Google has confirmed a recent data breach affecting Google Fi phone network customers. It is likely related to a security incident at T-Mobile, where hackers stole millions of customers’ information.
Google Fi operates as a Mobile Virtual Network Operator (MVNO), which acts like a regular cell network provider. MVNOs are more budget-friendly phone plans than typical phone plans. But they don’t have their own network infrastructure.
For example, Google Fi relies on T-Mobile’s infrastructure. And since it was compromised, Google Fi was also impacted. However, it’s worth noting that Google Fi is not directly related to Google’s mobile operating system, Android.
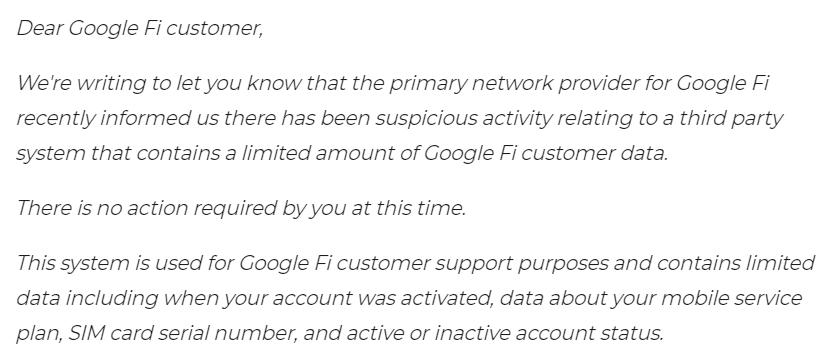
In an email sent to Google Fi subscribers, the tech giant told affected customers that Google Fi’s primary network provider suspected suspicious activity with a third-party support system. However, it affected only a limited amount of data. Below is a snippet from the email that Google sent to Fi subscribers.
The T-Mobile breach incident
The timing of this revelation and the fact that Google Fi uses U.S. Cellular and T-Mobile for network service indicate a connection to the T-Mobile hack. The incident came to light on January 19, when hackers stole 37 million customers’ personal information, such as dates of birth, billing addresses, and other T-Mobile account details. It was the eighth hacking incident at T-Mobile since 2018.
According to Google, hackers may have obtained limited customer information such as account status, phone numbers, SIM card serial numbers, and information about the customers’ mobile service plans from the breach.
Yet, they didn’t take data like payment card information, PINs, passwords, calls, or text messages. Unfortunately, the extent of the breach is unclear as Google doesn’t reveal the number of cell subscribers it has.
Most of the emails sent to customers claimed that no action was necessary. However, one Google Fi customer on Reddit reported the incident of their phone number getting hijacked, also known as SIM swapping.
Apparently, the hackers controlled their number for nearly two hours and could have used it to send and receive texts and calls. Usually, hackers use this method to access a victim’s other online accounts that use the same phone number.
PrivacySavvy contacted Google to ask whether the Google Fi incident is related to the recent T-Mobile breach, but we are yet to receive their response.
Also, representatives from USCellular and T-Mobile did not respond to requests for comment. However, the Google Fi incident highlights the importance of companies working together to enhance their security measures and prevent future breaches from occurring.
Google said it is collaborating with an unnamed network provider to determine the cause of the breach and implement measures to safeguard the data stored in third-party systems. It also plans to notify everyone affected. Additionally, the company reassured customers that there was no unauthorized access to Google’s internal systems or any systems under its control.
Past data breach incidents
Google infrastructure has suffered significant breaches in the past, although they have been rare.
For instance, a breach was blamed on Chinese hackers in 2013. In 2018, the information of 500,000 Google Plus users was exposed, leading to the eventual shutdown of the failed Facebook rival. In addition, Google has a reputation for offering “bug bounties” (large amounts of money) to researchers who discover security flaws in its products. That’s an excellent thing.
Let’s hope Google doesn’t downplay the significance of this latest breach because controlling an individual’s phone number is risky. For example, malicious actors can mimic the affected user and target others with phishing emails and other scams.
Scammers can tailor these scams to specific targets, and access to your personal information can help hackers craft even more effective phishing messages. Furthermore, if the affected customers were also a part of the recent T-Mobile data breach, cybercriminals would have a wealth of information to utilize in such attacks.
