The ESET researchers have warned against a new malware working as a modular backdoor. It gives intruders access to the sensitive information of Point-of-Sale (PoS) systems. The malicious software is dubbed ModPipe.
Primarily, cybersecurity researchers have warned both the hotel and hospital sectors to be wary of ModPipe.
The report claims the backdoor “ModPipe” targets Oracle MICROS Restaurant Enterprise Series (RES) 3700 PoS systems.
RES 3700 is a popular hotel and hospital management system used in the United States. This system helps in maintaining PoS, inventory, and labor management.
Basic components of ModPipe
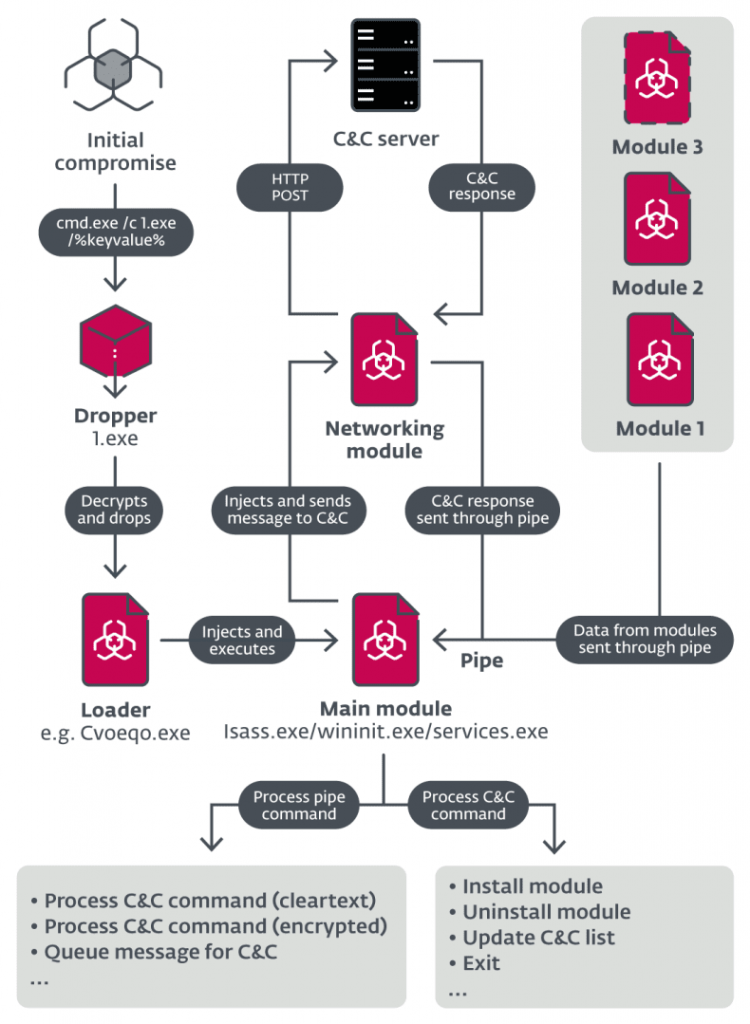
The ESET research team identified these backdoor modules’ existence and discovered the malware’s ‘basic units.’ The necessary components perform in a sequential pattern;
- The initial dropper is consist of two famous binaries, 32-bit and 64-bit.
- Then comes the persistent loader, which loads the main module performing the core function.
- The networking module helps communicate with C&C.
- At last, downloadable modules add specified functionality to the backdoor, such as stealing the database passwords.
What makes this malware dangerous?
The researchers were able to track numerous downloadable modules. GetMicInfo, the most threatening module, helps steal database passwords, settings, and other crucial data. The algorithm decrypts the data from Windows registry values.
The wild downloadable modules that comprise custom algorithms can adjust accordingly. They slide into the PoS database system leaking the information. That’s what makes ModPipe a dangerous malware.
When the ModPipe malware breaches the PoS database, it can access status tables, system configuration, and transaction history.
Certain modules are not traced yet. Thus far, the researchers have discovered GetMicInfo, ModScan, and ProcList. While the remaining four are still to be identified.
Despite all this danger, the RES 3700 system’s encryption standards make it secure enough to hide the card information. ESET’s researchers believe that ModPipe, in its elemental state, is not that strong to access credit card numbers or expiry dates.
The researchers noted,
“The objective of the attacker remains unclear.”
The most important information on the PoS system is the card data, and to steal that; the attacker needs to have passphrase that is site-specific.
This process needs to be executed in the module to access such sensitive information. It would then face the Windows Data Protection API (DPAPI), implemented automatically on the targeted system.
The hotel sector hasn’t been targeted with PoS malware for the first time. In June 2016, a swathe of US hotels had fallen prey to PoS malware that reportedly exposed customers’ financial data. The data breach divulged data from tens of thousands of drinks, food, and other transactions.
