actor is tagging other cybercriminal groups as well as the tone of the claim announcement suggest a reputation-building strategy.
DarkForums is one of the leading dark web discussion boards for vulnerabilities, data, and other cybercriminal services. It has both a clearnet domain and also a hidden service (onion address). As per our research, the forum, in reality, offers visibility to the established and emerging online attackers.
Apple Inc. Overview
Apple Inc. is one of the world’s largest multinational manufacturers of software, hardware, and digital services (we all know that). Last year, it had revenue of about $391 billion – a new all-time record for Apple. Steve Jobs-founded company’s value exceeds $2 trillion, no wonder why it one of the most influential and recognizable technology brands globally.
The company has an active user base of more than 2.3 billion, a vast worldwide use of iPhones and other Apple products. In 2024, Apple sold 232 million iPhones, 52 million iPads, and 22 million Mac computers, demonstrating the immense scale of its hardware footprint. The company’s technology infrastructure is mainly based on spearheading cloud providers (such as Amazon Web Services (AWS and Google Cloud), supplemented by its dedicated facilities.
People regard Apple as the benchmark for data security and protection, even though cybercriminals constantly target it with attacks. The company invests heavily in a multi-layered security architecture that encompasses hardware, system, and app security (all designed to safeguard its massive user base).
Assessing the credibility – Our take on the news
We went ahead and dug deeper for investigation purposes. Actor 303 is a popular identity on the DarkForums from the constant previous compromise announcements. It also has reputation-building activities on the dark web, which include its active participation in the prominent community threads and discussions.
Cybercriminals usually use the logo of the targeted organization instead of a third-party vendor involved in an alleged breach. Experts should treat this Apple data breach claim as a case to monitor. Why? We hear you ask. That’s because no technical evidence directly links it to Apple or indicates any significant impact on its ecosystem.
Moreover, at the time of writing, there is nothing to affirm the authenticity of the claims, given that Apple hasn’t responded or given any official statement regarding the breach claims. This pattern of unverified claims is common. A similar incident occurred in June 2024 when a notorious hacker claimed a breach, but analysis revealed the leak only contained internal tool configurations, not core user data.
Security experts consistently advise treating such claims with high skepticism (especially the ones that are made on dark web and not reported by a trusted clearnet publisher) until verified by official channels. The lack of Apple-exclusive content in the samples and the use of generic AWS structures point to a potential hoax designed to garner attention rather than a genuine security incident. Therefore, it’s advisable to be vigilant and wait for any subsequent publications or developments.
For all users, this incident serves as a critical reminder to follow essential cybersecurity practices: enable two-factor authentication, use strong and unique passwords, and keep all software updated (to ensure you have the latest security patches). For a complete list of essential security practices, see our detailed guide here.
