Cybersecurity researchers from Trend Micro, Echo Duan, and Jesse Chan have detected many RCE vulnerabilities in the famous Android application, SHAREit.
Remote Code Execution (RCE) bugs can let cyber attackers run malicious codes to extract the sensitive information of users if injected into a device.
According to the report published by researchers, the SHAREit app’s authorities are aware of the vulnerabilities, but the developers are yet to fix the problem as of Feb 21, 2021. The researchers gave SHAREit three months to fix it before making their report public.
SHAREit is an infamous application that lets users share their files among multiple devices at a swift transmission speed. The China-based application was among the top ten most downloaded apps in 2019. The content-sharing app has more than 1.8 billion active users across 200 countries.
Moreover, the application also presents its users with an impressive media player that lets them enjoy movies, videos, and music. The same SHAREit media player works for pictures, too.
It is also worth noting that such vulnerabilities are not present on the application’s iOS version, where there is an entirely different coding structure.
Severe vulnerabilities found in SHAREit
According to the researchers, the absence of restriction coding in the application’s code is the leading cause of these vulnerabilities.
Because of this, any app with malicious codes or a hacker can seize SHAREit core features to run custom code on the target’s device via MITM (man-in-the-middle) network assault. The attackers can then overwrite the applications’ local files or install irrelevant applications without the user knowing about the process.
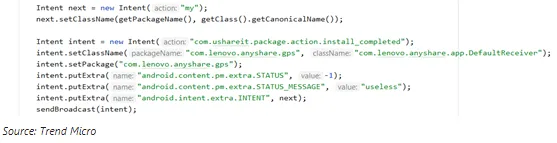
The researchers have also created the PoC (proof of concept) and shared it in the report to help SHAREit users take precautionary steps immediately.
Furthermore, SHAREit is also exposed to custom-coded vdex/odex files that can make malicious code events run on the target device. It also has a crafted link-installation feature that can let the attackers install malware on the targeted device.
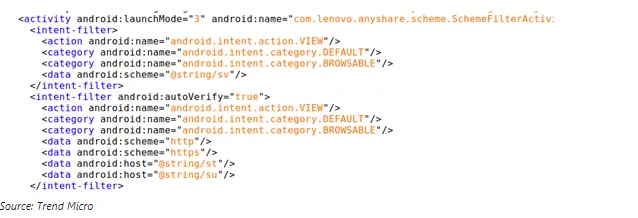
The researchers further revealed that the application is also ensuing risky practices. For instance, they are fetching Android Packages (APK) files via URLs that only use the HTTP protocols and sources that are even outside of the Android Play Store.
To conclude, the famous file-sharing application seems unprotected and contains several flaws. And the worst thing is, most of those flaws are almost impossible for the victims to detect.
If you are a SHAREit user, the PrivacySavvy security team would suggest you either uninstall the application or ensure that you have strengthened your Android security at the very best. Furthermore, researchers revealed that they have also shared their findings with Google. The tech giant is yet to take action against the application.
Because of Google Play’s open format, Android application vulnerabilities have become an issue for Google Play in recent years. That is something that the tech giant has acknowledged and keeps working on. Still, security experts affirm it needs to move faster in this regard.

