A recent Borat Remote Access Trojan ‘RAT’ possesses enormous potential for high destructive abilities. Besides the usual remote accessing capacities, RAT also displays the functions of spyware and ransomware that represent triple threats.
Cybersecurity researchers Cyble.com revealed that cybercriminals could purchase Borat RAT through underground forums. The malware earned its name from the adopted character of the famous comedian Sacha Baron Cohen. The Trojan uses a centralized dashboard with feature modules, a server certificate, and a builder.
What Borat RAT malware does
The design of Borat RAT makes it capable of performing many destructive activities. For example, it could serve as a keylogger, a ransomware component that could encrypt and decrypt, or a means for users to fix up personal ransom notes. Additionally, RAT could be a selective feature for distributed denial-of-service (DDoS) with the capacity to interrupt the normal flow and operations of targeted networks and servers.
As the name implies, RAT displays numerous features pertaining to its triple threats. The performances cut across the combination of the malware’s remote access, spyware, and ransomware. It affects browsers like Chrome and Microsoft Edge. Also, the malware could invade browser information like browser histories, cookies, favorites, bookmarks, and account details. It could also steal Discord tokens.
RAT can trigger an audio recording and access webcam footage by compromising a device’s microphone. Also, the malware can carry some remotely controlled functions like prompting screen capture, hijacking a keyboard or mouse, deleting and stealing system files, and altering system settings.
Furthermore, Borat RAT could invade and capture different system data, such as the operating system information. Once it completes its operations, it can transfer the information to the command-and-control (‘C2’) server, controlled by an attacker.
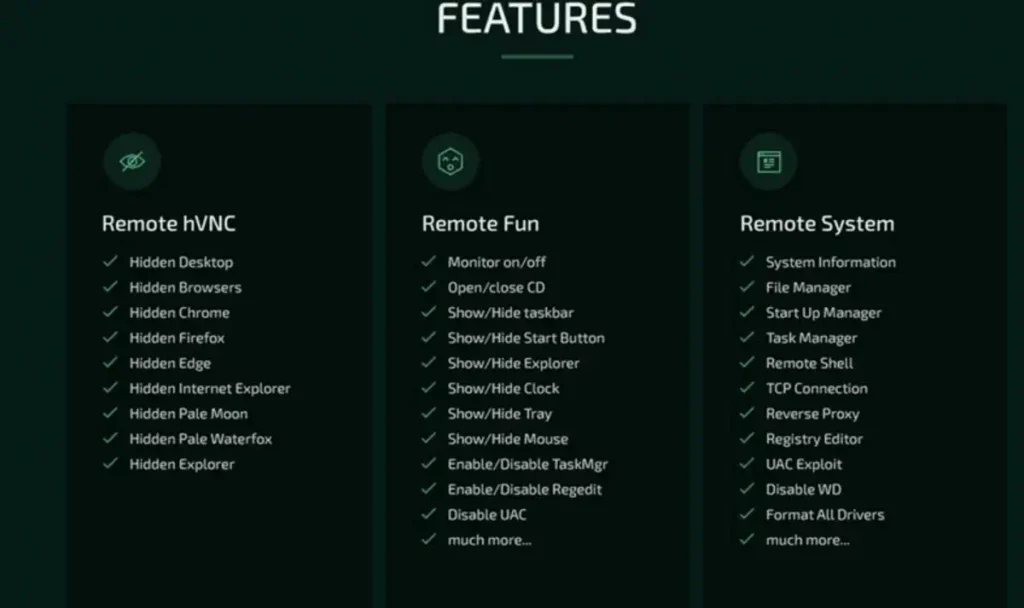
There are still other functions that Borat RAT could carry out. For example, the malware could dish out colossal disturbance to its victims as we see things. Through its odious operations, it can play audio on a system without authorization or swap the mouse buttons on computer systems to distort the normal system functions. Also, the malware can freeze the operation of the mouse and hide or show the desktop and taskbar of systems. Moreover, it can turn off the monitor, disrupt systems’ webcam lights, and cause other malfunctions in the system and programmable devices.
Based on its triple malicious operations of remote access, spyware, and ransomware, the Borat RAT poses considerable threats to any system it invades. Therefore, there is every need for close and daily surveillance of the malware to understudy the possible outturns of future events.
Why internet users should be more Privacy Savvy
With the increasing rate of internet activities, hackers rely on tools such as malware to perpetrate cybercrimes. These are different forms of malicious software created to exploit, harm, or access programmable networks and devices. They can extract data of all types ranging from financial to personal to medical and others.
Now, cybercriminals can invade many private and public records with the help of malware. The criminals have several reasons for using malicious software for their activities. They could release denial-of-service attacks on other networks by taking over the control of several computer systems. Also, they could corrupt computers to use them in mining cryptocurrencies such as Bitcoin.
